Содержание
- 2. Some ciphers actually used by Soviet spies used a square like this: Encryption Algorithms The Straddling
- 3. Of course, the second digit of a two-digit combination could also have stood, by itself, for
- 4. The VIC cipher is an intricate cipher issued by the Soviet Union to at least one
- 5. 1. The first step is to perform digit by digit subtraction (without carries) of the first
- 6. Encryption Algorithms The VIC Cipher 3. The result of the first step is then expanded to
- 7. 5. And these Ten-digits result are then encoded according to the following algorithm based on Second
- 8. Encryption Algorithms The VIC Cipher
- 9. Encryption Algorithms Porta Table Giovanni Baptista della Porta developed the Porta Table cipher method in 1565.
- 10. Encryption Algorithms Porta Table To begin, write out your plain message and write out the keyword
- 11. The next step is to use the Porta table to create the enciphered message. Use the
- 12. Encryption Algorithms Vigenere Cipher ABCDEFGHIJKLMNOPQRSTUVWXYZ A ABCDEFGHIJKLMNOPQRSTUVWXYZ B BCDEFGHIJKLMNOPQRSTUVWXYZA C CDEFGHIJKLMNOPQRSTUVWXYZAB D DEFGHIJKLMNOPQRSTUVWXYZABC E EFGHIJKLMNOPQRSTUVWXYZABCD F
- 13. Encryption Algorithms Vigenere Cipher The message "Wish you were here" can be encrypted by the three
- 14. Encryption Algorithms Polyalphabetic Substitution Ciphers Simple Substitution cipher use a single mapping from plaintext to ciphertext
- 15. In 1568, Alberty published a manuscript describing a cipher disk that defined multiple substitutions. The disk
- 16. Encryption Algorithms Rotor’s Machines Bases A rotor is a small disk of insulating material, with perhaps
- 17. R3 R2 R1 Reflector C M Encryption Algorithms Rotor’s Machine
- 19. Скачать презентацию
Слайд 2 Some ciphers actually used by Soviet spies used a square like this:
Encryption
Some ciphers actually used by Soviet spies used a square like this:
Encryption

Eight of the most common letters are translated to a single digit. The two digits not used in this way begin two-digit combinations that stand for the remaining letters. This is an example of a variable length code with the prefix property. When it is possible to tell, from the digits one has already seen of a symbol, whether or not one needs to include the next digit in the symbol, then spaces between the digits of a symbol are not needed, and this is what is known as the prefix property.
Слайд 3 Of course, the second digit of a two-digit combination could also have
Of course, the second digit of a two-digit combination could also have

Encryption Algorithms The Straddling Checkerboard
Слайд 4 The VIC cipher is an intricate cipher issued by the Soviet Union
The VIC cipher is an intricate cipher issued by the Soviet Union

The VIC cipher, which we will demonstrate here adapted to the sending of English-language messages, begins with an involved procedure to produce ten pseudorandom digits. The agent must have memorized:
1.Six digits (which were in the form of a date);
2.The first 20 letters of a key phrase (which was the beginning of a popular song);
3. Five random digits for use as a message indicator.
Let the date be July 4, 1776, to give the digits 741776. (Actually, the Russians used their customary form of dates, with the month second.) And let the random indicator group be 77651.
