Содержание
- 2. Presentation Content What is Internet? What do we need to protect? Threat Motivation Attack Types Security
- 3. What is Internet? The Internet is a worldwide IP network, that links collection of different networks
- 4. What do we need to protect Data Resources Reputation
- 5. Threat Motivation Spy Joyride Ignorance Score Keeper Revenge Greed Terrorist
- 6. Types of Attacks Passive Active Denial of Services Social Engineering
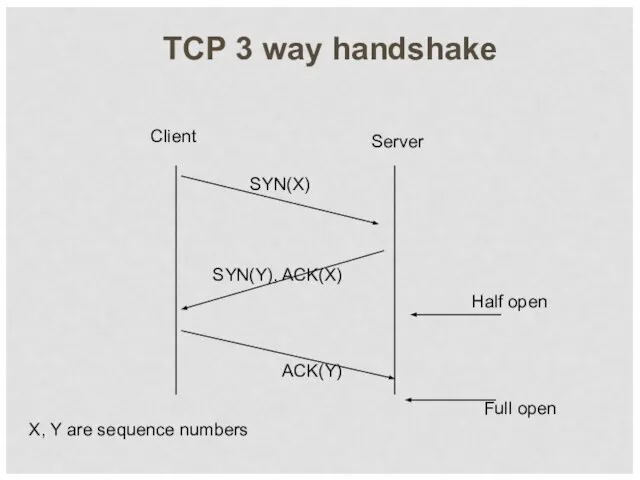
- 7. TCP 3 way handshake Server SYN(X) SYN(Y), ACK(X) ACK(Y) Client X, Y are sequence numbers Half
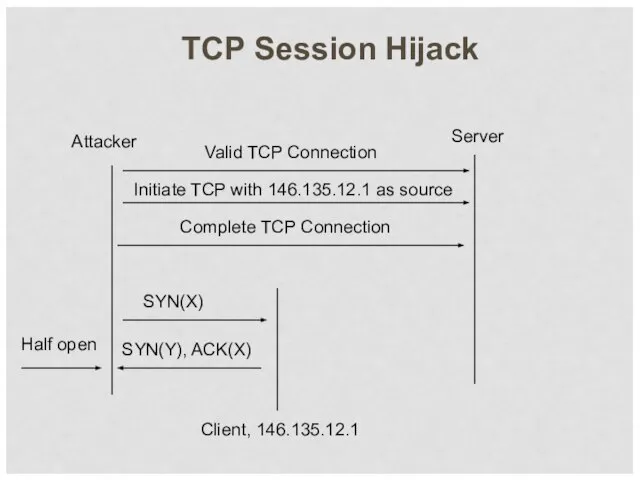
- 8. TCP Session Hijack Server SYN(X) SYN(Y), ACK(X) Attacker Client, 146.135.12.1 Half open Valid TCP Connection Initiate
- 9. Security Objectives Identification Authentication Authorization Access Control Data Integrity Confidentiality Non-repudiation
- 10. Identification Something which uniquely identifies a user and is called UserID. Sometime users can select their
