Содержание
- 2. What You Will Learn About How technical developments are eroding privacy and anonymity Types of computer
- 3. Privacy in Cyberspace Privacy refers to an individual’s ability to restrict the collection, use, and sale
- 4. Technology and Anonymity Anonymity is the ability to convey a message without disclosing one’s identity It
- 5. Cookies Cookies are small files that are written to an individual’s hard drive whenever a Web
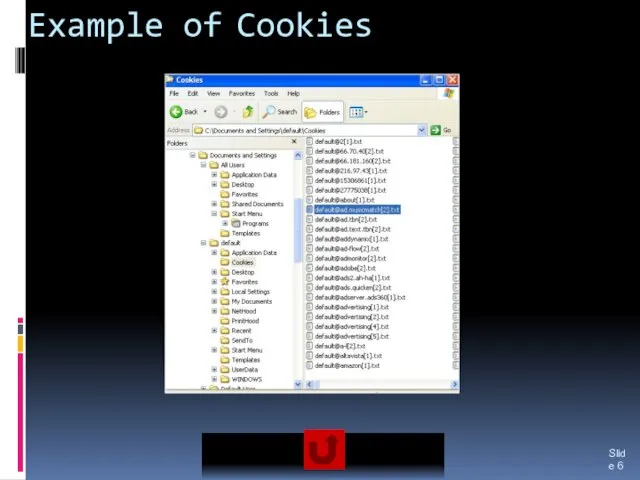
- 6. Example of Cookies Slide
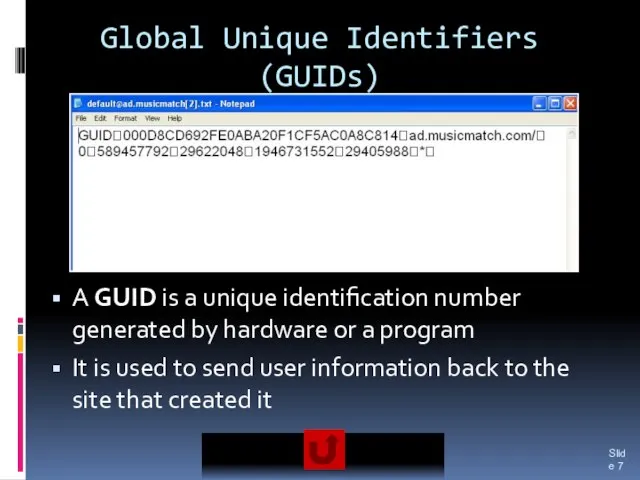
- 7. Global Unique Identifiers (GUIDs) A GUID is a unique identification number generated by hardware or a
- 8. Global Unique Identifiers (GUIDs) Example of GUIDs Intel Corporation placed a GUID in its Pentium III
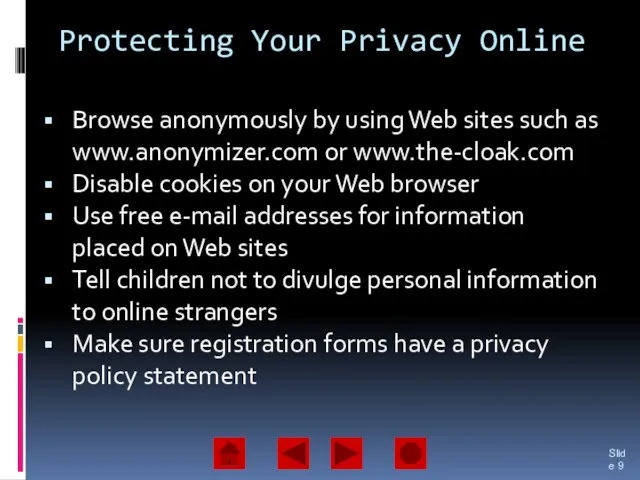
- 9. Protecting Your Privacy Online Browse anonymously by using Web sites such as www.anonymizer.com or www.the-cloak.com Disable
- 10. Protecting Your Privacy At Home Cell phones have GPS capability Parents, EMS can find people Intrusive
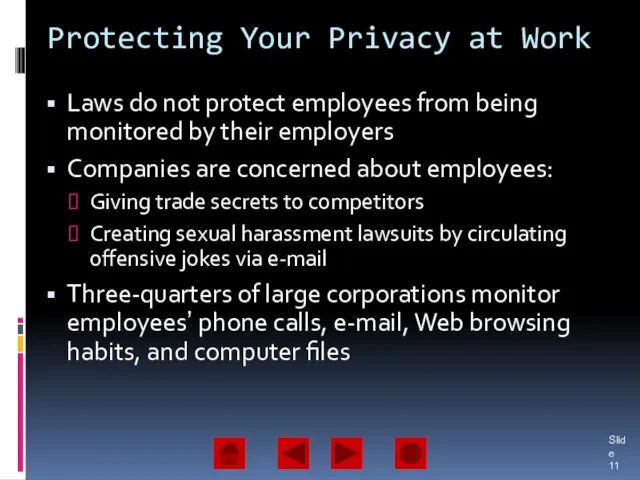
- 11. Protecting Your Privacy at Work Laws do not protect employees from being monitored by their employers
- 12. Protecting Privacy at Work Rules to follow while at work: Do not use the employer’s phone
- 13. Computer Crime and Cybercrime Computer crimes occur when intruders gain unauthorized access to computer systems Cybercrime
- 14. Computer Crime and Cybercrime Types of Computer Crime Identity Theft Computer Viruses More Rogue Programs Fraud
- 15. Identity Theft Identity theft is one of the fastest growing crimes in the United States and
- 16. Computer Viruses Computer viruses are malicious programs that infect a computer system causing various problems with
- 17. How Virus Infections Spread Virus Infections spread by: Inserting a disk with an infected program and
- 18. Types of Viruses File Infectors Attach themselves to program files Spread to other programs on the
- 19. Types of Viruses Macro Viruses Infect the automatic command capabilities of productivity software Attach themselves to
- 20. More Rogue Programs Time Bombs Also called logic bombs Harmless until a certain event or circumstance
- 21. More Rogue Programs Denial of Service Attack (DoS) Syn flooding Overload an Internet server with a
- 22. Fraud and Theft Selling social security numbers Memory shaving – taking RAM chips from computers Salami
- 23. Techniques to Obtain Passwords Password guessing Shoulder surfing Packet sniffing Dumpster diving Social engineering Superuser status
- 24. Forgery and Blackmail Forgery Internet data can appear to be coming from one source when its
