Содержание
- 2. Objectives Review of Concepts. What is (are): Information Systems? Information Security? Information Systems Security? Information Assurance?
- 3. Review of Concepts What are Information Systems? Systems that store, transmit, and process information. + What
- 4. Review of Concepts What is Information Assurance? Emphasis on Information Sharing Establishing and controlling trust Authorization
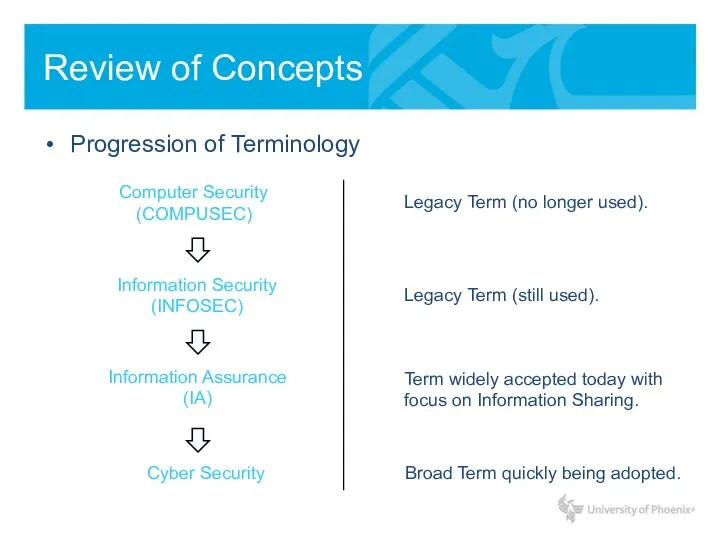
- 5. Review of Concepts Progression of Terminology Computer Security (COMPUSEC) Information Security (INFOSEC) Information Assurance (IA) Cyber
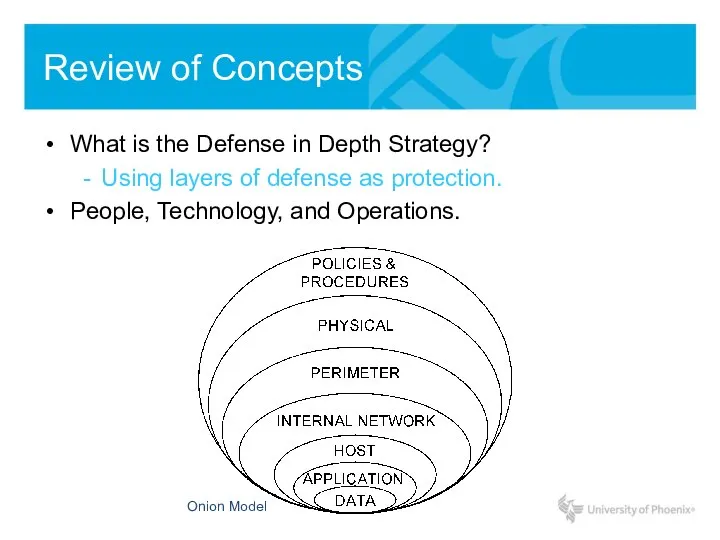
- 6. Review of Concepts What is the Defense in Depth Strategy? Using layers of defense as protection.