- 11. Authentication The process of verifying the identity of a user Typically based on Something user knows
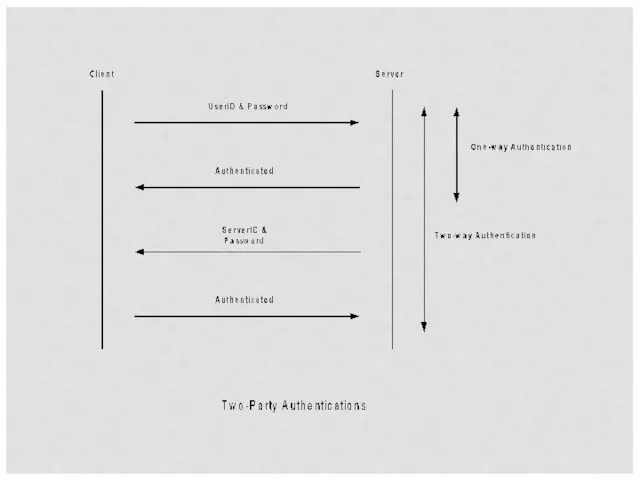
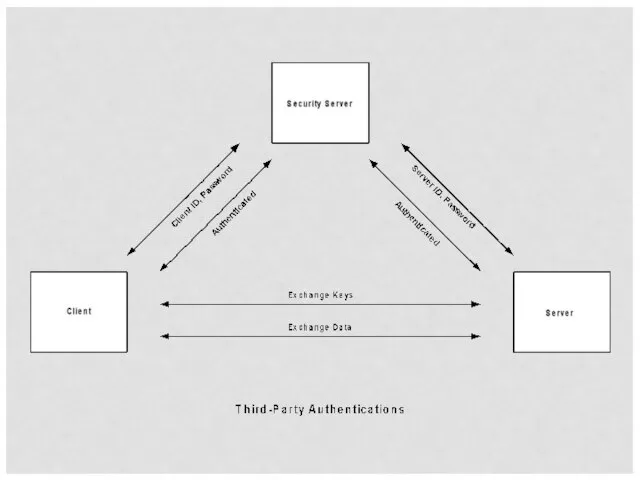
- 12. Authentication Cont. Authentication procedure Two-Party Authentication One-Way Authentication Two-Way Authentication Third-Party Authentication Kerberos X.509 Single Sign
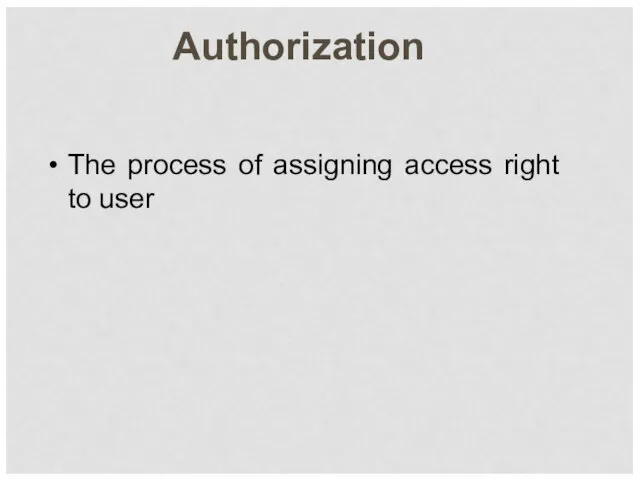
- 15. Authorization The process of assigning access right to user
- 16. Access Control The process of enforcing access right and is based on following three entities Subject
- 17. Access Control Cont. Access Control is divided into two Discretionary Access Control (DAC) The owner of
- 18. Data Integrity. Assurance that the data that arrives is the same as when it was sent.
- 19. Confidentiality Assurance that sensitive information is not visible to an eavesdropper. This is usually achieved using
