Содержание
- 2. Diffie-Hellman Key Exchange The Diffie-Hellman protocol allows 2 people to use random values and yet each
- 3. Alice and Bob need to agree on a key to use in a symmetric key cryptosystem.
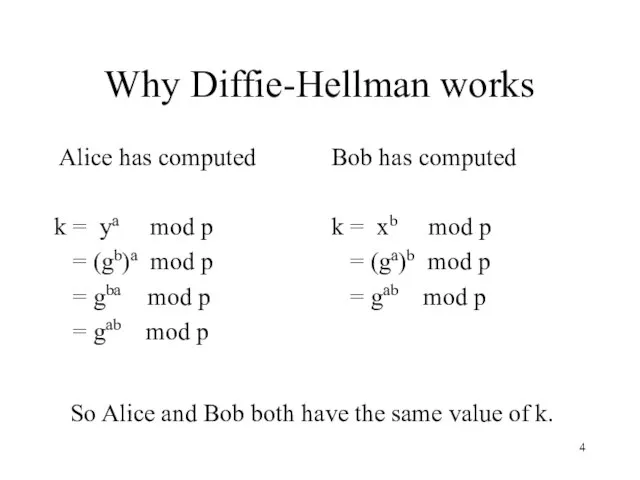
- 4. Why Diffie-Hellman works Alice has computed k = ya mod p = (gb)a mod p =
- 5. How secure is it? We assume that cryptanalyst Charles knows the values of p and g
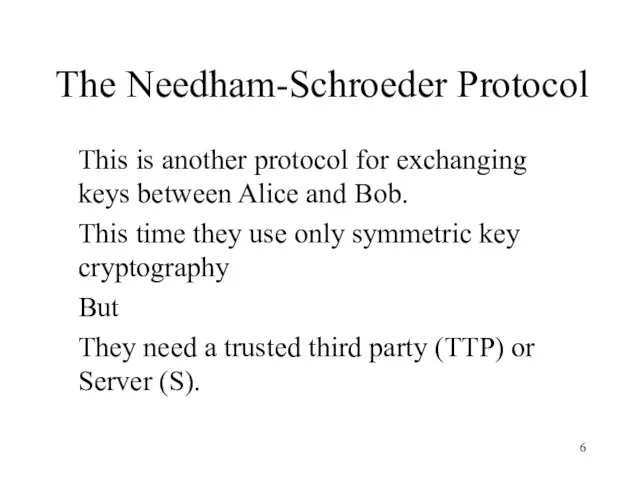
- 6. The Needham-Schroeder Protocol This is another protocol for exchanging keys between Alice and Bob. This time
- 7. Alice and the server have a key KAS Bob and the server have a key KBS
- 8. Alice sends the server S the names of Alice and Bob to request that a session
- 9. Alice uses key KAS to decrypt the items sent to her in step 2. Alice now
- 10. Needham-Schroeder A S: A,B 2. S A: eKAS(B, KAB, eKBS(A, KAB)) Alice decrypts to get B,
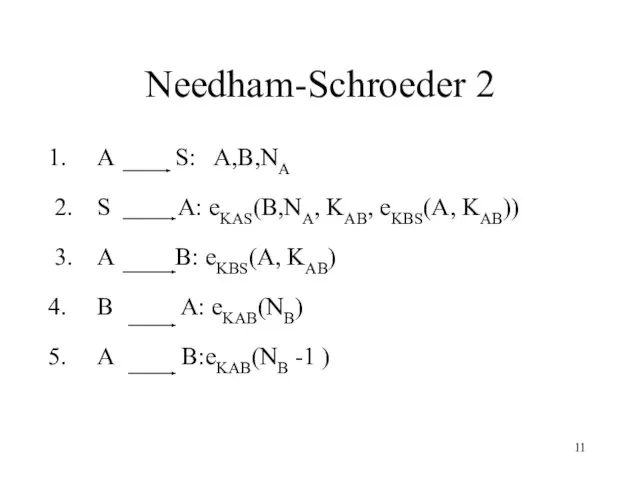
- 11. Needham-Schroeder 2 A S: A,B,NA 2. S A: eKAS(B,NA, KAB, eKBS(A, KAB)) 3. A B: eKBS(A,
- 12. Certificates A certificate consists of a public key together with an identification of the key user.
- 13. The CA guarantees the link between the user and the public key by digitally signing a
- 14. X.509 Standard Bob generates a document containing his relevant information and presents himself with this document
- 16. Скачать презентацию










 Реализация проекта. План проекта мебель-трансформер
Реализация проекта. План проекта мебель-трансформер Урок презентация на тему Храм Василия Блаженного
Урок презентация на тему Храм Василия Блаженного  EISBERG MODELL
EISBERG MODELL «Преобразование транспортно-коммуникационных пространств городов. Санкт-Петербург. Площадь Балтийского вокзала»
«Преобразование транспортно-коммуникационных пространств городов. Санкт-Петербург. Площадь Балтийского вокзала» История одного города
История одного города Опыт использования учебников «Органическая химия» и «Общая химия» для обучения школьников на профильном уровне
Опыт использования учебников «Органическая химия» и «Общая химия» для обучения школьников на профильном уровне Презентация на тему Секреты долголетия
Презентация на тему Секреты долголетия Профсоюзы
Профсоюзы Налоговая реформа княгини Ольги
Налоговая реформа княгини Ольги Здоровьесберегающие образовательные технологии в педиатрии
Здоровьесберегающие образовательные технологии в педиатрии  Управление качеством образования на основе совершенствования научно-методической работы
Управление качеством образования на основе совершенствования научно-методической работы Практика стратегического анализа в российских городах
Практика стратегического анализа в российских городах МИСПИ(1)
МИСПИ(1) Анна Ахматова
Анна Ахматова Ребёнок один в машине
Ребёнок один в машине Китайские картины
Китайские картины Презентация на тему Требования к оформлению презентации
Презентация на тему Требования к оформлению презентации Требования к курсовой работе
Требования к курсовой работе Быстрая настройка рекламы в свадебной сфере!
Быстрая настройка рекламы в свадебной сфере! Калькулювання виробничой собівартості продукціи (робіт, послуг)
Калькулювання виробничой собівартості продукціи (робіт, послуг) СКОРО В ПРОДАЖЕ Артикул: 116012 Размер: 56,62 Лот 8 шт. Цвет: желтый, розовый, голубой, белый Полотно: капитон Примечания: застежка – кнопки
СКОРО В ПРОДАЖЕ Артикул: 116012 Размер: 56,62 Лот 8 шт. Цвет: желтый, розовый, голубой, белый Полотно: капитон Примечания: застежка – кнопки Street-Art et immeubles peints
Street-Art et immeubles peints Выбор ниши
Выбор ниши Презентация на тему Детство Пушкина (9 класс)
Презентация на тему Детство Пушкина (9 класс)  Полевые транзисторы. Самостоятельная работа
Полевые транзисторы. Самостоятельная работа Презентация на тему Жизнь и творчество А.Т. Твардовского
Презентация на тему Жизнь и творчество А.Т. Твардовского  Модерн в природе
Модерн в природе Закономерности эволюции
Закономерности эволюции