Содержание
- 2. Encryption Algorithms Transposition Cipher A lot of codes are simple in design. Just by changing the
- 3. Encryption Algorithms Transposition Cipher Transposition cipher rearrange characters according to some scheme. This rearrangement was classically
- 4. Encryption Algorithms Transposition Cipher Many transposition ciphers permute the characters of the plaintext with a fixed
- 5. Encryption Algorithms Transposition Cipher Like columnar transposition, periodic permutation cipher can be viewed as transpositions of
- 6. Encryption Algorithms Transposition Cipher Using a key word or phrase, such as, for example CONVENIENCE, assign
- 7. Encryption Algorithms Transposition Cipher Example. Another method of transposition is a Variant of column transposition that
- 8. Encryption Algorithms Transposition Cipher Another interesting form of transposition is the "turning grille", used by Germany
- 9. Encryption Algorithms Transposition Cipher Example. Example of a turning grille and its use for message: M=HERE
- 10. Encryption Algorithms Transposition Cipher Example. M=HERE IS A SECRET MESSAGE WRITE Third Round Fourth Round C=HEEMS
- 11. Encryption Algorithms Simple Substitution Ciphers Simple substitution cipher replace each character of plaintext with a corresponding
- 12. Encryption Algorithms Simple Substitution Ciphers Compass Cipher-A Method for Alphabet Substitution There are lots of ways
- 13. Encryption Algorithms Simple Substitution Ciphers Letter Spokes Cipher Clock It’s another way of making up a
- 14. Encryption Algorithms Simple Substitution Ciphers Alphabet & Word Correlated Ciphers. Sometimes keywords are used to help
- 15. Encryption Algorithms Simple Substitution Ciphers Cipher based on shifted alphabet (“direct standard alphabets”) shift the letters
- 16. Encryption Algorithms Simple Substitution Ciphers Addition (shifting) and multiplication can be combined to give an affine
- 17. Encryption Algorithms Single-Letter Frequency Analysis Simple substitution cipher are generally easy to break in a ciphertext-only
- 18. Encryption Algorithms Homophonic Substitution cipher A homophonic substitution cipher maps each character a of the plaintext
- 19. 1.Single letter frequency distributions. Encryption Algorithms Homophonic Substitution cipher
- 20. Encryption Algorithms Beale Ciphers The Beale cipher is an example of a homophonic substitution cipher. The
- 21. Encryption Algorithms Polygram Substitution Cipher All of the preceding substitution cipher encipher a single letter of
- 22. Playfair has inspired some related bigraphic ciphers that, on the one hand, improve security by involving
- 23. The first of the three rules for Playfair encipherment changes one two-letter group, or digraph, to
- 24. Encryption Algorithms Trifid Cipher This is the Bifid cipher of Delastelle, and the general principle of
- 26. Скачать презентацию
Слайд 2Encryption Algorithms
Transposition Cipher
A lot of codes are simple in design. Just
Encryption Algorithms
Transposition Cipher
A lot of codes are simple in design. Just

Lumping Words (Format)
Get rid of spaces and returns to lump words together. Use upper case to make the code harder to read and decode.
Ciphertext: THISISHARDCODEFORMANYPEOPLE Message: THIS IS HARD CODE FOR MANY PEOPLE
Character Bloks
Block letter of a message by 2,3 or more characters.
Ciphertext: TH IS IS HA RD CO DE FO RM AN YP EO PL E Message: THIS IS HARD CODE FOR MANY PEOPLE
Backwards English
Writing words, sentences, or entire message backwards can be very confusing!
Ciphertext: SIHT SI DRAH EDOC ROF YNAM ELPOEP Message: THIS IS HARD CODE FOR MANY PEOPLE
Reading SIHT backwards yields the answer THIS.
Слайд 3Encryption Algorithms
Transposition Cipher
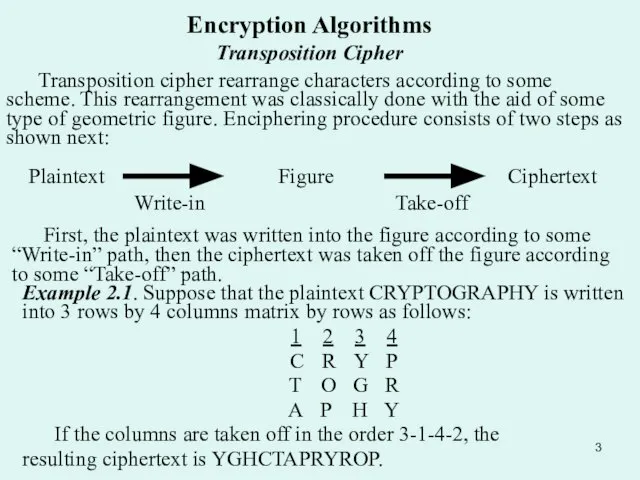
Transposition cipher rearrange characters according to some scheme. This
Encryption Algorithms
Transposition Cipher
Transposition cipher rearrange characters according to some scheme. This
Plaintext
Figure
Ciphertext
Write-in
Take-off
First, the plaintext was written into the figure according to some “Write-in” path, then the ciphertext was taken off the figure according to some “Take-off” path.