- 20. Non-repudiation Assurance that any transaction that takes place can subsequently be proved to have taken place.
- 21. Security Mechanisms Web Security Cryptographic techniques Internet Firewalls
- 22. Web Security Basic Authentication Secure Socket Layer (SSL)
- 23. Basic Authentication A simple user ID and password-based authentication scheme, and provides the following: To identify
- 24. SECURE SOCKET LAYER (SSL) Netscape Inc. originally created the SSL protocol, but now it is implemented
- 25. Secure Socket Layer Cont.. The client sends a "hello" message to the Web server, and the
- 26. Cryptographic Techniques Secret Key Algorithm Public Key Algorithm Secure Hash Function Digital Signature Certificate Authority
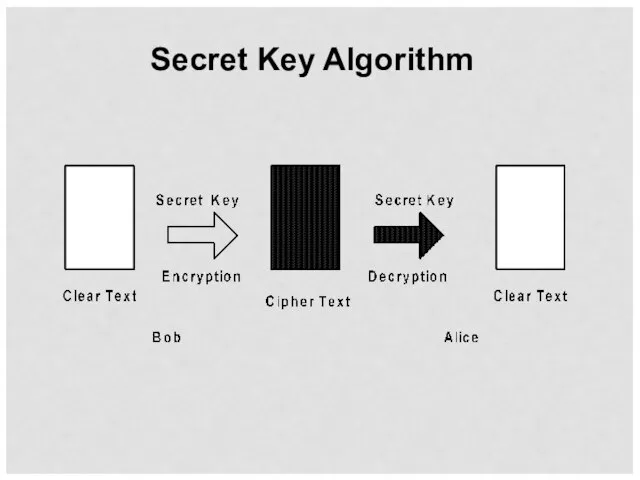
- 27. Secret Key Algorithm
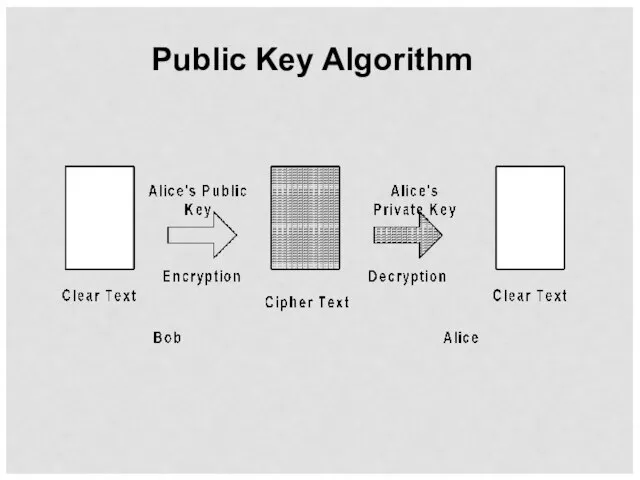
- 28. Public Key Algorithm
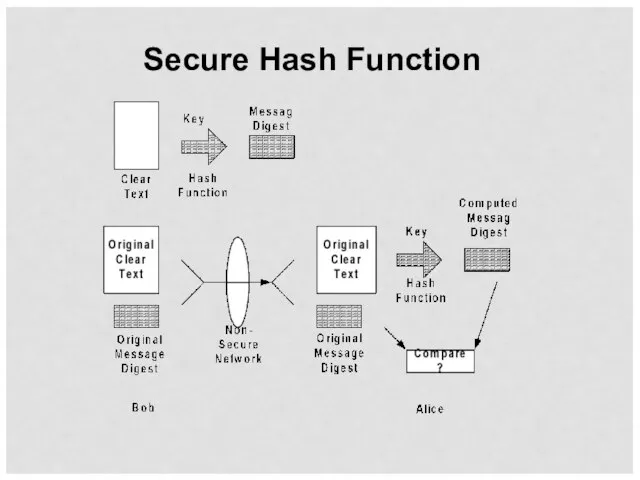
- 29. Secure Hash Function
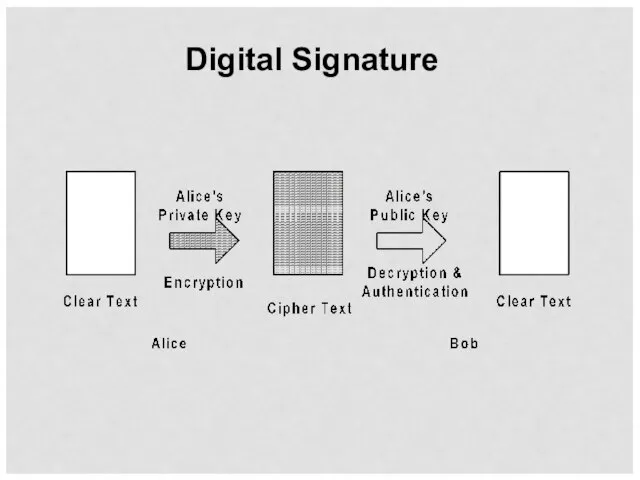
- 30. Digital Signature
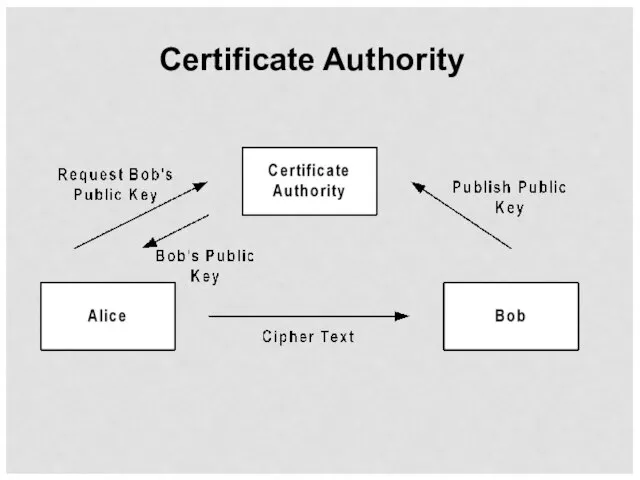