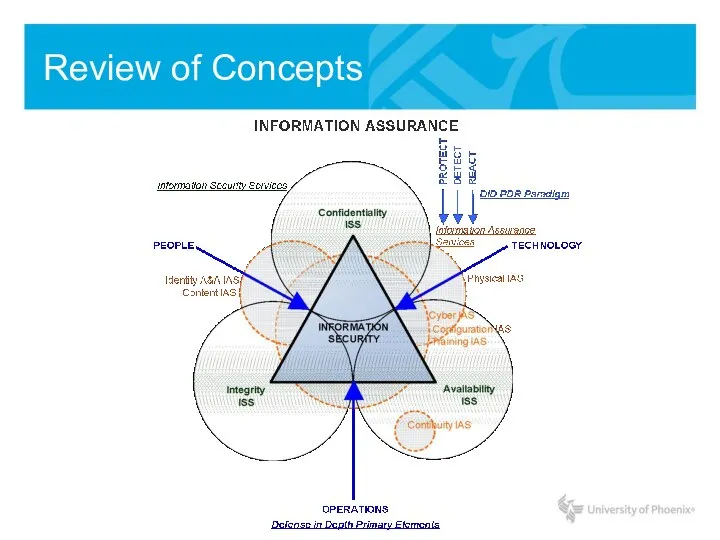
- 7. Review of Concepts
- 8. ISS Management What is a Backup Plan (BP) vs Disaster Recovery Plan (DRP) vs Emergency Response
- 9. Why is this important? Information is valuable. therefore, Information Systems are valuable. etc… Compromise of Information
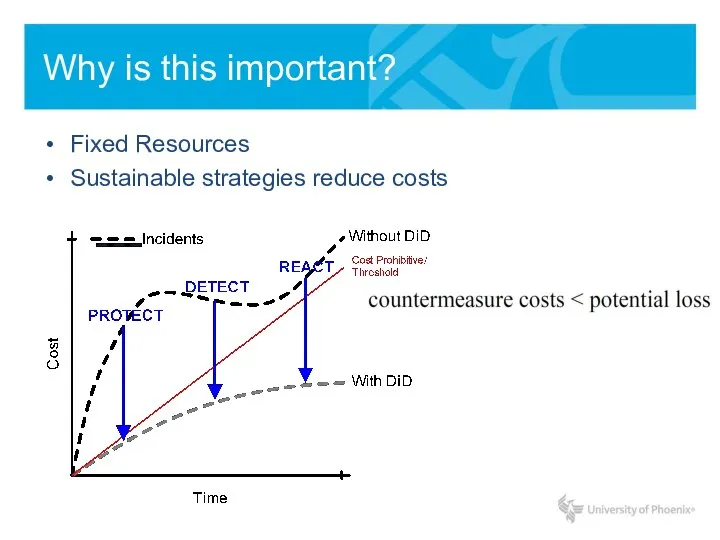
- 10. Why is this important? Fixed Resources Sustainable strategies reduce costs
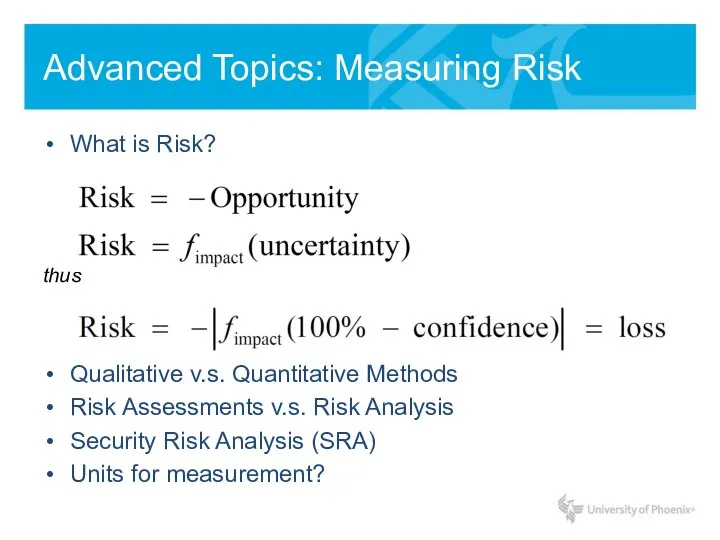
- 11. Advanced Topics: Measuring Risk What is Risk? thus Qualitative v.s. Quantitative Methods Risk Assessments v.s. Risk
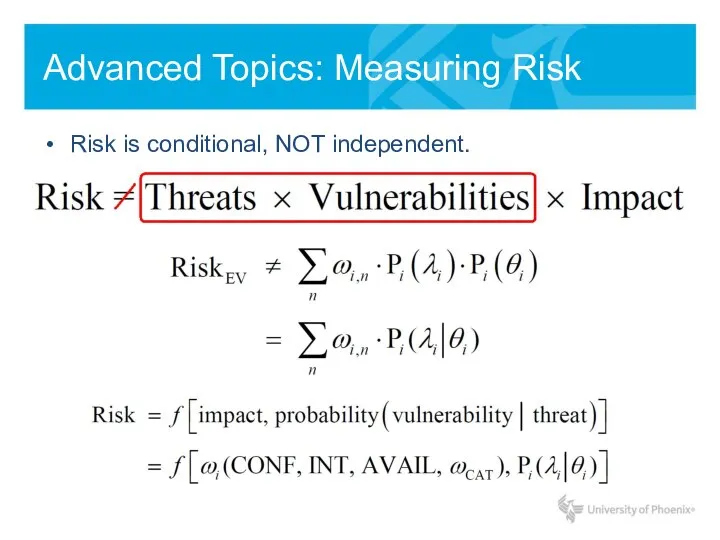
- 12. Advanced Topics: Measuring Risk Risk is conditional, NOT independent.