- 25. Meet the Attackers Hackers Computer hobbyists Find weaknesses and loopholes in computer systems Rarely destructive Adhere
- 26. Meet the Attackers Crackers Also called black hats Obsessed with entering secure computer systems Rarely destructive
- 27. More Attackers Disgruntled Employees Sabotage their company’s computer system Create security holes called trap doors May
- 28. More Attackers Shills Use Internet auctions Secret operatives who bid on a seller’s item to drive
- 29. Security Risks Computer security risk is any event, action, or situation that leads to the loss
- 30. Information Warfare Information warfare is the use of information technologies to corrupt or destroy an enemy's
- 31. Protecting Your Computer System To protect a computer from power-related problems you should: Use programs that
- 32. Controlling Access To control access to a computer: Use authentication passwords Use callback systems Use “know
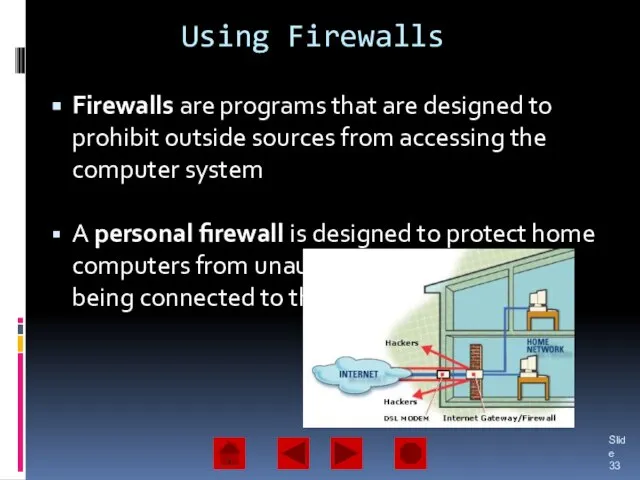
- 33. Using Firewalls Firewalls are programs that are designed to prohibit outside sources from accessing the computer
- 34. Avoiding Scams Only conduct business with established companies Read the fine print Don’t provide financial or
- 35. Preventing Cyberstalkers Don’t share personal information in chat rooms Be extremely cautious about meeting anyone you’ve
- 36. The Encryption Debate Encryption is the coding and scrambling process by which a message is made
- 37. Encryption Basics A readable message is called plaintext An encryption key is a formula used to
- 38. Encryption Basics Symmetric key encryption are encryption techniques that use the same key to encrypt and
- 39. The Problem of Key Interception Rot-13 is not a secure encryption system Symmetric key encryption systems
- 40. Public Key Encryption Public key encryption uses two different keys Public key is the encryption key
- 41. Digital Signatures and Certificates Digital signatures are a technique used to guarantee that a message has
- 42. Public Key Infrastructure (PKI) A public key infrastructure is a uniform set of encryption standards that
- 43. Encryption and Public Security Issues Encryption can be used for illegal as well as legitimate means
- 44. Summary Many websites collect and store information about Web users Cookies and GUIDs are used to
- 45. Summary continued Computer criminals Crackers Cybergangs Virus authors Swindlers Shills Cyberstalkers Sexual predators A computer security
- 47. Скачать презентацию



































 Casting Actors
Casting Actors National Sports Renju
National Sports Renju Стратегію підготовлено Мінекономрозвитку разом із експертами
