Содержание
- 2. Contents Main Concepts Control Measures Common threats and challenges Database Security Priority Areas
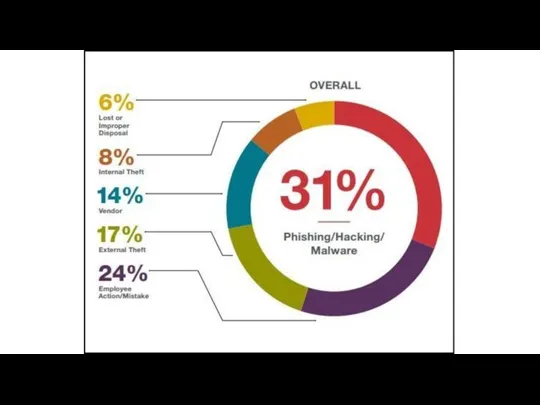
- 3. 1. Main Concepts Types of Security Threats to Databases Database Security - Part of a Common
- 4. 1. Types of Security Database Security Issues
- 5. Company that we have analyzed
- 6. Kaspi+Egov
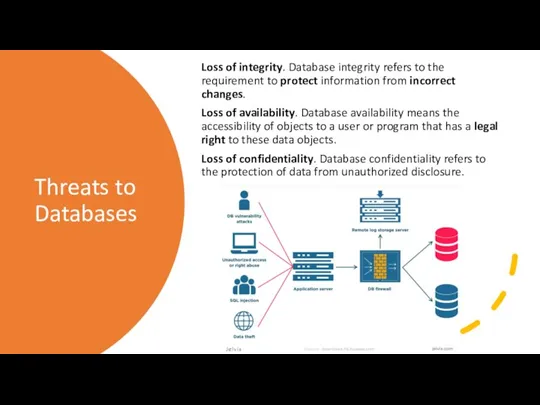
- 7. Threats to Databases Loss of integrity. Database integrity refers to the requirement to protect information from
- 8. Database security must address and protect the following: The data in the database The database management
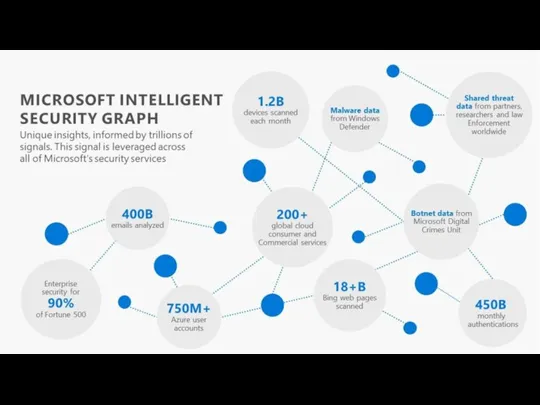
- 9. 2. Control Measures
- 10. Access control It includes two main components: authentication and authorization. Authentication is a method of verifying
- 11. 5. Data encryption Database encryption is the process of converting data, within a database, in plain
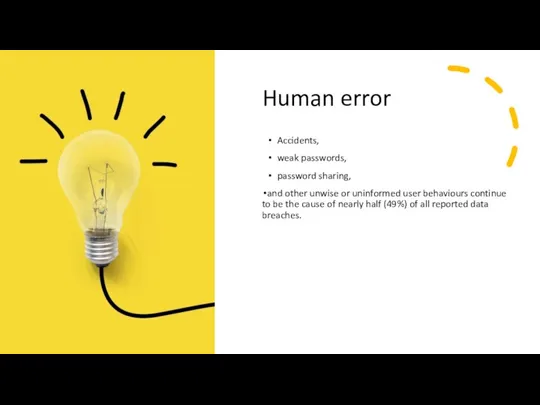
- 12. Common threats and challenges 1. Human error 2. Exploitation of database software vulnerabilities 3. Denial of
- 15. Human error Accidents, weak passwords, password sharing, and other unwise or uninformed user behaviours continue to
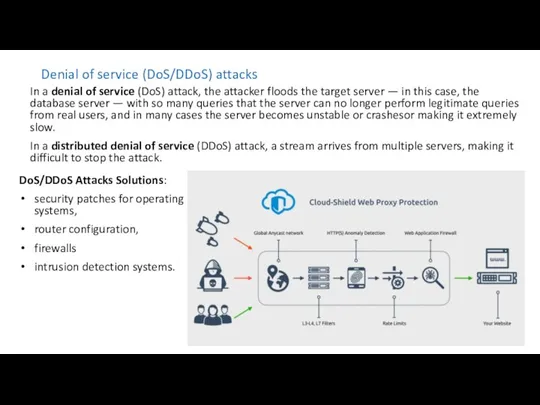
- 16. Denial of service (DoS/DDoS) attacks In a denial of service (DoS) attack, the attacker floods the
- 17. Malware Malware is software written specifically to exploit vulnerabilities or otherwise cause damage to the database.