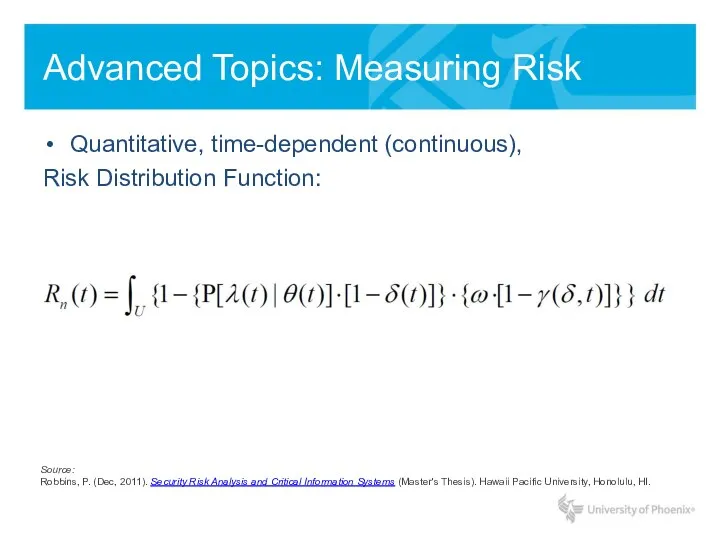
- 13. Advanced Topics: Measuring Risk Quantitative, time-dependent (continuous), Risk Distribution Function: Source: Robbins, P. (Dec, 2011). Security
- 14. Advanced Topics: Measuring Risk Expected Value of Risk = Product of Risks Risk is never zero
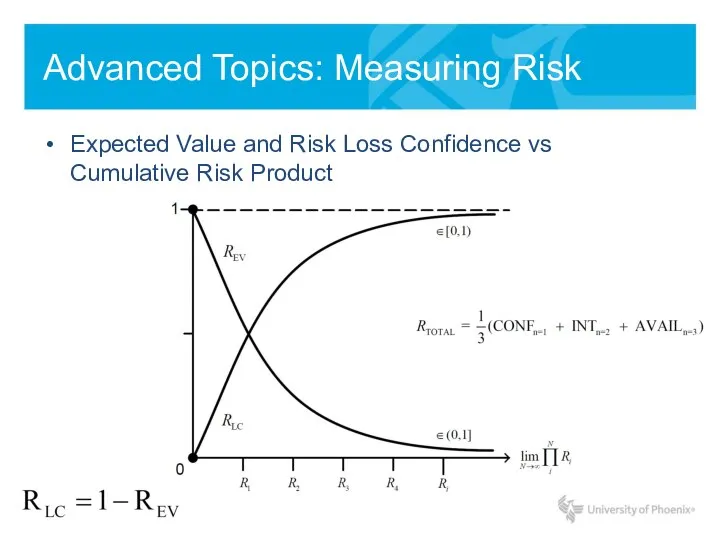
- 15. Advanced Topics: Measuring Risk Expected Value and Risk Loss Confidence vs Cumulative Risk Product
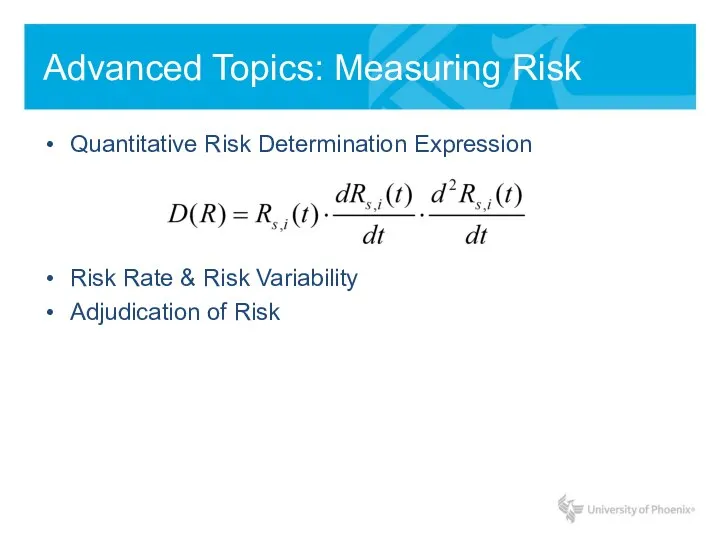
- 16. Advanced Topics: Measuring Risk Quantitative Risk Determination Expression Risk Rate & Risk Variability Adjudication of Risk
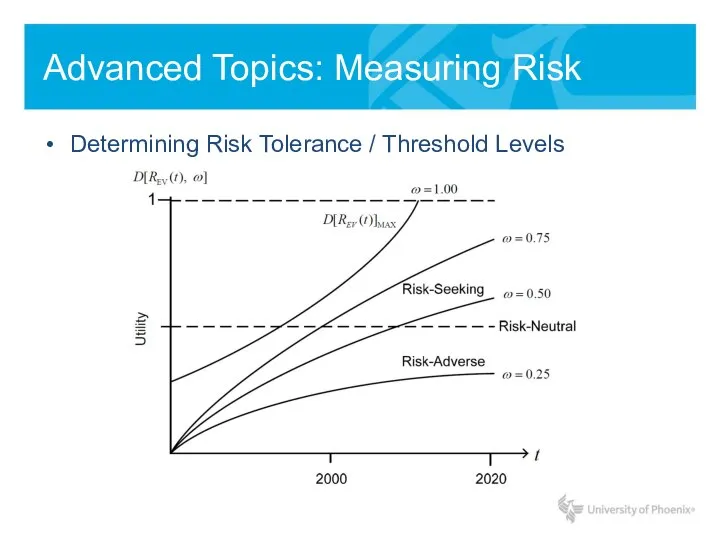
- 17. Advanced Topics: Measuring Risk Determining Risk Tolerance / Threshold Levels
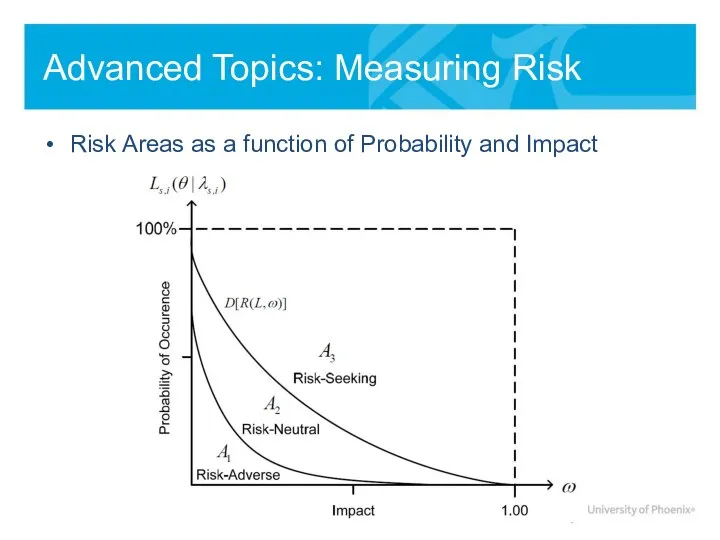
- 18. Advanced Topics: Measuring Risk Risk Areas as a function of Probability and Impact
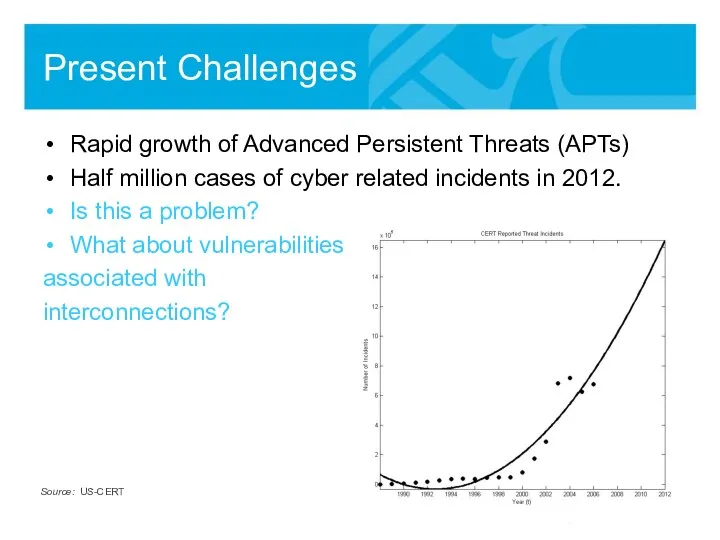