- 31. Certificate Authority
- 32. X.509 Certificate Is a ITU-T Recommendation. Specifies the authentication service for X.500 directories X.500 specifies the
- 33. X.509 Certificate (cont..) X09 certificate consists of the following fields: Version Serial Number Algorithm Identifier Issuer
- 34. X.509 Certificate (Cont..) Version 1 Basic Version 2 Adds unique identifier to prevent reuse of X.500
- 35. X.509 Certificate Revocation List (CRL) Is to prevent fraud and misuse. A certificate may be revoked
- 36. X.509 CRL (cont..) X09 CRL consists of the following fields: Version Serial Number Revocation Date Algorithm
- 37. Internet Firewall A firewall is to control traffic flow between networks. Firewall uses the following techniques:
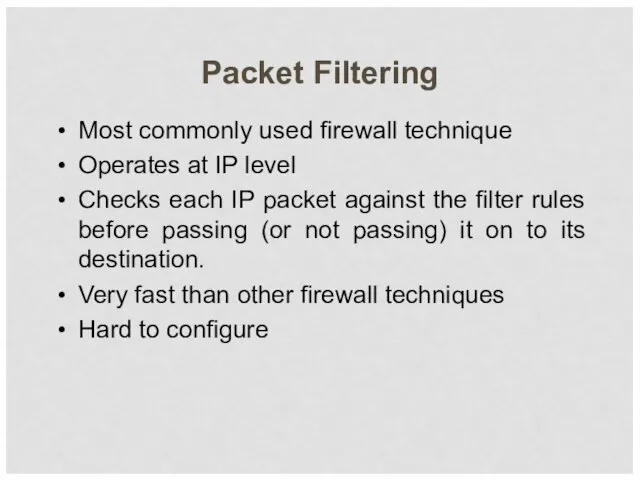
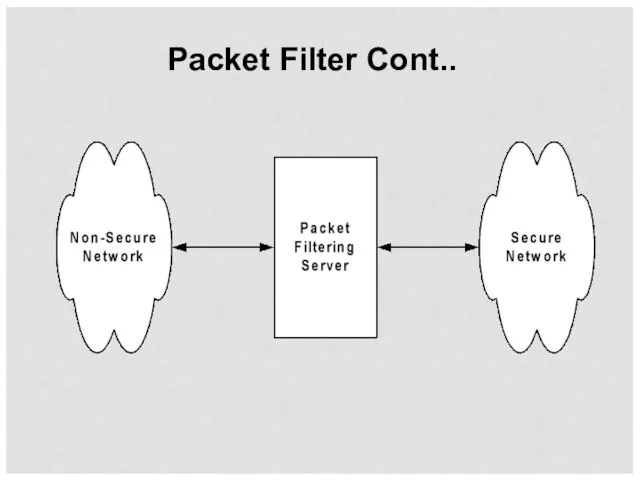
- 38. Packet Filtering Most commonly used firewall technique Operates at IP level Checks each IP packet against
- 39. Packet Filter Cont..