Стратегію підготовлено Мінекономрозвитку разом із експертами  Не умри, и мы отстанем
Не умри, и мы отстанем Литература периода Великой Отечественной войны и первого послевоенного десятилетия.
Литература периода Великой Отечественной войны и первого послевоенного десятилетия. Объекты изучения физики
Объекты изучения физики В.Ф. Одоевский "Мороз Иванович"
В.Ф. Одоевский "Мороз Иванович" Епархиальные катехизаторско-педагогические курсы Нижнетагильской епархии
Епархиальные катехизаторско-педагогические курсы Нижнетагильской епархии «Строительство завода глубокой переработки масличных семян (ПЗПМС) производительностью 330 тыс. тонн/год (1000 тонн/сутки) по семенам
«Строительство завода глубокой переработки масличных семян (ПЗПМС) производительностью 330 тыс. тонн/год (1000 тонн/сутки) по семенам Природные зоны Земли
Природные зоны Земли Осень в природе 2 часть
Осень в природе 2 часть Презентация Тришиной Марины Богородские игрушки и Сергиево Посадские матрёшки
Презентация Тришиной Марины Богородские игрушки и Сергиево Посадские матрёшки Презентация на тему Маша и медведь
Презентация на тему Маша и медведь  Применение искусственного интеллекта в сельском хозяйстве
Применение искусственного интеллекта в сельском хозяйстве Прямоугольный параллелепипед
Прямоугольный параллелепипед Урок КВН "ПРИРОДА ВОКРУГ НАС!"
Урок КВН "ПРИРОДА ВОКРУГ НАС!" ОРКСЭ. Итоговый урок за 2 четверть
ОРКСЭ. Итоговый урок за 2 четверть Проекционные визуальные средства обучения
Проекционные визуальные средства обучения ПРЕЗЕНТАЦИЯ. ЧАСТЬ 2
ПРЕЗЕНТАЦИЯ. ЧАСТЬ 2 Как выбрать идеальный авточехол
Как выбрать идеальный авточехол Такие разные числа
Такие разные числа 1 сентября 1993 года открылась новая школа
1 сентября 1993 года открылась новая школа Параметры экспертизы конкурсных заявок в рамках проекта «Школа Росатома»
Параметры экспертизы конкурсных заявок в рамках проекта «Школа Росатома» Однородные и неоднородные определения
Однородные и неоднородные определения Программы учебных дисциплин в компетентностном формате
Программы учебных дисциплин в компетентностном формате Использование технологии проектной деятельности при подготовке конкурсных работ учащимися объединения хранители природы
Использование технологии проектной деятельности при подготовке конкурсных работ учащимися объединения хранители природы Назначение и принцип работы приборов радиационной и химической разведки. Лекция 11
Назначение и принцип работы приборов радиационной и химической разведки. Лекция 11 Получение оплаты за проживание и предоставление платных услуг в гостинице
Получение оплаты за проживание и предоставление платных услуг в гостинице