Содержание
- 2. Contents Introduction: Data security. Fundamental concepts of cryptography. Transposition and Substitution ciphers: Simple transposition. Product cipher.
- 3. Contents cont. RSA Cipher: Riverst, Shamir and Adleman public key cipher. Practical aspects. Linear Feedback Shift
- 4. Contents cont. Digital signature: Main definition. Digital signature based on Symmetric cryptosystem. Hash Functions: Message authentication
- 5. Contents Cont. Physical Cryptography: Physical unclonable function (PUF). Arbiter PUF. Ring oscillator PUF. SRAM based PUF.
- 6. 1. Романец, Ю.В. Защита информации в компьютерных системах и сетях / Ю.В. Романец, П.А. Тимофеев, В.Ф.
- 7. Cryptography is the science and study of secret writing. A cipher is a secret method of
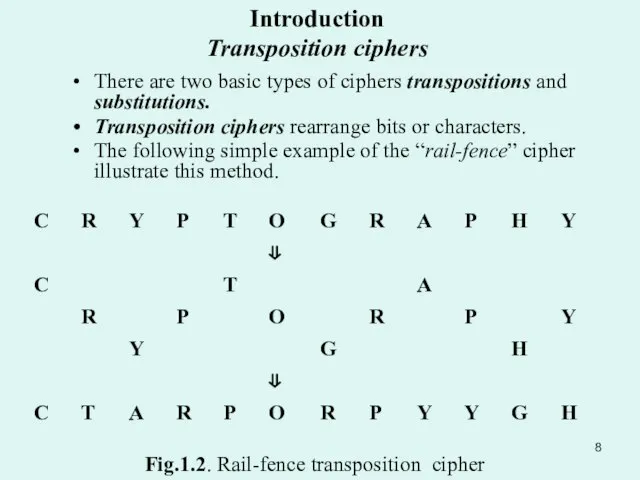
- 8. There are two basic types of ciphers transpositions and substitutions. Transposition ciphers rearrange bits or characters.
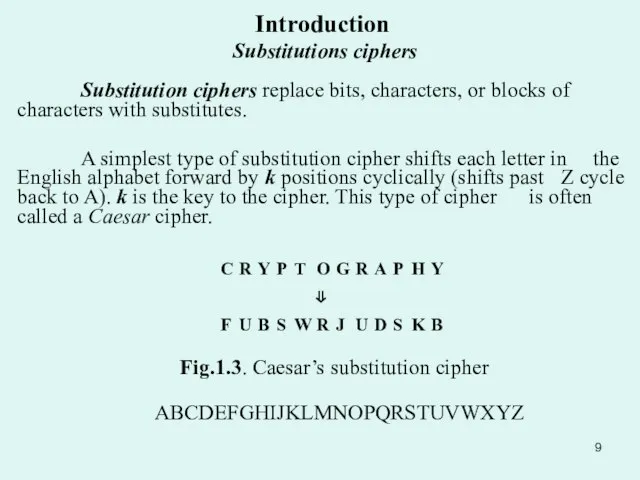
- 9. Introduction Substitutions ciphers Substitution ciphers replace bits, characters, or blocks of characters with substitutes. A simplest
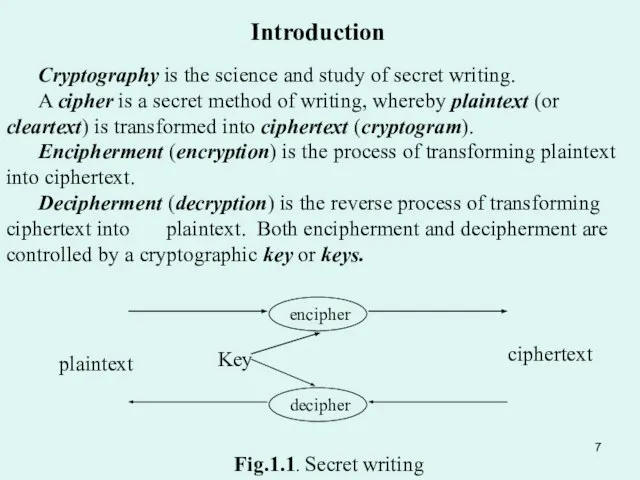
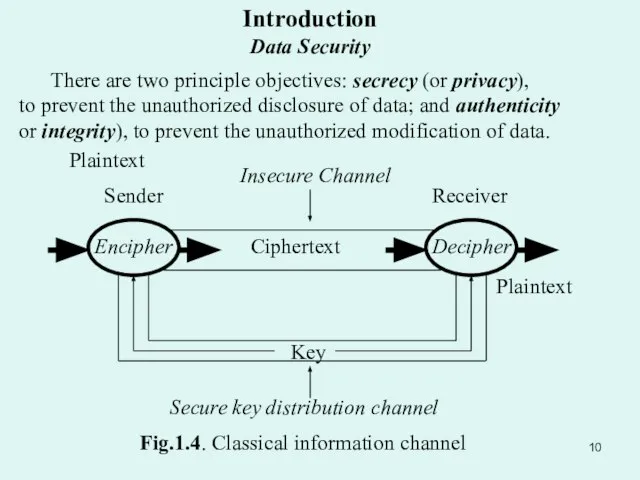
- 10. Plaintext Fig.1.4. Classical information channel Introduction Data Security There are two principle objectives: secrecy (or privacy),
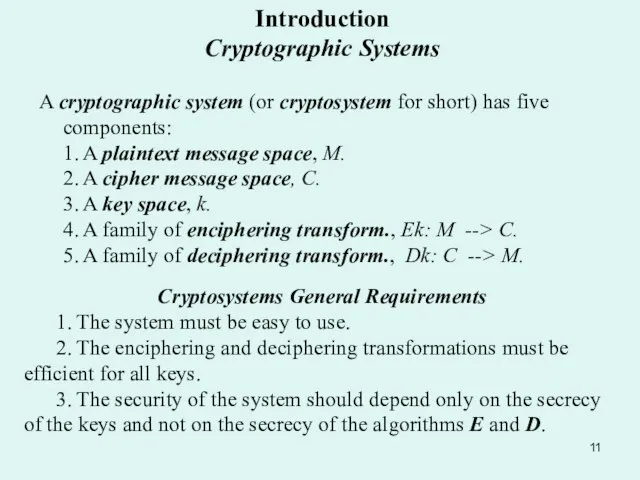
- 11. Introduction Cryptographic Systems A cryptographic system (or cryptosystem for short) has five components: 1. A plaintext