Example 2.1. Suppose that the plaintext CRYPTOGRAPHY is written into 3 rows by 4 columns matrix by rows as follows:
1 2 3 4
C R Y P
T O G R
A P H Y
If the columns are taken off in the order 3-1-4-2, the
resulting ciphertext is YGHCTAPRYROP.
Слайд 4Encryption Algorithms
Transposition Cipher
Many transposition ciphers permute the characters of the plaintext
Encryption Algorithms
Transposition Cipher
Many transposition ciphers permute the characters of the plaintext
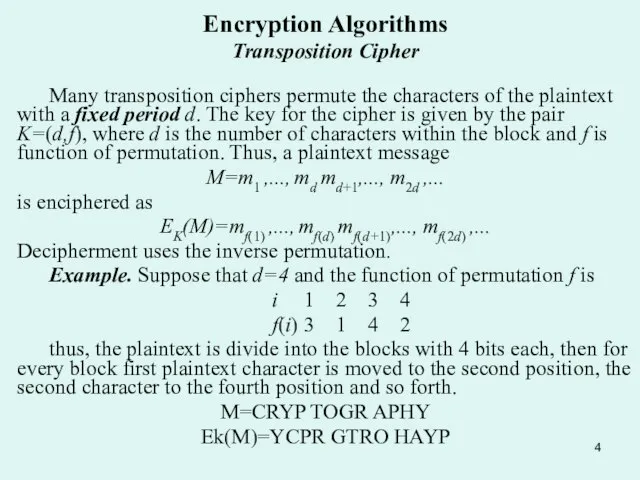
M=m1 ,..., md md+1,..., m2d ,...
is enciphered as
EK(M)=mf(1) ,..., mf(d) mf(d+1),..., mf(2d) ,...
Decipherment uses the inverse permutation.
Example. Suppose that d=4 and the function of permutation f is
i 1 2 3 4
f(i) 3 1 4 2
thus, the plaintext is divide into the blocks with 4 bits each, then for every block first plaintext character is moved to the second position, the second character to the fourth position and so forth.
M=CRYP TOGR APHY
Ek(M)=YCPR GTRO HAYP
Слайд 5Encryption Algorithms
Transposition Cipher
Like columnar transposition, periodic permutation cipher can be viewed
Encryption Algorithms
Transposition Cipher
Like columnar transposition, periodic permutation cipher can be viewed
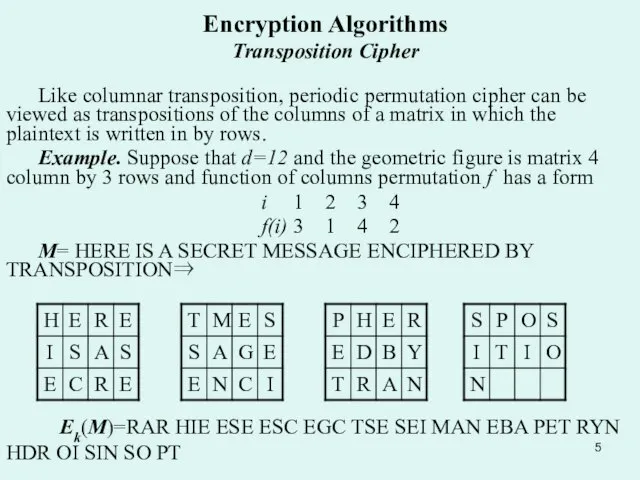
Example. Suppose that d=12 and the geometric figure is matrix 4 column by 3 rows and function of columns permutation f has a form
i 1 2 3 4
f(i) 3 1 4 2
M= HERE IS A SECRET MESSAGE ENCIPHERED BY TRANSPOSITION⇒
Ek(M)=RAR HIE ESE ESC EGC TSE SEI MAN EBA PET RYN HDR OI SIN SO PT
Слайд 6Encryption Algorithms
Transposition Cipher
Using a key word or phrase, such as, for
Encryption Algorithms
Transposition Cipher
Using a key word or phrase, such as, for
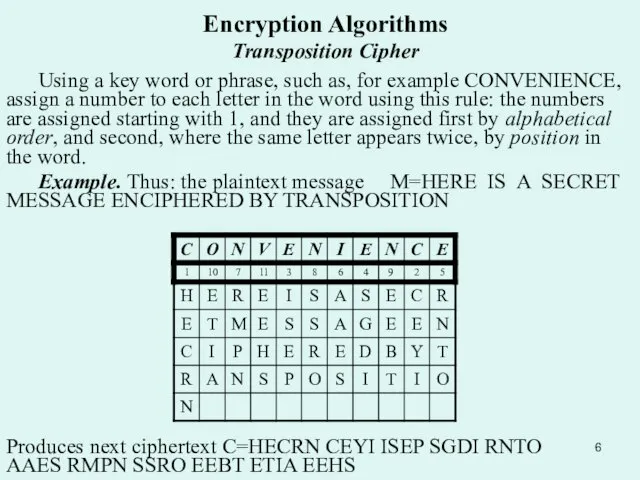
Example. Thus: the plaintext message M=HERE IS A SECRET MESSAGE ENCIPHERED BY TRANSPOSITION
Produces next ciphertext C=HECRN CEYI ISEP SGDI RNTO AAES RMPN SSRO EEBT ETIA EEHS
Слайд 7Encryption Algorithms
Transposition Cipher
Example. Another method of transposition is a Variant of
Encryption Algorithms
Transposition Cipher
Example. Another method of transposition is a Variant of
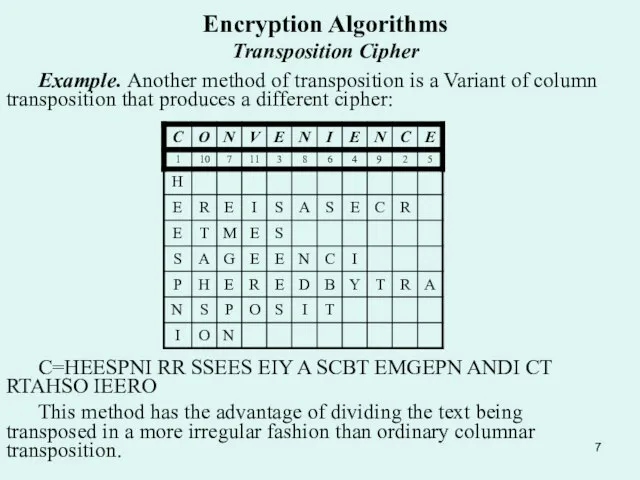
C=HEESPNI RR SSEES EIY A SCBT EMGEPN ANDI CT RTAHSO IEERO
This method has the advantage of dividing the text being transposed in a more irregular fashion than ordinary columnar transposition.