- 19. Present Challenges Rapid growth of Advanced Persistent Threats (APTs) Half million cases of cyber related incidents
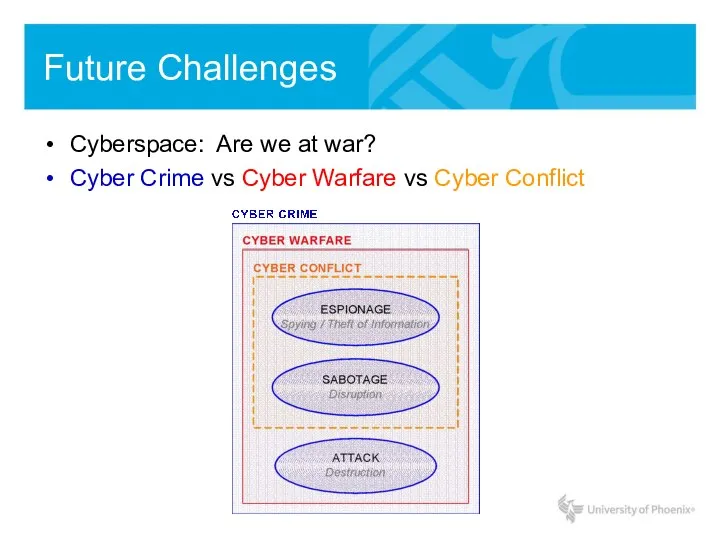
- 20. Future Challenges Cyberspace: Are we at war? Cyber Crime vs Cyber Warfare vs Cyber Conflict
- 22. Скачать презентацию





 Make ridiculous story
Make ridiculous story Assesing speaking
Assesing speaking Rhyming Words
Rhyming Words Pan Cerd English
Pan Cerd English Неопределенные местоимения some, any, no
Неопределенные местоимения some, any, no - Have you ever?
- Have you ever? Fill in the prepositions and click the egg
Fill in the prepositions and click the egg Passive Voice. Wine Production
Passive Voice. Wine Production Reading for pleasure
Reading for pleasure Austria
Austria Present Simple vs Present Continuoun play
Present Simple vs Present Continuoun play Daily Date and Weather Chart
Daily Date and Weather Chart There is. There are