Encryption Algorithms The VIC Cipher
Слайд 5 1. The first step is to perform digit by digit subtraction (without
1. The first step is to perform digit by digit subtraction (without
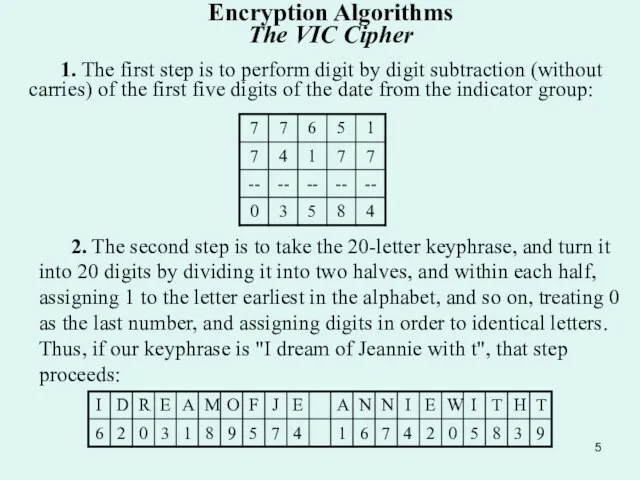
2. The second step is to take the 20-letter keyphrase, and turn it into 20 digits by dividing it into two halves, and within each half, assigning 1 to the letter earliest in the alphabet, and so on, treating 0 as the last number, and assigning digits in order to identical letters. Thus, if our keyphrase is "I dream of Jeannie with t", that step proceeds:
Encryption Algorithms The VIC Cipher
Слайд 6Encryption Algorithms The VIC Cipher
3. The result of the first step is
Encryption Algorithms The VIC Cipher
3. The result of the first step is
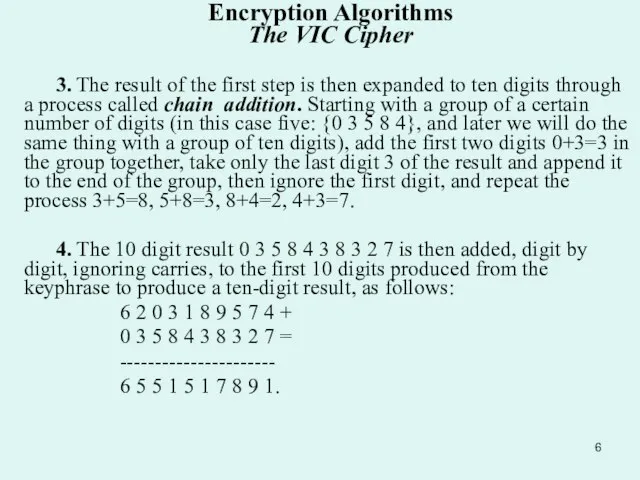
4. The 10 digit result 0 3 5 8 4 3 8 3 2 7 is then added, digit by digit, ignoring carries, to the first 10 digits produced from the keyphrase to produce a ten-digit result, as follows:
6 2 0 3 1 8 9 5 7 4 +
0 3 5 8 4 3 8 3 2 7 =
----------------------
6 5 5 1 5 1 7 8 9 1.
Слайд 7 5. And these Ten-digits result are then encoded according to the following
5. And these Ten-digits result are then encoded according to the following
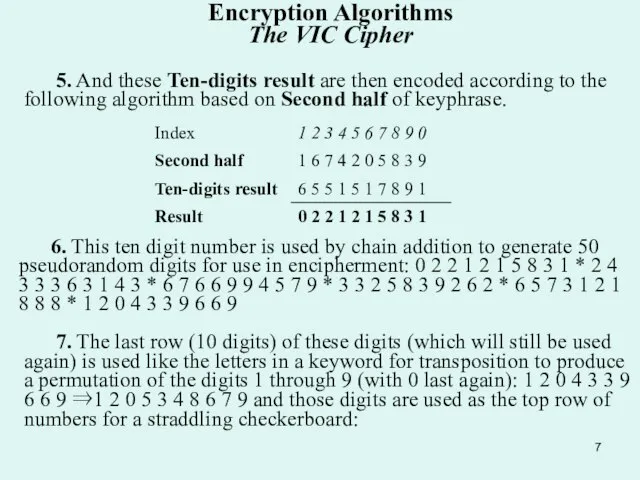
6. This ten digit number is used by chain addition to generate 50 pseudorandom digits for use in encipherment: 0 2 2 1 2 1 5 8 3 1 * 2 4 3 3 3 6 3 1 4 3 * 6 7 6 6 9 9 4 5 7 9 * 3 3 2 5 8 3 9 2 6 2 * 6 5 7 3 1 2 1 8 8 8 * 1 2 0 4 3 3 9 6 6 9