Слайд 8Encryption Algorithms
Transposition Cipher
Another interesting form of transposition is the "turning grille",
Encryption Algorithms
Transposition Cipher
Another interesting form of transposition is the "turning grille",
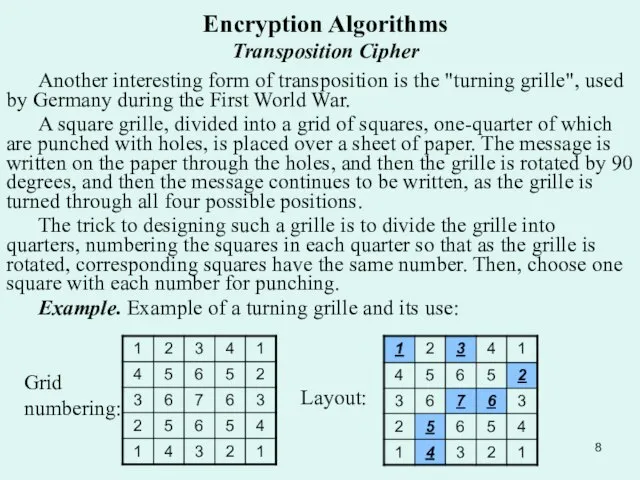
A square grille, divided into a grid of squares, one-quarter of which are punched with holes, is placed over a sheet of paper. The message is written on the paper through the holes, and then the grille is rotated by 90 degrees, and then the message continues to be written, as the grille is turned through all four possible positions.
The trick to designing such a grille is to divide the grille into quarters, numbering the squares in each quarter so that as the grille is rotated, corresponding squares have the same number. Then, choose one square with each number for punching.
Example. Example of a turning grille and its use:
Layout:
Grid numbering:
Слайд 9Encryption Algorithms
Transposition Cipher
Example. Example of a turning grille and its use
Encryption Algorithms
Transposition Cipher
Example. Example of a turning grille and its use
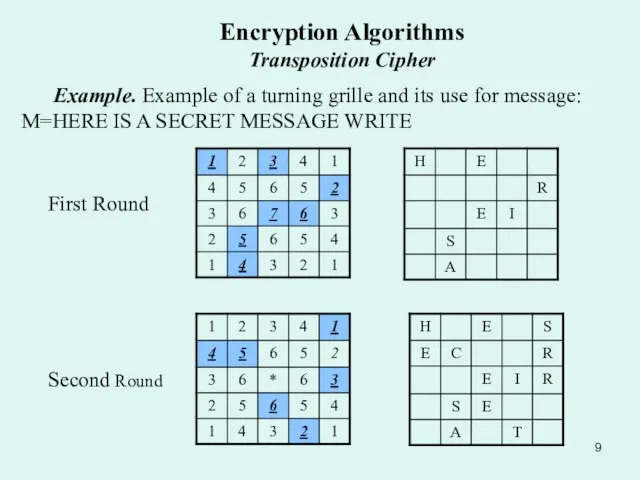
First Round
Second Round
Слайд 10Encryption Algorithms
Transposition Cipher
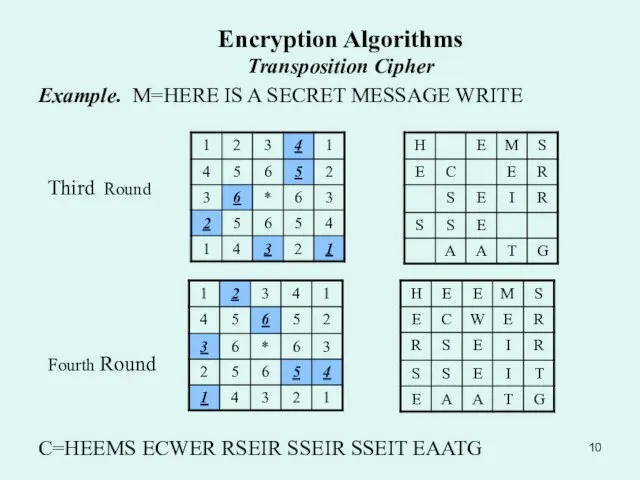
Example. M=HERE IS A SECRET MESSAGE WRITE
Third Round
Fourth Round
C=HEEMS
Encryption Algorithms
Transposition Cipher
Example. M=HERE IS A SECRET MESSAGE WRITE
Third Round
Fourth Round
C=HEEMS
Слайд 11Encryption Algorithms
Simple Substitution Ciphers
Simple substitution cipher replace each character of plaintext
Encryption Algorithms
Simple Substitution Ciphers
Simple substitution cipher replace each character of plaintext
