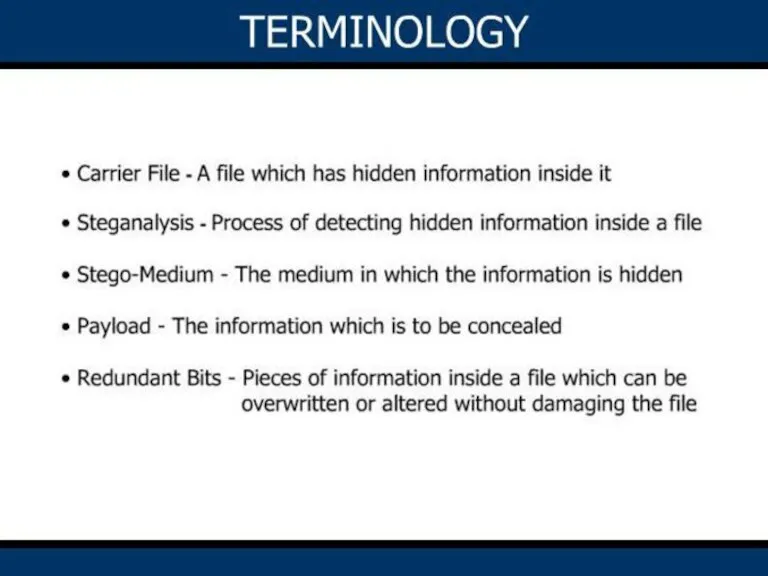
Содержание
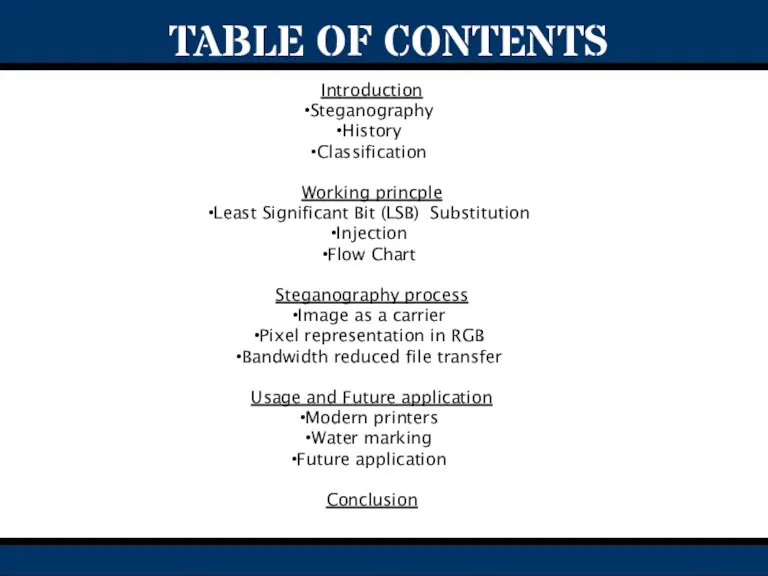
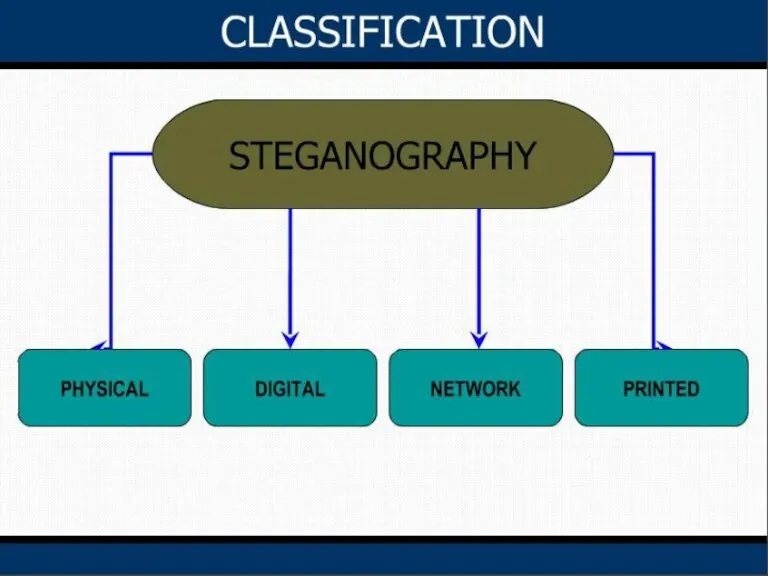
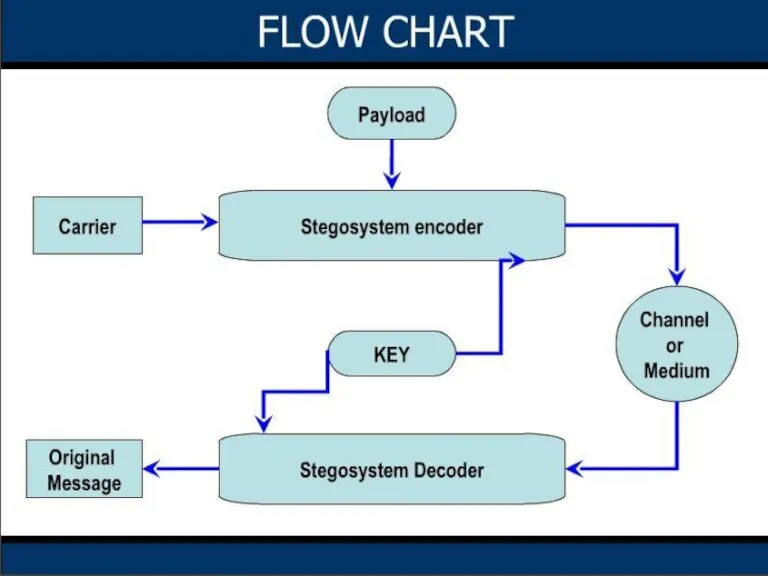
- 2. Introduction Steganography History Classification Working princple Least Significant Bit (LSB) Substitution Injection Flow Chart Steganography process
