Слайд 2DDoS
One of the most common ways to mount a Distributed Denial of

Service attacks is done via networks of zombie computers taking instructions from a central point
Early net were controlled via proprietary software written by the network owner
Today they are mostly controlled by an IRC channel
This makes it easier to control the network and easier for the owner to hide
Слайд 3IRC
Internet Relay Chat
Jarkko Oikarinen; 1988
Real time Internet Chat (synchronous conferencing)
Designed for

group conferencing
Can do private one-to-one messaging
TCP Port 195 but usually run on 6667 to avoid having to run the server as root.
RFC 1459 also RFCs 2810-2813
Network is usually arranged in an acyclic graph (tree)
Messages only need go down the required branches
Communications are facilitated via channels
Channels can be global to all servers or local to a single server in the network
Слайд 4IRC (more)
Users and Channels have modes
User Modes
i – invisible, cannot be seen
without a common channel
or knowing the exact name
s - Receives server notices
w - Receives wallops
o - ser is an IRC operator (ircop)
Слайд 5IRC (more)
Users and Channels have modes
Channel Modes
o– channel operator
p – private

channel
s – secret channel
i – invite only
t – topic set by channel operator
n - Users cannot send external messages from outside
the channel
m – channel is moderated
l – limited number of users
b – hostmasks (IRC addresses) not allowed on channel
v – gives user voice status
k – sets a channel key
Слайд 6IRC (more)
A user who creates a channel becomes the channel operator
operators have
more privileges than users
IRC Bots
Bots are a special type of IRC client and are often used for performing automated administrative tasks for the net
treated as a regular user by the servers
but could be a trojan horse installed on a user machine; this constitutes a zombie
Слайд 7Zombies
Network connected computers compromised by a hacker, a virus or a trojan
horse program
Owners of zombie computers are usually unaware their machine is compromised
Most spam is sent from zombie computers
Used as the bots in many BotNets
Used to mount large scale DDoS attacks
Слайд 8Bot Uses
DDos
Spamming
Sniffing and Keylogging
Identity Theft
Hosting of Illegal Software (or content)
Слайд 9Types of Bots
GT-Bot – based on windows IRC client mIRC
uses core to
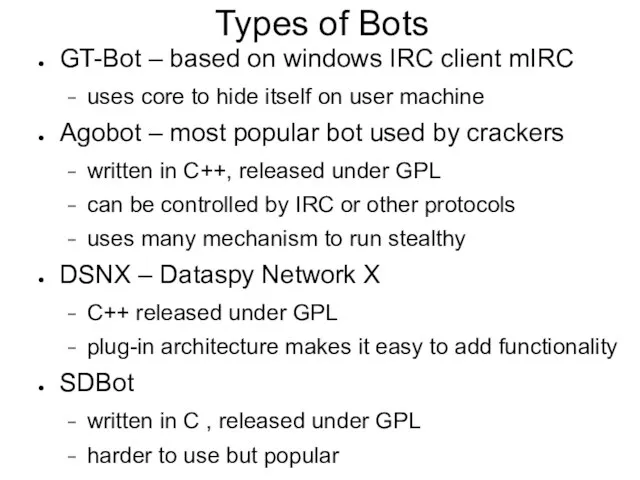
hide itself on user machine
Agobot – most popular bot used by crackers
written in C++, released under GPL
can be controlled by IRC or other protocols
uses many mechanism to run stealthy
DSNX – Dataspy Network X
C++ released under GPL
plug-in architecture makes it easy to add functionality
SDBot
written in C , released under GPL
harder to use but popular
Слайд 10An Attack
Attacker spreads a trojan horse to infect various hosts
hosts become zombies

and connect to IRC server on a specific channel as regular user users
channel may be encrypted or open
IRC Server can be on a public network or installed on one of the compromised hosts
Bots listen to the channel for instructions from the operator
operator instructs the net to do “it's stuff”









 Россия - родина моя!
Россия - родина моя! Колебания Солнца и звезд и температурные волны в фотосфере
Колебания Солнца и звезд и температурные волны в фотосфере Презентация на тему ХИМИЯ - это наука о веществах и их превращениях
Презентация на тему ХИМИЯ - это наука о веществах и их превращениях  Организация и анализ приемки товаров по количеству и качеству в розничной торговле на примере АО ТД Южный
Организация и анализ приемки товаров по количеству и качеству в розничной торговле на примере АО ТД Южный Кабинет иностранного языка № 306
Кабинет иностранного языка № 306 Традиции и обычаи Японии
Традиции и обычаи Японии Методическое объединение учителей иностранных языков
Методическое объединение учителей иностранных языков Интеллектуал
Интеллектуал ДОМ СОЛНЦА
ДОМ СОЛНЦА Ассортимент магазина Fea tLab
Ассортимент магазина Fea tLab Синдром Иценко-Кушинга
Синдром Иценко-Кушинга Стрижка, окрашивание и укладка волос
Стрижка, окрашивание и укладка волос Презентация на тему Н-НН в суффиксах причастий
Презентация на тему Н-НН в суффиксах причастий  Центр образовательных услуг
Центр образовательных услуг Urok_161-162_Tekhnologia_uboya_i_pererabotki
Urok_161-162_Tekhnologia_uboya_i_pererabotki Красная книга Ростовской области. Животные
Красная книга Ростовской области. Животные Принятие управленческих решений
Принятие управленческих решений Сберегший душу потеряет, а потерявший – сбережет. Евангелие от Иоанна 12:24-26.
Сберегший душу потеряет, а потерявший – сбережет. Евангелие от Иоанна 12:24-26. Микены и Троя
Микены и Троя Хлеб. Откуда он берется?
Хлеб. Откуда он берется? Ключевые особенности и отличия федеральных государственных образовательных стандартов (ФГОС) от государственных образовательны
Ключевые особенности и отличия федеральных государственных образовательных стандартов (ФГОС) от государственных образовательны Mitsubishi Grandis
Mitsubishi Grandis Духовно-нравственное здоровье нации и будущее наших детей
Духовно-нравственное здоровье нации и будущее наших детей МЕЖДУНАРОДНЫЙ КОМИТЕТКРАСНОГО КРЕСТА
МЕЖДУНАРОДНЫЙ КОМИТЕТКРАСНОГО КРЕСТА Многогранники
Многогранники "Карагайский бор"
"Карагайский бор" Конкурс «Лучший следопыт» в области геометрии.
Конкурс «Лучший следопыт» в области геометрии. Список документов, для признания нуждающимися в улучшении жилищных условий
Список документов, для признания нуждающимися в улучшении жилищных условий