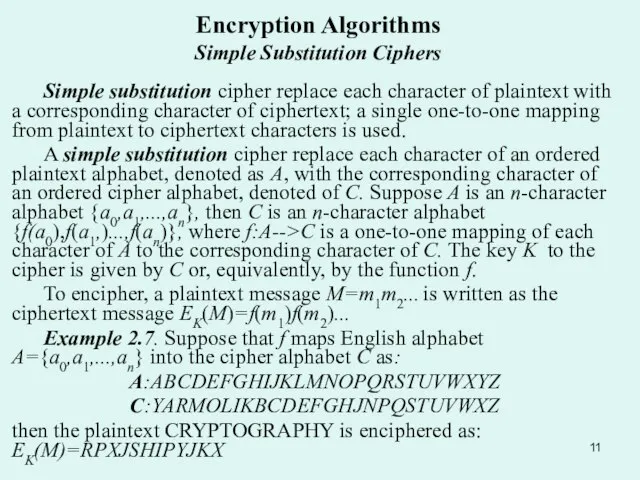
A simple substitution cipher replace each character of an ordered plaintext alphabet, denoted as Α, with the corresponding character of an ordered cipher alphabet, denoted of C. Suppose A is an n-character alphabet {a0,a1,...,an}, then C is an n-character alphabet {f(a0),f(a1,)...,f(an)}, where f:A-->C is a one-to-one mapping of each character of A to the corresponding character of C. The key K to the cipher is given by C or, equivalently, by the function f.
To encipher, a plaintext message M=m1m2... is written as the ciphertext message EK(M)=f(m1)f(m2)...
Example 2.7. Suppose that f maps English alphabet A={a0,a1,...,an} into the cipher alphabet C as:
A:ABCDEFGHIJKLMNOPQRSTUVWXYZ
C:YARMOLIKBCDEFGHJNPQSTUVWXZ
then the plaintext CRYPTOGRAPHY is enciphered as: EK(M)=RPXJSHIPYJKX
Слайд 12Encryption Algorithms
Simple Substitution Ciphers
Compass Cipher-A Method for Alphabet Substitution
There are lots
Encryption Algorithms
Simple Substitution Ciphers
Compass Cipher-A Method for Alphabet Substitution
There are lots
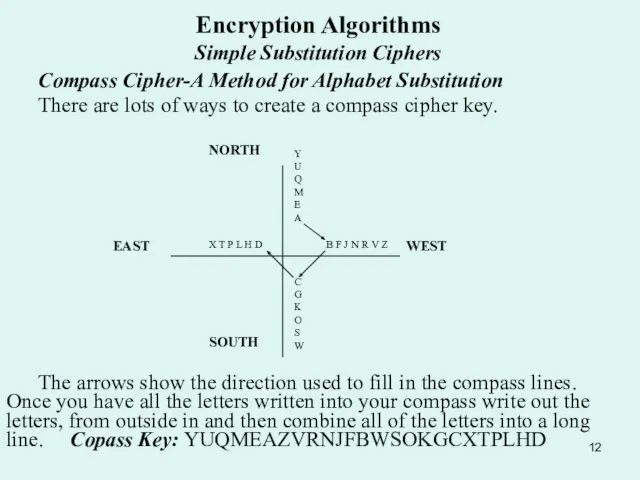
The arrows show the direction used to fill in the compass lines. Once you have all the letters written into your compass write out the letters, from outside in and then combine all of the letters into a long line. Copass Key: YUQMEAZVRNJFBWSOKGCXTPLHD
Слайд 13Encryption Algorithms
Simple Substitution Ciphers
Letter Spokes Cipher Clock
It’s another way of making
Encryption Algorithms
Simple Substitution Ciphers
Letter Spokes Cipher Clock
It’s another way of making
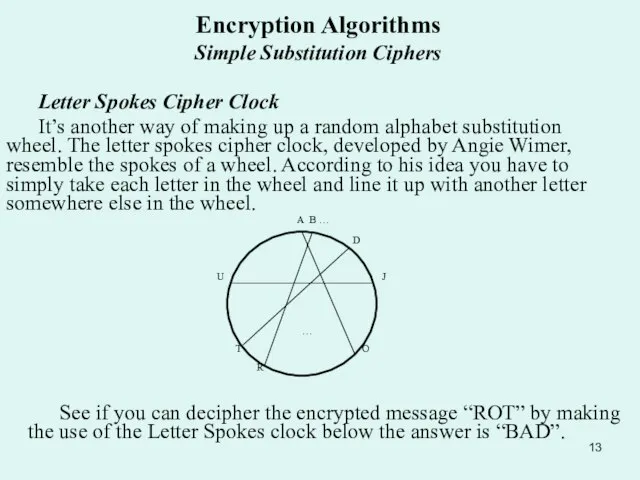
See if you can decipher the encrypted message “ROT” by making the use of the Letter Spokes clock below the answer is “BAD”.