7. The last row (10 digits) of these digits (which will still be used again) is used like the letters in a keyword for transposition to produce a permutation of the digits 1 through 9 (with 0 last again): 1 2 0 4 3 3 9 6 6 9 ⇒1 2 0 5 3 4 8 6 7 9 and those digits are used as the top row of numbers for a straddling checkerboard:
Encryption Algorithms The VIC Cipher
Слайд 8Encryption Algorithms The VIC Cipher
Encryption Algorithms The VIC Cipher

Слайд 9 Encryption Algorithms Porta Table
Giovanni Baptista della Porta developed the Porta
Encryption Algorithms Porta Table
Giovanni Baptista della Porta developed the Porta
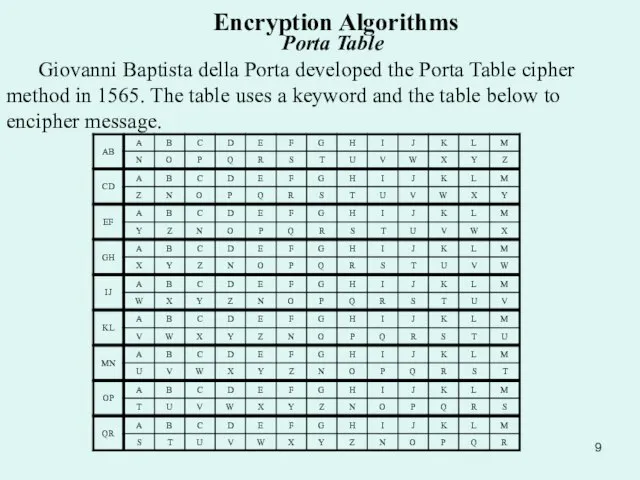
Слайд 10 Encryption Algorithms Porta Table
To begin, write out your plain message
Encryption Algorithms Porta Table
To begin, write out your plain message
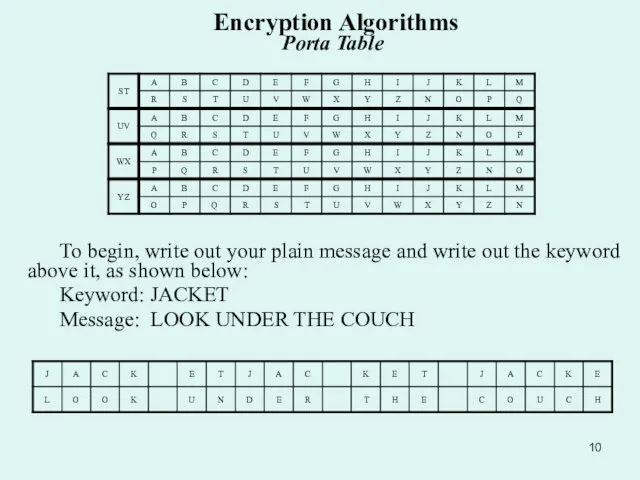
Keyword: JACKET
Message: LOOK UNDER THE COUCH
Слайд 11 The next step is to use the Porta table to create the
The next step is to use the Porta table to create the
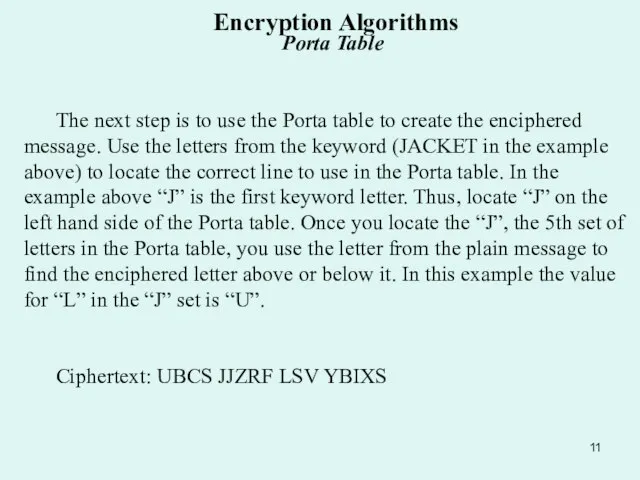
Ciphertext: UBCS JJZRF LSV YBIXS
Encryption Algorithms Porta Table
Слайд 12 Encryption Algorithms Vigenere Cipher
ABCDEFGHIJKLMNOPQRSTUVWXYZ
A ABCDEFGHIJKLMNOPQRSTUVWXYZ
B BCDEFGHIJKLMNOPQRSTUVWXYZA
C CDEFGHIJKLMNOPQRSTUVWXYZAB
D DEFGHIJKLMNOPQRSTUVWXYZABC
E EFGHIJKLMNOPQRSTUVWXYZABCD
F FGHIJKLMNOPQRSTUVWXYZABCDE
G GHIJKLMNOPQRSTUVWXYZABCDEF
H HIJKLMNOPQRSTUVWXYZABCDEFG
I IJKLMNOPQRSTUVWXYZABCDEFGH
J JKLMNOPQRSTUVWXYZABCDEFGHI
K KLMNOPQRSTUVWXYZABCDEFGHIJ
L LMNOPQRSTUVWXYZABCDEFGHIJK
