Слайд 2Cryptography - data protection method
Derbyshev Lev
RI-270007

Слайд 4Enigma Encryption Machine
This is what the Enigma
machine looks like.
With its help, German

soldiers managed to pass
instructions during
World War II.
Слайд 5Information Problems
As the amount of data increases, the following problems appear:
Data leakage
Data
substitution
Distortion due to technical reasons
Слайд 6Personal data. Who is interested in this?
A lot of people search like

information. Its use may have a different character from the sale of a product to the actions of a criminal character.
Слайд 7One-way encryption
This is an example of how to calculate a unique hash
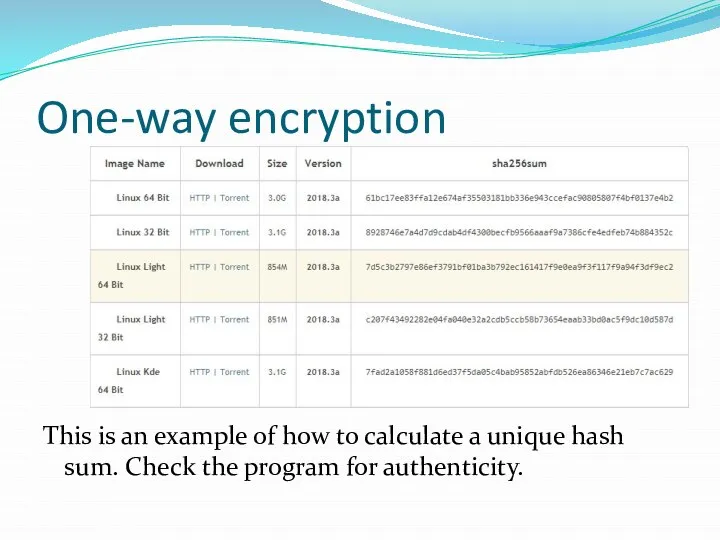
sum. Check the program for authenticity.
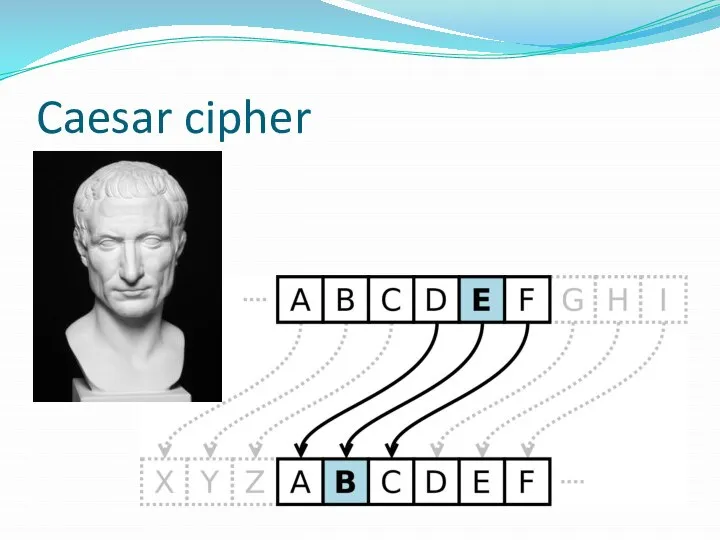
Слайд 8Two-way encryption
This type of encryption can be decrypted by knowing the master

key. It is designed to transmit data securely.






 What time is it
What time is it Articles and headlines. Пояснения к выполнению заданий
Articles and headlines. Пояснения к выполнению заданий Differences and similarities between England and Yakut villages
Differences and similarities between England and Yakut villages Places or stores fun activities games
Places or stores fun activities games Vegetables. English with Mr. Perfection
Vegetables. English with Mr. Perfection What’s the date
What’s the date Number
Number Direct and Indirect Speech
Direct and Indirect Speech Call it a day
Call it a day Past Perfect
Past Perfect My place
My place Use of blood evidence in the investigation of crimes
Use of blood evidence in the investigation of crimes Презентация на тему St. Valentine's Day
Презентация на тему St. Valentine's Day  Clothes. 2 класс
Clothes. 2 класс Slides Carnival
Slides Carnival My Landform Book
My Landform Book Local People of Madagascar
Local People of Madagascar Nearest and dearest. Idioms used to speak about family and relatives
Nearest and dearest. Idioms used to speak about family and relatives Homework Programmation in c Language
Homework Programmation in c Language Colourful house
Colourful house Adj and adverbs
Adj and adverbs An apple a day keeps a doctor away
An apple a day keeps a doctor away Leninsky district
Leninsky district What is in your fridge
What is in your fridge What’s the weather like?
What’s the weather like? The Pyramids of Egypt
The Pyramids of Egypt I will, I wont
I will, I wont Practical Training 2
Practical Training 2