Слайд 14Encryption Algorithms
Simple Substitution Ciphers
Alphabet & Word Correlated Ciphers.
Sometimes keywords
Encryption Algorithms
Simple Substitution Ciphers
Alphabet & Word Correlated Ciphers.
Sometimes keywords
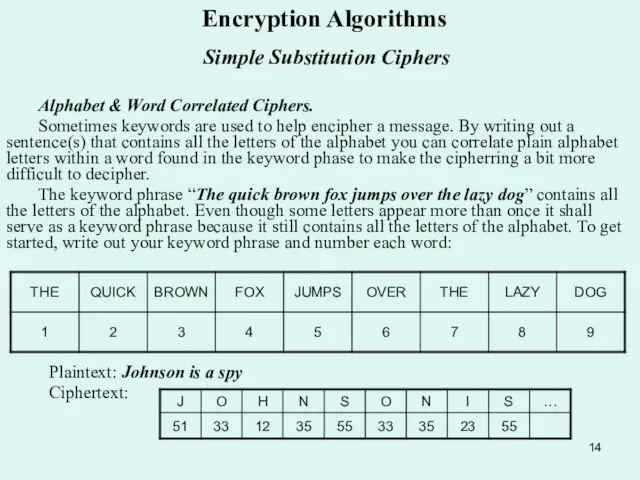
The keyword phrase “The quick brown fox jumps over the lazy dog” contains all the letters of the alphabet. Even though some letters appear more than once it shall serve as a keyword phrase because it still contains all the letters of the alphabet. To get started, write out your keyword phrase and number each word:
Plaintext: Johnson is a spy
Ciphertext:
Слайд 15Encryption Algorithms
Simple Substitution Ciphers
Cipher based on shifted alphabet (“direct standard alphabets”)
Encryption Algorithms
Simple Substitution Ciphers
Cipher based on shifted alphabet (“direct standard alphabets”)

f(a)=(a+k) mod n,
where n is the size of the alphabet and a denotes letter and its position in A.
For the English alphabet
0-A, 1-B, 2-C, 3-D, 4-E, 5-F, 6-G, 7-H, 8-I, 9-J, 10-K, 11-L, 12-M, 13-N, 14-O, 15-P, 16-Q, 17-R, 18-S, 19-T, 20-U, 21-V, 22-W, 23-X, 24-Y, 25-Z.
Under the Caesar cipher, our plaintext CRYPTOGRAPHY is enciphered by
f(a)=(a+3) mod 26,
then EK(M)=FUBSWRJUDSKB.
There are more complex transformation of the plaintext alphabet. Ciphers based on multiplications (“decimations”) are shown below
f(a)=ka mod n,
where k and n are relatively prime so that the letter of the alphabet produce a complete set of residues. For the plaintext CRYPTOGRAPHY and k=3 we will get f(a)=3a mod 26, and EK(M)=GZUTFQSZATVU.
Слайд 16Encryption Algorithms
Simple Substitution Ciphers
Addition (shifting) and multiplication can be combined to
Encryption Algorithms
Simple Substitution Ciphers
Addition (shifting) and multiplication can be combined to
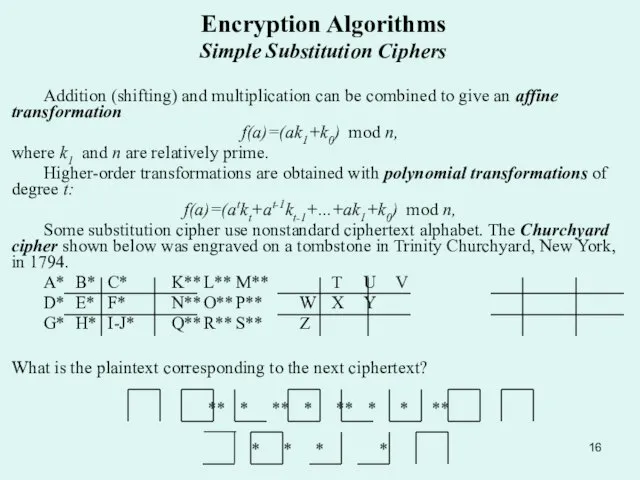
f(a)=(ak1+k0) mod n,
where k1 and n are relatively prime.
Higher-order transformations are obtained with polynomial transformations of degree t:
f(a)=(atkt+at-1kt-1+...+ak1+k0) mod n,
Some substitution cipher use nonstandard ciphertext alphabet. The Churchyard cipher shown below was engraved on a tombstone in Trinity Churchyard, New York, in 1794.