M MNOPQRSTUVWXYZABCDEFGHIJKL
N NOPQRSTUVWXYZABCDEFGHIJKLM
O OPQRSTUVWXYZABCDEFGHIJKLMN
P PQRSTUVWXYZABCDEFGHIJKLMNO
Q QRSTUVWXYZABCDEFGHIJKLMNOP
R RSTUVWXYZABCDEFGHIJKLMNOPQ
S STUVWXYZABCDEFGHIJKLMNOPQR
T TUVWXYZABCDEFGHIJKLMNOPQRS
U UVWXYZABCDEFGHIJKLMNOPQRST
V VWXYZABCDEFGHIJKLMNOPQRSTU
W WXYZABCDEFGHIJKLMNOPQRSTUV
X XYZABCDEFGHIJKLMNOPQRSTUVW
Y YZABCDEFGHIJKLMNOPQRSTUVWX
Z ZABCDEFGHIJKLMNOPQRSTUVWXY
Example The encipher of the word CRYPTOGRAPHY
Encryption Algorithms Vigenere Cipher
ABCDEFGHIJKLMNOPQRSTUVWXYZ
A ABCDEFGHIJKLMNOPQRSTUVWXYZ
B BCDEFGHIJKLMNOPQRSTUVWXYZA
C CDEFGHIJKLMNOPQRSTUVWXYZAB
D DEFGHIJKLMNOPQRSTUVWXYZABC
E EFGHIJKLMNOPQRSTUVWXYZABCD
F FGHIJKLMNOPQRSTUVWXYZABCDE
G GHIJKLMNOPQRSTUVWXYZABCDEF
H HIJKLMNOPQRSTUVWXYZABCDEFG
I IJKLMNOPQRSTUVWXYZABCDEFGH
J JKLMNOPQRSTUVWXYZABCDEFGHI
K KLMNOPQRSTUVWXYZABCDEFGHIJ
L LMNOPQRSTUVWXYZABCDEFGHIJK
M MNOPQRSTUVWXYZABCDEFGHIJKL
N NOPQRSTUVWXYZABCDEFGHIJKLM
O OPQRSTUVWXYZABCDEFGHIJKLMN
P PQRSTUVWXYZABCDEFGHIJKLMNO
Q QRSTUVWXYZABCDEFGHIJKLMNOP
R RSTUVWXYZABCDEFGHIJKLMNOPQ
S STUVWXYZABCDEFGHIJKLMNOPQR
T TUVWXYZABCDEFGHIJKLMNOPQRS
U UVWXYZABCDEFGHIJKLMNOPQRST
V VWXYZABCDEFGHIJKLMNOPQRSTU
W WXYZABCDEFGHIJKLMNOPQRSTUV
X XYZABCDEFGHIJKLMNOPQRSTUVW
Y YZABCDEFGHIJKLMNOPQRSTUVWX
Z ZABCDEFGHIJKLMNOPQRSTUVWXY
Example The encipher of the word CRYPTOGRAPHY
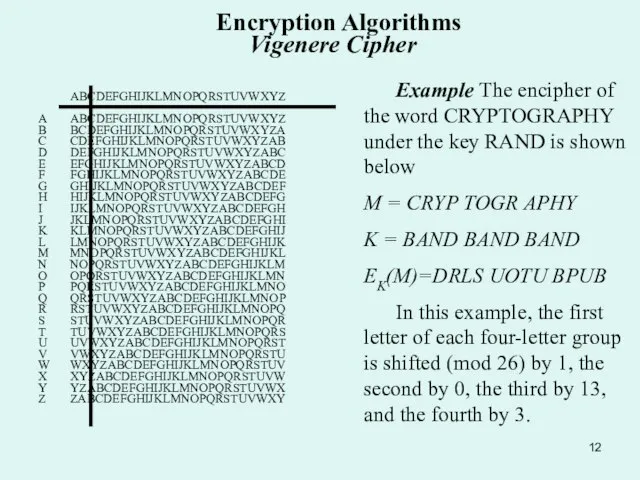
M = CRYP TOGR APHY
K = BAND BAND BAND
EK(M)=DRLS UOTU BPUB
In this example, the first letter of each four-letter group is shifted (mod 26) by 1, the second by 0, the third by 13, and the fourth by 3.