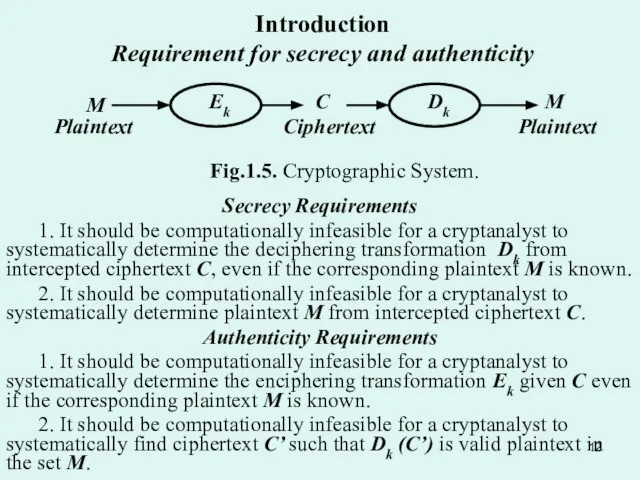
- 12. Introduction Requirement for secrecy and authenticity Secrecy Requirements 1. It should be computationally infeasible for a
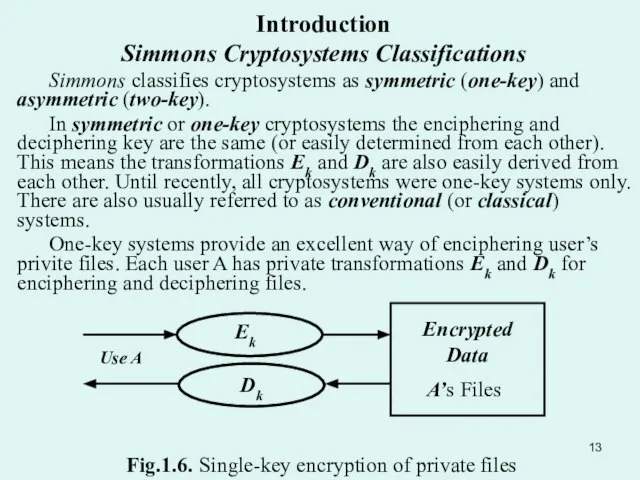
- 13. Introduction Simmons Cryptosystems Classifications Simmons classifies cryptosystems as symmetric (one-key) and asymmetric (two-key). In symmetric or
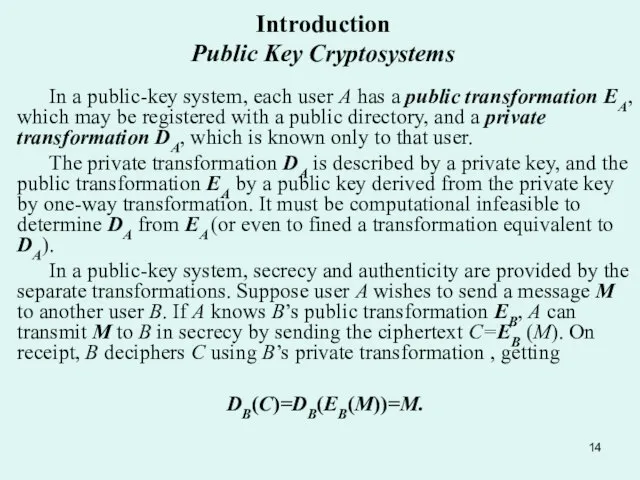
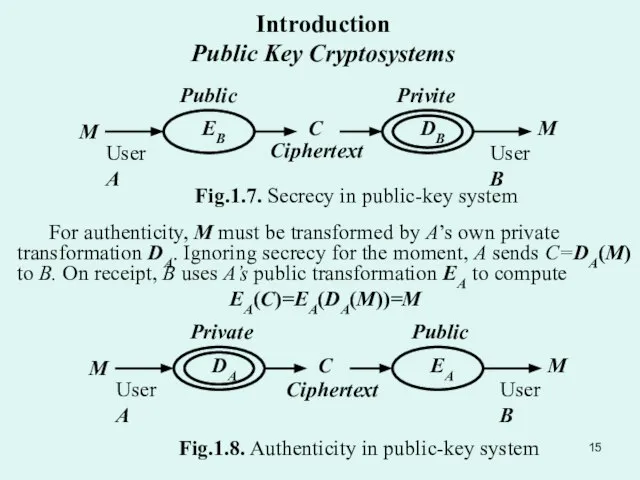
- 14. In a public-key system, each user A has a public transformation EA, which may be registered
- 15. Introduction Public Key Cryptosystems For authenticity, M must be transformed by A’s own private transformation DA.
- 17. Скачать презентацию





 IZ_T_1
IZ_T_1 М.Е.Салтыков-Щедрин. «Повесть о том, как один мужик двух генералов прокормил». Нравственные пороки общества»
М.Е.Салтыков-Щедрин. «Повесть о том, как один мужик двух генералов прокормил». Нравственные пороки общества» В гостях у При-, Пре-
В гостях у При-, Пре- Усадьба И. С. Тургенева в Буживале
Усадьба И. С. Тургенева в Буживале Структура содержания общего образования
Структура содержания общего образования День мира
День мира Университет будущего
Университет будущего “ДРУЗІ”
“ДРУЗІ” Творческая лаборатория слова.
Творческая лаборатория слова. Нормативные документы, регулирующие финансовый рынок в РФ
Нормативные документы, регулирующие финансовый рынок в РФ Использование нормативно-технических документов студентами в дипломных и магистерских работах