A* B* C* K** L** M** T U V
D* E* F* N** O** P** W X Y
G* H* I-J* Q** R** S** Z
What is the plaintext corresponding to the next ciphertext?
** * ** * ** * * **
* * * *
Слайд 17Encryption Algorithms Single-Letter Frequency Analysis
Simple substitution cipher are generally easy to break
Encryption Algorithms Single-Letter Frequency Analysis
Simple substitution cipher are generally easy to break
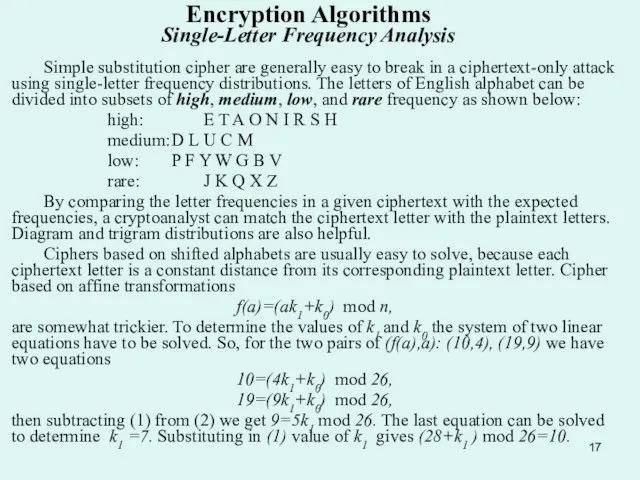
high: E T A O N I R S H
medium: D L U C M
low: P F Y W G B V
rare: J K Q X Z
By comparing the letter frequencies in a given ciphertext with the expected frequencies, a cryptoanalyst can match the ciphertext letter with the plaintext letters. Diagram and trigram distributions are also helpful.
Ciphers based on shifted alphabets are usually easy to solve, because each ciphertext letter is a constant distance from its corresponding plaintext letter. Cipher based on affine transformations
f(a)=(ak1+k0) mod n,
are somewhat trickier. To determine the values of k1 and k0 the system of two linear equations have to be solved. So, for the two pairs of (f(a),a): (10,4), (19,9) we have two equations
10=(4k1+k0) mod 26,
19=(9k1+k0) mod 26,
then subtracting (1) from (2) we get 9=5k1 mod 26. The last equation can be solved to determine k1 =7. Substituting in (1) value of k1 gives (28+k1 ) mod 26=10.
Слайд 18Encryption Algorithms Homophonic Substitution cipher
A homophonic substitution cipher maps each character a
Encryption Algorithms Homophonic Substitution cipher
A homophonic substitution cipher maps each character a

Example. Let the English letters are enciphered as integers between 00 and 99, where the number of integers assigned to a letter is proportional to the relative frequency of the letter, and no integer is assigned to more than one letter. A possible assignment of integers to the letters in the message CRYPTOGRAPHY are show below (integer assignment for the remaining letters of the alphabet are not given)
letter Homophones
A 23, 25, 97, 95, 81, 33, 12, 11
C 44, 77, 34, 51
G 87, 41
H 59, 90, 00, 26
O 66, 87, 02, 15, 22, 09, 83, 54
P 04, 58
R 38, 07, 94, 30, 56, 67
T 55, 71, 72, 80, 01, 12, 29, 50, 68
Y 88
One possible encipherment of the message is:
C= 77 07 88 58 72 54 41 30 97 04 00 88
Слайд 19 1.Single letter frequency distributions.
Encryption Algorithms Homophonic Substitution cipher
1.Single letter frequency distributions.
Encryption Algorithms Homophonic Substitution cipher
Слайд 20Encryption Algorithms Beale Ciphers
The Beale cipher is an example of a homophonic
Encryption Algorithms Beale Ciphers
The Beale cipher is an example of a homophonic

Declaration of Independence (first 100 words)
01 When, in the course of human events, it becomes necessary
11 for one people to dissolve the political bands which have
21 connected them with another, and to assume among the Powers
31 of the earth the separate and equal station to which
41 the Laws of Nature and of Nature’s God entitle them,
51 a decent respect to the opinions of mankind requires that
61 they should declare the causes which impel them to the
71 separation. We hold these truths to be self-evident; that
81 all men are created equal, that they are endowed by
91 their Creator with certain unalienable rights; that among
Beale enciphered each letter in the plaintext message by substituting the number of some word which started with that letter. The letter W, for example, was enciphered with the number 1, 19, 40, 66, 72, ... . As an example let consider the word PLAIN. The result of enciphering are shown below:
M = P L A I N
C = 13 42 81 08 44
Слайд 21Encryption Algorithms Polygram Substitution Cipher
All of the preceding substitution cipher encipher a
Encryption Algorithms Polygram Substitution Cipher
All of the preceding substitution cipher encipher a
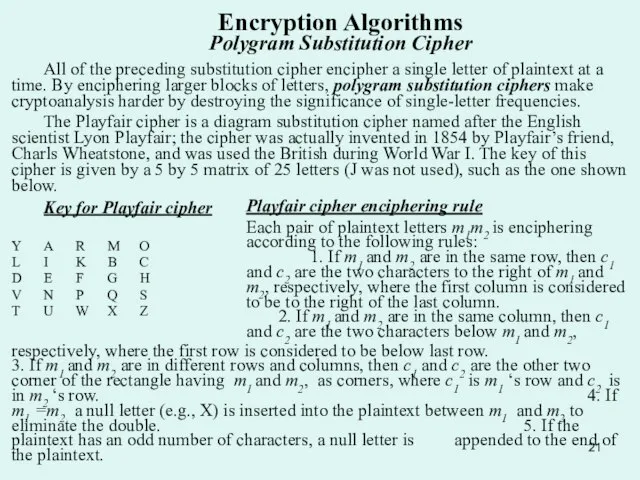
The Playfair cipher is a diagram substitution cipher named after the English scientist Lyon Playfair; the cipher was actually invented in 1854 by Playfair’s friend, Charls Wheatstone, and was used the British during World War I. The key of this cipher is given by a 5 by 5 matrix of 25 letters (J was not used), such as the one shown below.