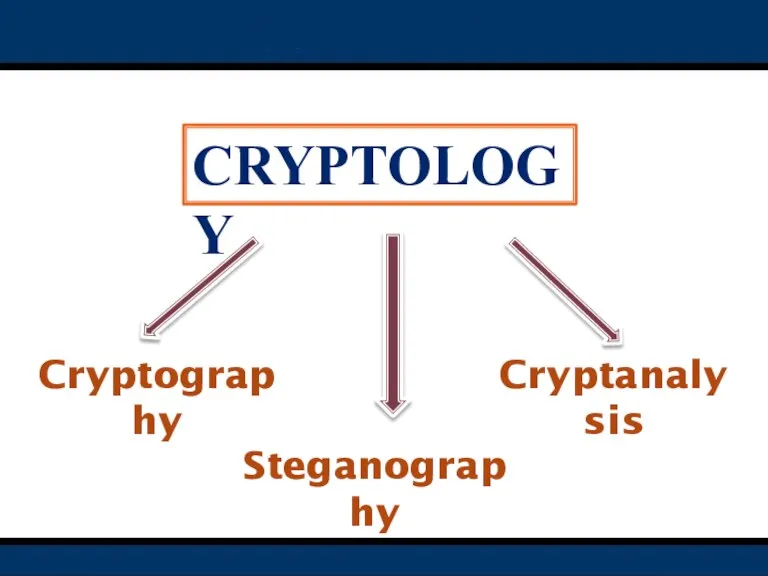
- 3. Cryptology Cryptography Cryptanalysis Steganography
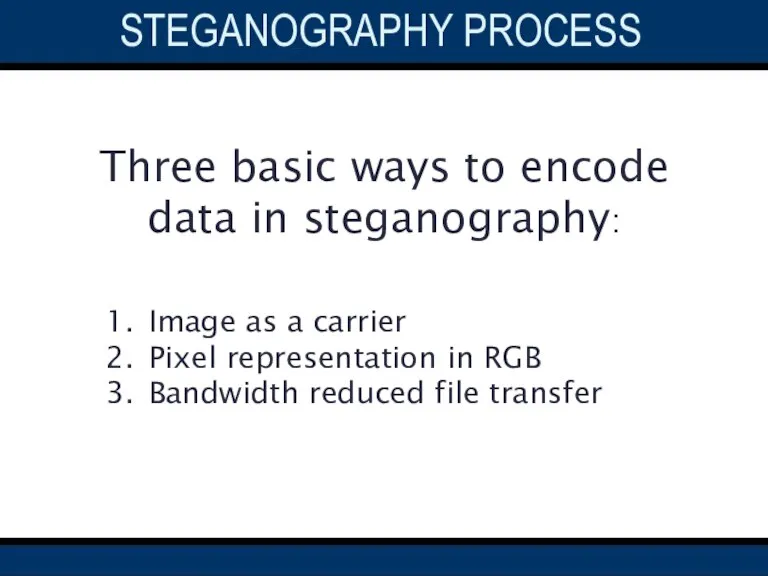
- 12. STEGANOGRAPHY process Three basic ways to encode data in steganography: Image as a carrier Pixel representation