Слайд 13Encryption Algorithms Vigenere Cipher
The message "Wish you were here" can be
Encryption Algorithms Vigenere Cipher
The message "Wish you were here" can be
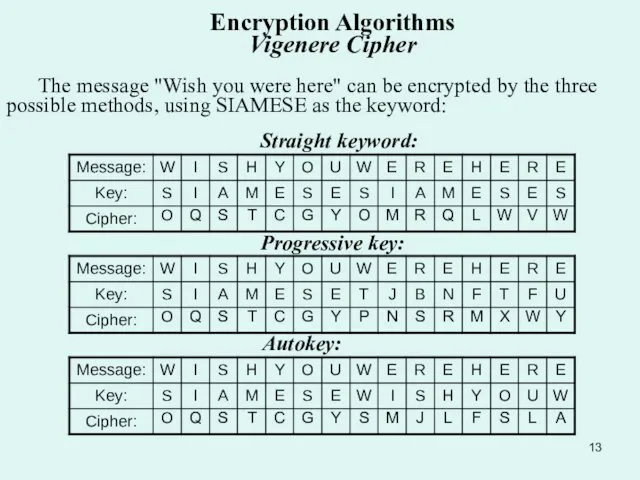
Straight keyword:
Progressive key:
Autokey:
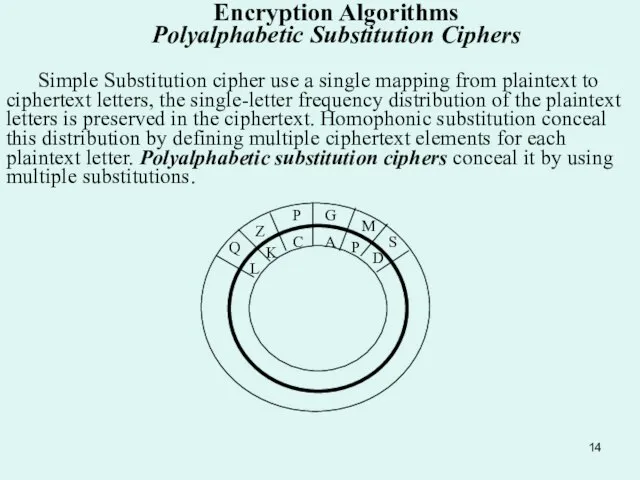
Слайд 14Encryption Algorithms Polyalphabetic Substitution Ciphers
Simple Substitution cipher use a single mapping from
Encryption Algorithms Polyalphabetic Substitution Ciphers
Simple Substitution cipher use a single mapping from
A
G
P
C
D
M
L
Q
Z
S
K
P
Слайд 15 In 1568, Alberty published a manuscript describing a cipher disk that defined
In 1568, Alberty published a manuscript describing a cipher disk that defined

Encryption Algorithms Polyalphabetic Substitution Ciphers
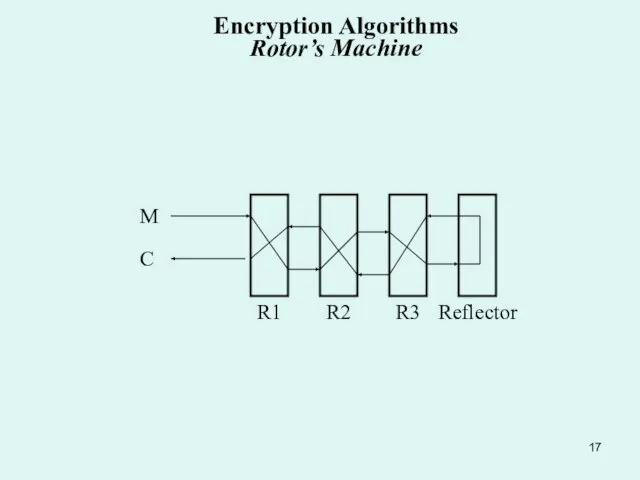
Слайд 16Encryption Algorithms Rotor’s Machines Bases
A rotor is a small disk of insulating
Encryption Algorithms Rotor’s Machines Bases
A rotor is a small disk of insulating

In Hebern machines, the contacts on the rotors were simply flat circles of metal; the machine had ball contacts on springs to make contact with them. This allowed the rotors to be put in upside down, for more possible keys. The Enigma, on the other hand, was built more cheaply; the rotors had plain metal contacts on one side, and spring contacts on the other. This almost halved the number of contacts needed, provided you didn't decide to use a new set of rotors.