Key for Playfair cipher
Y A R M O
L I K B C
D E F G H
V N P Q S
T U W X Z
Playfair cipher enciphering rule
Each pair of plaintext letters m1m2 is enciphering according to the following rules: 1. If m1 and m2 are in the same row, then c1 and c2 are the two characters to the right of m1 and m2, respectively, where the first column is considered to be to the right of the last column. 2. If m1 and m2 are in the same column, then c1 and c2 are the two characters below m1 and m2,
respectively, where the first row is considered to be below last row. 3. If m1 and m2 are in different rows and columns, then c1 and c2 are the other two corner of the rectangle having m1 and m2, as corners, where c1 is m1 ‘s row and c2 is in m2 ‘s row. 4. If m1 =m2 a null letter (e.g., X) is inserted into the plaintext between m1 and m2 to eliminate the double. 5. If the plaintext has an odd number of characters, a null letter is appended to the end of the plaintext.
Слайд 22 Playfair has inspired some related bigraphic ciphers that, on the one hand,
Playfair has inspired some related bigraphic ciphers that, on the one hand,
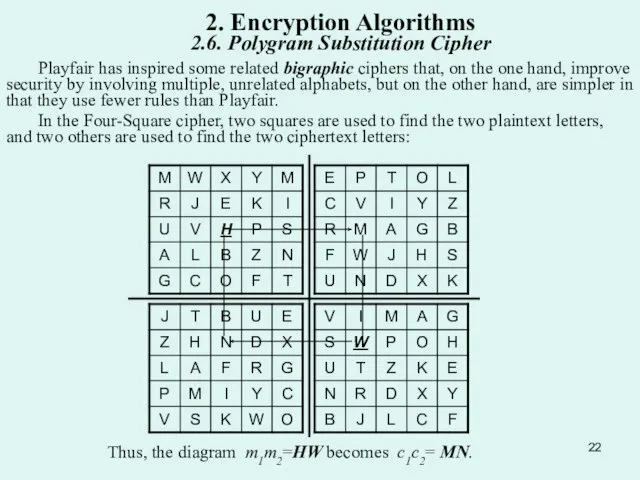
In the Four-Square cipher, two squares are used to find the two plaintext letters, and two others are used to find the two ciphertext letters:
2. Encryption Algorithms 2.6. Polygram Substitution Cipher
Thus, the diagram m1m2=HW becomes c1c2= MN.
Слайд 23 The first of the three rules for Playfair encipherment changes one two-letter
The first of the three rules for Playfair encipherment changes one two-letter
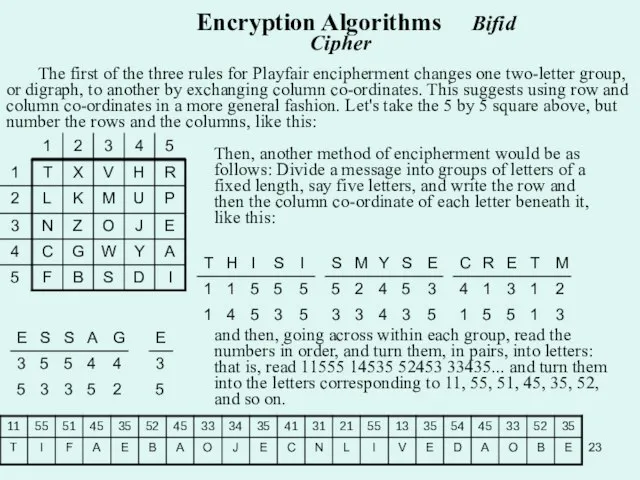
Encryption Algorithms Bifid Cipher
Then, another method of encipherment would be as follows: Divide a message into groups of letters of a fixed length, say five letters, and write the row and then the column co-ordinate of each letter beneath it, like this:
and then, going across within each group, read the numbers in order, and turn them, in pairs, into letters: that is, read 11555 14535 52453 33435... and turn them into the letters corresponding to 11, 55, 51, 45, 35, 52, and so on.