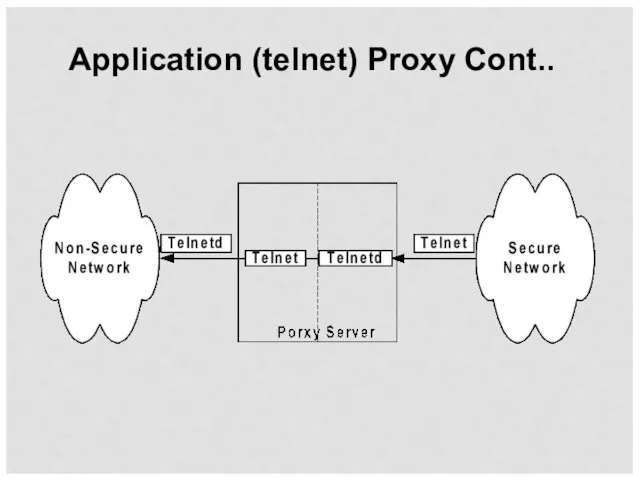
- 40. Application Proxy Application Level Gateway The communication steps are as follows User connects to proxy server
- 41. Application (telnet) Proxy Cont..
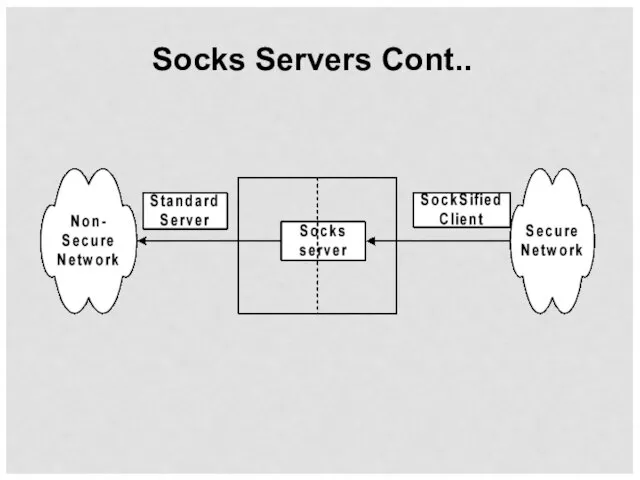
- 42. SOCKS Server Circuit-level gateways Generally for outbound TCP traffic from secure network Client code must be
- 43. Socks Servers Cont..
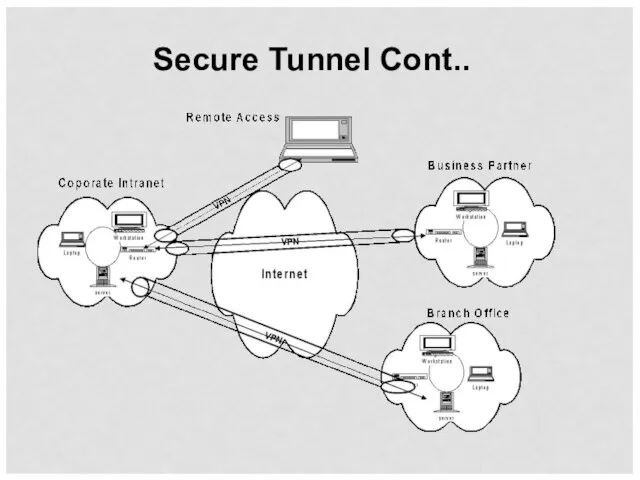
- 44. Secure Tunnel Cont..