A rotor provided a changing scrambled alphabet, by (you guessed it!) rotating. A rotor with 26 contacts on each side, each corresponding to a letter of the alphabet, that changed E to M before rotating would now change D to L (or F to N, depending on the direction in which it rotated), while E could become any other letter, depending on the way the different wire went that was now brought into position to encipher it.
Слайд 17R3
R2
R1
Reflector
C
M
Encryption Algorithms Rotor’s Machine
R3
R2
R1
Reflector
C
M
Encryption Algorithms Rotor’s Machine
 История возникновения Всесоюзного физкультурного комплекса ГТО
История возникновения Всесоюзного физкультурного комплекса ГТО Железо – элемент побочной подгруппы
Железо – элемент побочной подгруппы Монтаж ОТИС
Монтаж ОТИС Русанова Наталья Леонидовна
Русанова Наталья Леонидовна Электро-диффузионные явления
Электро-диффузионные явления  Отдельностоящие плиты. Новинки 2011
Отдельностоящие плиты. Новинки 2011 Мир отношений. Отношения с самим собой, с миром и людьми
Мир отношений. Отношения с самим собой, с миром и людьми 50 наиболее востребованных на рынке труда, новых и перспективных профессий, требующих среднего профессионального образования
50 наиболее востребованных на рынке труда, новых и перспективных профессий, требующих среднего профессионального образования Текстиль
Текстиль Основные сюжеты и образы иконописи: иконы Праздников
Основные сюжеты и образы иконописи: иконы Праздников Публичный отчет директора гимназии №1за 2011-2012 учебный год
Публичный отчет директора гимназии №1за 2011-2012 учебный год Виды скульптуры по назначению
Виды скульптуры по назначению История России 10 класс
История России 10 класс Предложение фирмы «Проектика» по производству и поставке торгового оборудования Рязань 2012 Россия, 390029, г.Рязань, ул.Чкалова, 68А Тел
Предложение фирмы «Проектика» по производству и поставке торгового оборудования Рязань 2012 Россия, 390029, г.Рязань, ул.Чкалова, 68А Тел Презентация на тему Сохранение психологического и физического здоровья педагога
Презентация на тему Сохранение психологического и физического здоровья педагога  Специализированные учреждения ООН в современной системе международных отношений
Специализированные учреждения ООН в современной системе международных отношений Типы организационных теорий и их принципы. (Тема 2)
Типы организационных теорий и их принципы. (Тема 2) Отряды птиц
Отряды птиц Социальные игры Презентация для рекламодателей. - презентация
Социальные игры Презентация для рекламодателей. - презентация ТиТСП 3-1
ТиТСП 3-1 Wearable продукт
Wearable продукт Сигары
Сигары «1С:Предприятие 8. Оперативная печать»
«1С:Предприятие 8. Оперативная печать» Alles rund um die Geschichte und Freizeitorte Passau
Alles rund um die Geschichte und Freizeitorte Passau ОЦЕНКА ДОСТИЖЕНИЯ РЕЗУЛЬТАТОВ ОБУЧЕНИЯ ЧЕРЕЗ ИЗМЕРЕНИЕ ИЗМЕНЕНИЙ В ОБУЧАЮЩЕМСЯ Е. Б. Бухарова Директор Института экономики, уп
ОЦЕНКА ДОСТИЖЕНИЯ РЕЗУЛЬТАТОВ ОБУЧЕНИЯ ЧЕРЕЗ ИЗМЕРЕНИЕ ИЗМЕНЕНИЙ В ОБУЧАЮЩЕМСЯ Е. Б. Бухарова Директор Института экономики, уп Қазіргі замандағы әлемдік діндер
Қазіргі замандағы әлемдік діндер Грантрайдинг: упаковка проекта
Грантрайдинг: упаковка проекта Презентация на тему Борьба организма с инфекцией Иммунитет
Презентация на тему Борьба организма с инфекцией Иммунитет