Слайд 24Encryption Algorithms Trifid Cipher
This is the Bifid cipher of Delastelle, and the
Encryption Algorithms Trifid Cipher
This is the Bifid cipher of Delastelle, and the
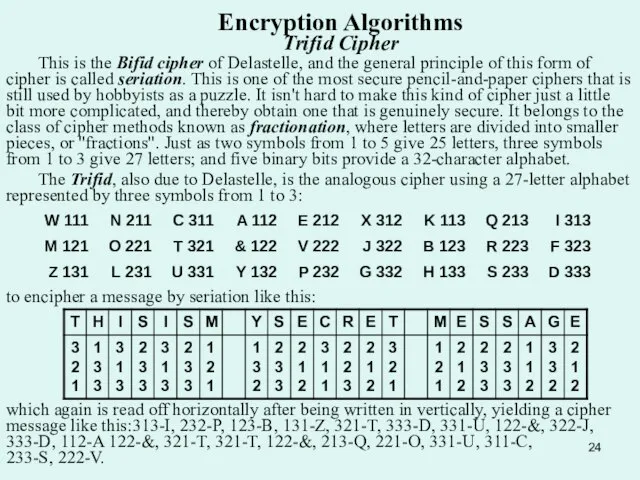
The Trifid, also due to Delastelle, is the analogous cipher using a 27-letter alphabet represented by three symbols from 1 to 3:
to encipher a message by seriation like this:
which again is read off horizontally after being written in vertically, yielding a cipher message like this:313-I, 232-P, 123-B, 131-Z, 321-T, 333-D, 331-U, 122-&, 322-J, 333-D, 112-A 122-&, 321-T, 321-T, 122-&, 213-Q, 221-O, 331-U, 311-C, 233-S, 222-V.
 техника безоп
техника безоп шиповое соединение
шиповое соединение Взаємодія України та Португалії
Взаємодія України та Португалії Основы конституционного строя России
Основы конституционного строя России Обсуждение художественного фильма Полосатый рейс с точки зрения трудового права
Обсуждение художественного фильма Полосатый рейс с точки зрения трудового права Планирование веб-релизовв условиях многопоточности задачсо скачущими приоритетами
Планирование веб-релизовв условиях многопоточности задачсо скачущими приоритетами Способы кодирования информации.
Способы кодирования информации. Технология в жизни человека и общества
Технология в жизни человека и общества Пикапы маслозаправщики. Схема движения по маршрутам
Пикапы маслозаправщики. Схема движения по маршрутам «Магнетизм и его изучение». Учитель физики Балашова Н. А. Троицк 2011г.
«Магнетизм и его изучение». Учитель физики Балашова Н. А. Троицк 2011г.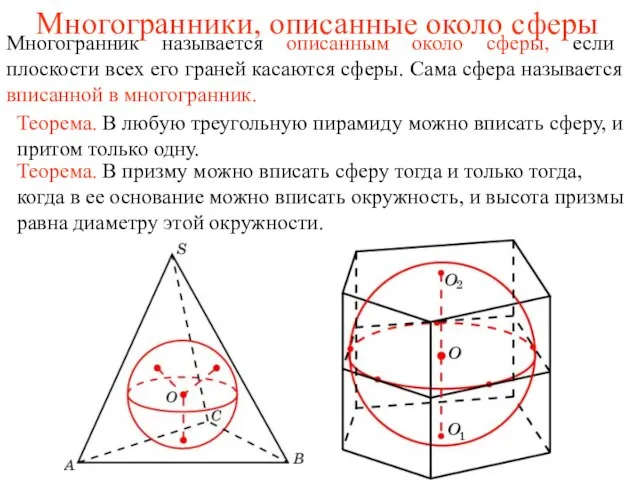 Многогранники, описанные около сферы
Многогранники, описанные около сферы Юношеский возраст. Лекция 8.2
Юношеский возраст. Лекция 8.2 Охрана земельных ресурсов – залог эффективного ведения сельского хозяйства
Охрана земельных ресурсов – залог эффективного ведения сельского хозяйства Элементы суггестивного управления в системе педагогической деятельности учителя
Элементы суггестивного управления в системе педагогической деятельности учителя Рязанские народные ремесла и промыслы
Рязанские народные ремесла и промыслы The best job in the world
The best job in the world  ИНФЕКЦИОННЫЙ КОНТРОЛЬ ИНФЕКЦИОННАЯ БЕЗОПАСНОСТЬ
ИНФЕКЦИОННЫЙ КОНТРОЛЬ ИНФЕКЦИОННАЯ БЕЗОПАСНОСТЬ Рекламное агентство
Рекламное агентство 1С-Битрикс: Сайт школы
1С-Битрикс: Сайт школы Презентация Microsoft Office PowerPoint
Презентация Microsoft Office PowerPoint Работа выполнена в рамках проекта «Повышения квалификаций различных категорий работников образования и формирование у них базов
Работа выполнена в рамках проекта «Повышения квалификаций различных категорий работников образования и формирование у них базов FN1_LessonOne
FN1_LessonOne Modal verb May/might
Modal verb May/might Образ ребенка в киноискусстве XX
Образ ребенка в киноискусстве XX Потребление воды и минеральных ресурсов
Потребление воды и минеральных ресурсов Эвдемонизм - это гуманизм
Эвдемонизм - это гуманизм 07_0___163
07_0___163 Презентация "Орфей и Эвридика" - скачать презентации по МХК
Презентация "Орфей и Эвридика" - скачать презентации по МХК