Использование нормативно-технических документов студентами в дипломных и магистерских работах Скорости в живой природе
Скорости в живой природе Доченька, поздравляем от всего сердца с двадцатилетием
Доченька, поздравляем от всего сердца с двадцатилетием Школа №12132
Школа №12132 Семейное хозяйство
Семейное хозяйство Опыт проведения куров повышения квалификации для инженеров-конструкторов(АСПО- SCAD 13 лет дружбы на рынке САПР) И.И.Рыбина (ЗАО «
Опыт проведения куров повышения квалификации для инженеров-конструкторов(АСПО- SCAD 13 лет дружбы на рынке САПР) И.И.Рыбина (ЗАО « Кутузов и Наполеон в романе Л.Н. Толстого «Война и мир»
Кутузов и Наполеон в романе Л.Н. Толстого «Война и мир» Футуризм в искусстве
Футуризм в искусстве Техническое регулирование в строительстве
Техническое регулирование в строительстве Скрипты для продажи EMS и первого класса. Почта России
Скрипты для продажи EMS и первого класса. Почта России Использование минуток здоровья в ДОУ
Использование минуток здоровья в ДОУ Особенности обучения ученика и студента
Особенности обучения ученика и студента Этнос и нация
Этнос и нация Елизаветинское барокко
Елизаветинское барокко Скоринг: как банки и МФО решают, давать ли вам кредит
Скоринг: как банки и МФО решают, давать ли вам кредит c710641808604d52a46259ae4ab8d849
c710641808604d52a46259ae4ab8d849 Презентация на тему Международные реки
Презентация на тему Международные реки  Публичный доклад о работе школы за 2008-2009 учебный год
Публичный доклад о работе школы за 2008-2009 учебный год