- 18. 8. Attacks on backups Threats are compounded by the following: Growing data volumes: Data capture, storage,
- 19. Encryption, software and applications Encryption: ALL data—including data in the database, and credential data—should be protected
- 20. Backup security: All backups, copies, or images of the database must be subject to the same
- 22. Скачать презентацию












 Луноход-1. Первооткрыватель планетного туризма
Луноход-1. Первооткрыватель планетного туризма Интерфейсы на Java
Интерфейсы на Java Основы алгоритмизации и программирования. Лекция 9
Основы алгоритмизации и программирования. Лекция 9 Сайт корректировки
Сайт корректировки Архивация
Архивация Правила оформления слайда
Правила оформления слайда Критерии оценки блогеров, полезные сервисы (LiveDune, Popsters, Epicdetect)
Критерии оценки блогеров, полезные сервисы (LiveDune, Popsters, Epicdetect) Кантриболз .История
Кантриболз .История Информационные технологии в психологии. Анализ Интернет-ресурсов
Информационные технологии в психологии. Анализ Интернет-ресурсов Автоматическая система теплопотребления и погодного регулирования в ИТП многоквартирного дома
Автоматическая система теплопотребления и погодного регулирования в ИТП многоквартирного дома Изучение графического движка Unity на основе игры
Изучение графического движка Unity на основе игры Web-технологии: PHP, MySQL, AJAX
Web-технологии: PHP, MySQL, AJAX Безопасный интернет
Безопасный интернет Современные тенденции развития информационных технологий. Принципы машинного обучения, нейронных сетей
Современные тенденции развития информационных технологий. Принципы машинного обучения, нейронных сетей Сервисы для создания контента в соцсетях
Сервисы для создания контента в соцсетях Лекция 6 - Реляционная модель данных_Часть 2_Операции над отношениями
Лекция 6 - Реляционная модель данных_Часть 2_Операции над отношениями Компьютерные технологии в энергомашиностроении
Компьютерные технологии в энергомашиностроении Низкоуровневое программирование. Интерпретация, компиляция, компоновка
Низкоуровневое программирование. Интерпретация, компиляция, компоновка CASE-технологии
CASE-технологии Зри в корень – пиши грамотно
Зри в корень – пиши грамотно Обзор СЭД/ЕСМ
Обзор СЭД/ЕСМ Модель OSI
Модель OSI Возможные применения теории фракталов в криптографии
Возможные применения теории фракталов в криптографии Таблицы Ишихары. Тестирование цветового восприятия
Таблицы Ишихары. Тестирование цветового восприятия Защита домашней сети
Защита домашней сети Мир без интернета
Мир без интернета JavaScript История развития
JavaScript История развития Безопасный интернет. Материалы к уроку безопасного интернета для 1-4 классов общеобразовательной средней школы
Безопасный интернет. Материалы к уроку безопасного интернета для 1-4 классов общеобразовательной средней школы