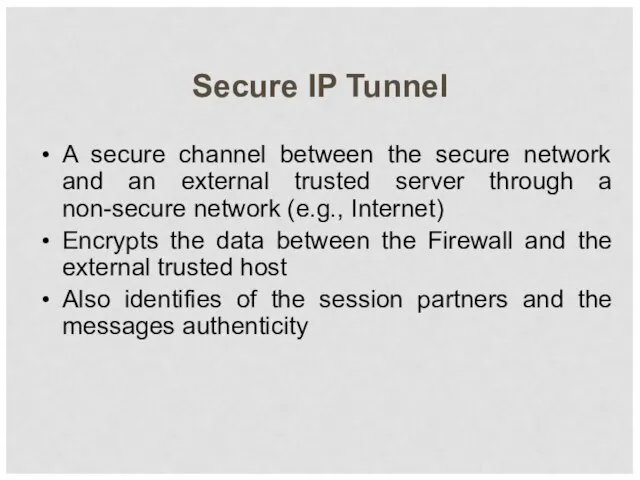
- 45. Secure IP Tunnel A secure channel between the secure network and an external trusted server through
- 46. VPN Solutions IP Security (IPSec) Layer 2 Tunnel Protocol (L2TP) Virtual Circuits Multi Protocol Label Switching
- 47. IPSec Solution IPSec is an Internet standard for ensuring secure private communication over IP networks, and
- 48. Principle of IPSec protocols Authentication Header (AH) Provides data origin authentication, data integrity and replay protection
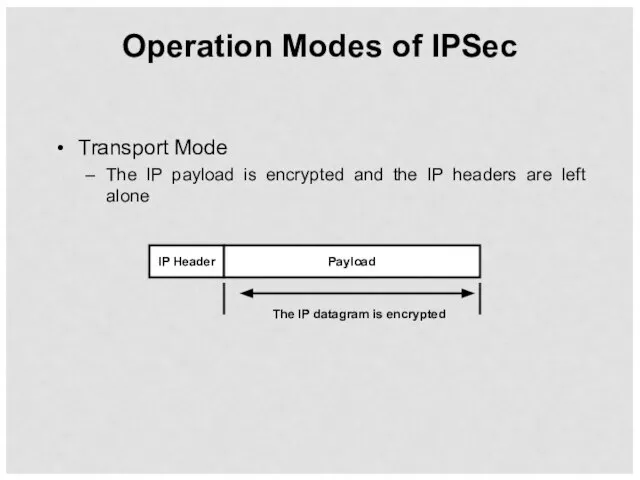
- 49. Operation Modes of IPSec Transport Mode The IP payload is encrypted and the IP headers are