There is. There are Past continuous. Past simple
Past continuous. Past simple Deys of the week
Deys of the week Present Simple
Present Simple I can see
I can see Reading and writing poems and haiku. Lesson 1
Reading and writing poems and haiku. Lesson 1 Where is Teddy?
Where is Teddy? Incorporating Data and Illustrations
Incorporating Data and Illustrations Verb to be 3
Verb to be 3 Тексты на английском языке
Тексты на английском языке Презентация к уроку английского языка "Pancakes day" -
Презентация к уроку английского языка "Pancakes day" - 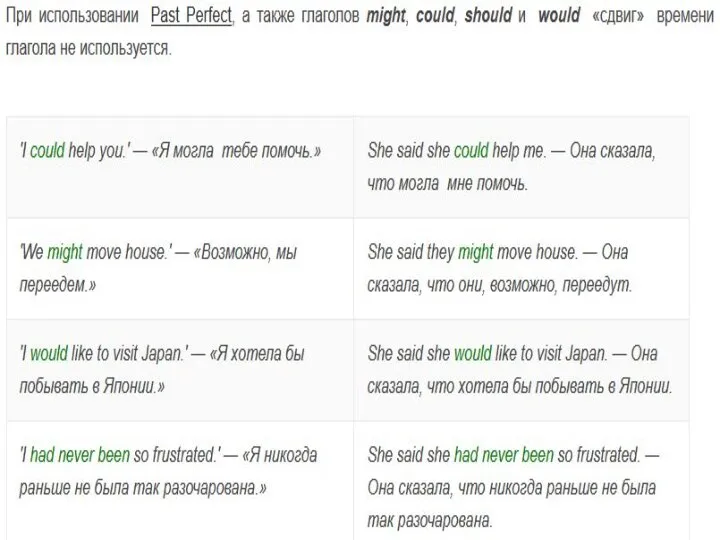 Слова для передачи приказа, просьбы или совета
Слова для передачи приказа, просьбы или совета Take a trip around the Timashevsk. Welkome to our city
Take a trip around the Timashevsk. Welkome to our city Present Continuous (+)
Present Continuous (+) My Picture
My Picture Roblox. Lesson
Roblox. Lesson