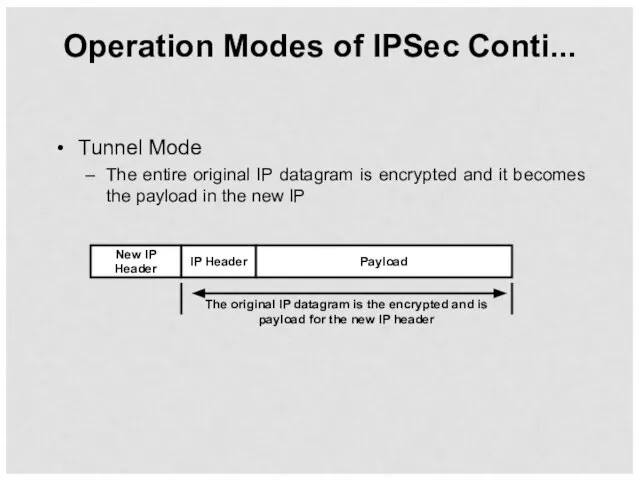
- 50. Operation Modes of IPSec Conti... Tunnel Mode The entire original IP datagram is encrypted and it
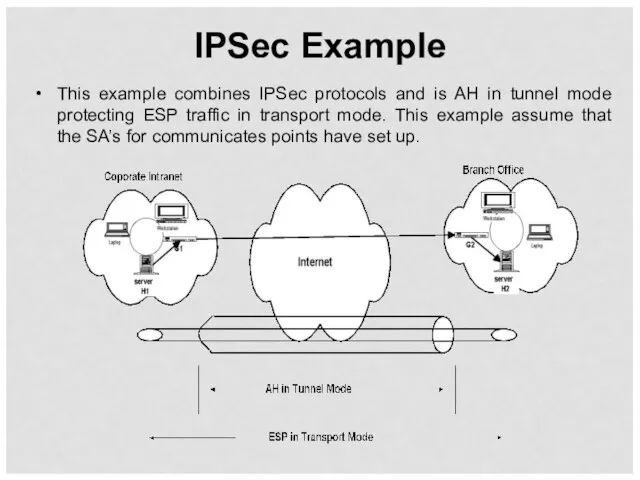
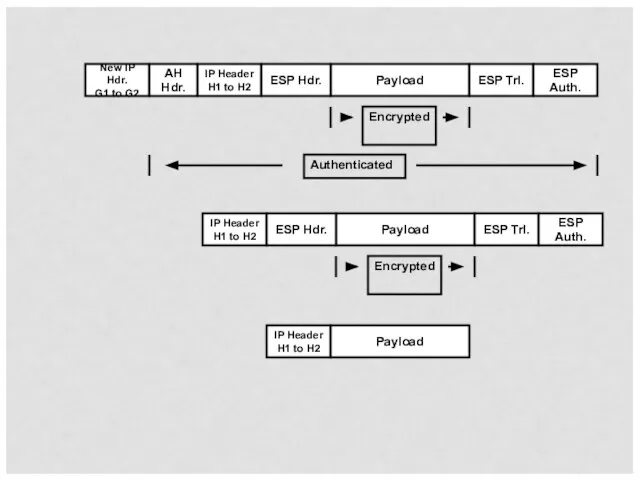
- 51. IPSec Example This example combines IPSec protocols and is AH in tunnel mode protecting ESP traffic
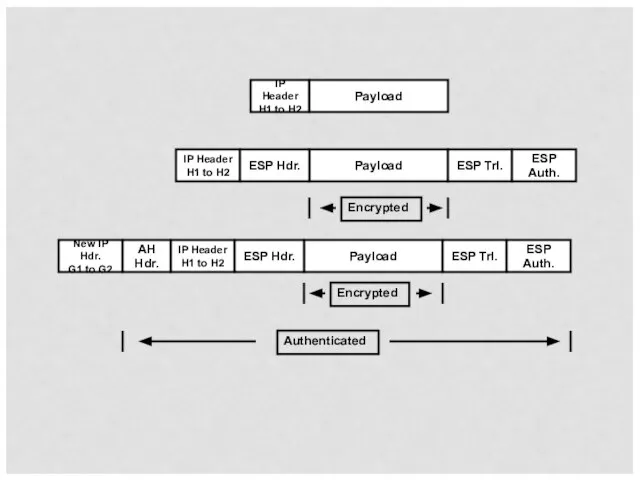
- 52. IP Header H1 to H2 Payload New IP Hdr. G1 to G2 IP Header H1 to
- 53. New IP Hdr. G1 to G2 IP Header H1 to H2 Payload ESP Hdr. ESP Trl.
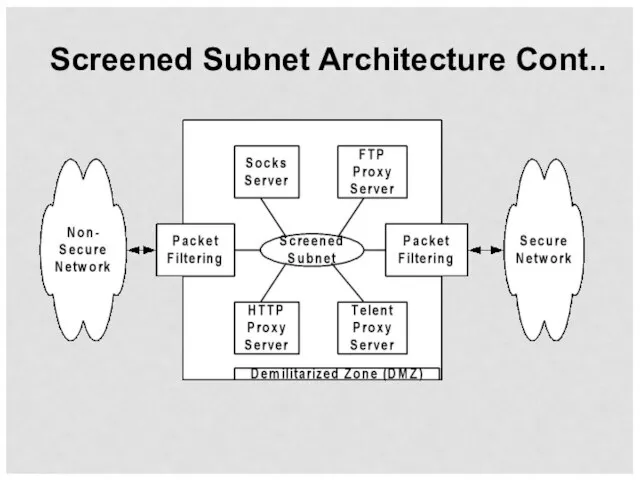
- 54. Screened Subnet Architecture Cont..
- 55. Screened Subnet Architecture The DMZ (perimeter network) is set up between the secure and non-secure networks
- 57. Скачать презентацию































 Чарующие звуки музыки
Чарующие звуки музыки Диены
Диены В каких стилях русского языка чаще всего встречаются речевые ошибки ? Чаще всего речевые ошибки встречаются в разговорном и Чаще в
В каких стилях русского языка чаще всего встречаются речевые ошибки ? Чаще всего речевые ошибки встречаются в разговорном и Чаще в University of my dream
University of my dream Моя будущая профессия
Моя будущая профессия Синдром дефицита внимания и гиперактвиность
Синдром дефицита внимания и гиперактвиность Презентация на тему Приглашение к чтению Е.И. Чрушина и его творчества
Презентация на тему Приглашение к чтению Е.И. Чрушина и его творчества СОВРЕМЕННЫЕ СИСТЕМЫ ЗАЩИТЫ И АВТОМАТИЗАЦИИ НА МНОГОЦЕПНЫХ ЛИНИЯХ ЭЛЕКТРОПЕРЕДАЧИ СВЕРХВЫСОКОГО НАПРЯЖЕНИЯ Янез Законьшек ЗАО «
СОВРЕМЕННЫЕ СИСТЕМЫ ЗАЩИТЫ И АВТОМАТИЗАЦИИ НА МНОГОЦЕПНЫХ ЛИНИЯХ ЭЛЕКТРОПЕРЕДАЧИ СВЕРХВЫСОКОГО НАПРЯЖЕНИЯ Янез Законьшек ЗАО « Санитарно-эпидемиологические требования к условиям и организации обучения в общеобразовательных учреждениях
Санитарно-эпидемиологические требования к условиям и организации обучения в общеобразовательных учреждениях РасширениеMS Visual Studio 2005с использованиемIntel® C++ IDE Automation
РасширениеMS Visual Studio 2005с использованиемIntel® C++ IDE Automation Растения играют большую роль в жизни животных и человека кислород пища лекарство убежище ткани древесина.
Растения играют большую роль в жизни животных и человека кислород пища лекарство убежище ткани древесина. Переработка попутного нефтяного газа – эффективное использование невозобновляемого источника природных ресурсов РФ
Переработка попутного нефтяного газа – эффективное использование невозобновляемого источника природных ресурсов РФ Банная станция
Банная станция Утилизация теплоты
Утилизация теплоты Бюджетное устройство и бюджетная система
Бюджетное устройство и бюджетная система Глаза животных 3 класс
Глаза животных 3 класс Термическая обработка
Термическая обработка Деловой стиль одежды
Деловой стиль одежды Феварин (флувоксамин) в амбулаторном лечении алкогольной зависимости, осложненной психическими расстройствами
Феварин (флувоксамин) в амбулаторном лечении алкогольной зависимости, осложненной психическими расстройствами Zaadachi_3_klass
Zaadachi_3_klass Охрана атмосферы города от газовых выбросов промышленных предприятий
Охрана атмосферы города от газовых выбросов промышленных предприятий Презентация на тему Косыночные повязки
Презентация на тему Косыночные повязки  Еврейская культура. Еврейские праздники
Еврейская культура. Еврейские праздники Портрет
Портрет ПЛАТФОРМА ВАШЕГО УСПЕХА
ПЛАТФОРМА ВАШЕГО УСПЕХА Процессы приготовления, подготовки к реализации и презентации холодных блюд, кулинарных изделий, закусок
Процессы приготовления, подготовки к реализации и презентации холодных блюд, кулинарных изделий, закусок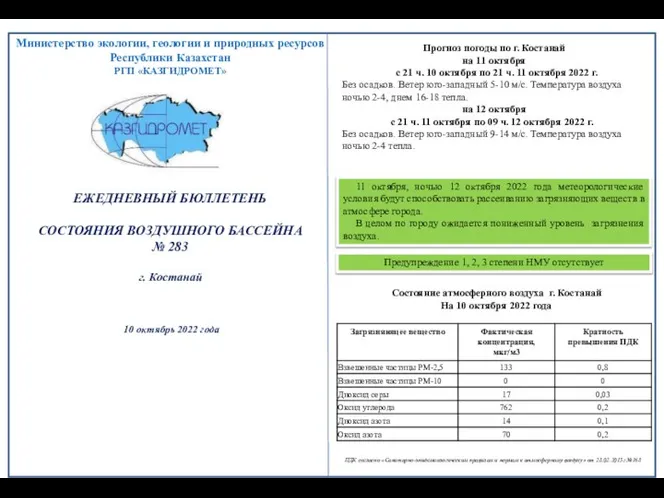 6343f139f10cakostanay-nmu-10-10-22-1
6343f139f10cakostanay-nmu-10-10-22-1 Характеристика аффективно - потребностной сферы школьников, испытывающих трудности в обучении
Характеристика аффективно - потребностной сферы школьников, испытывающих трудности в обучении