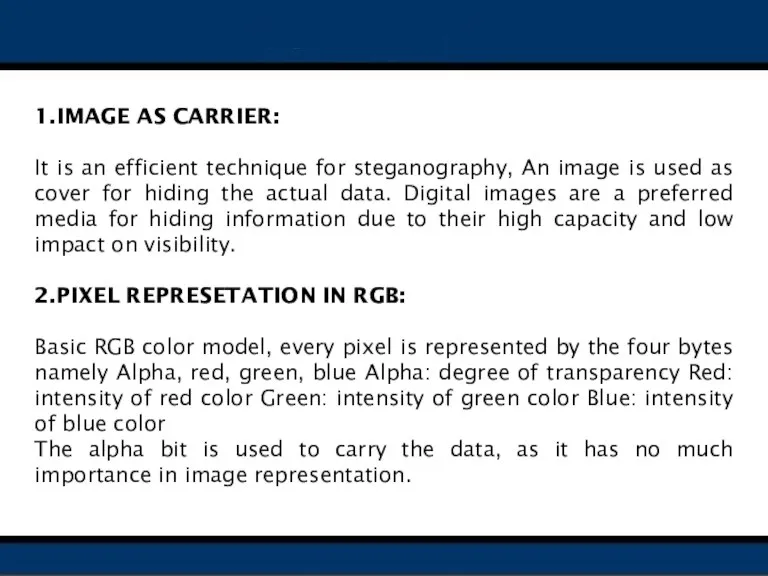
- 13. 1.IMAGE AS CARRIER: It is an efficient technique for steganography, An image is used as cover
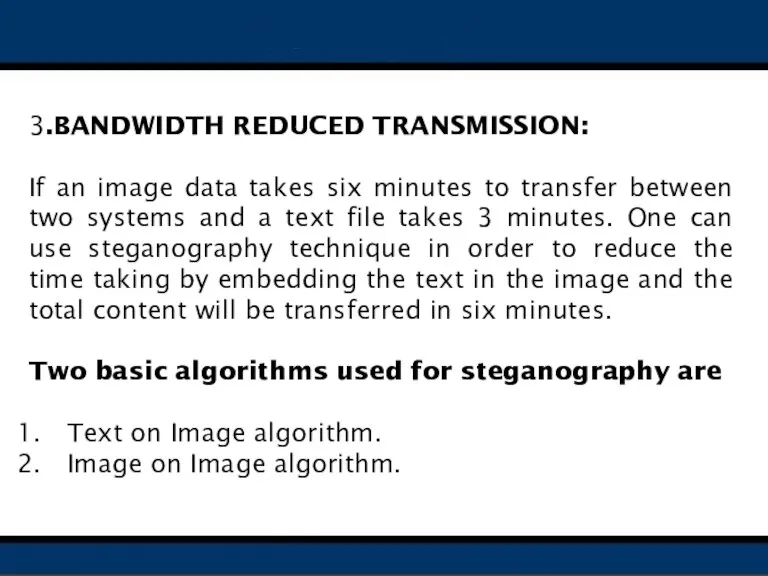
- 14. 3.BANDWIDTH REDUCED TRANSMISSION: If an image data takes six minutes to transfer between two systems and
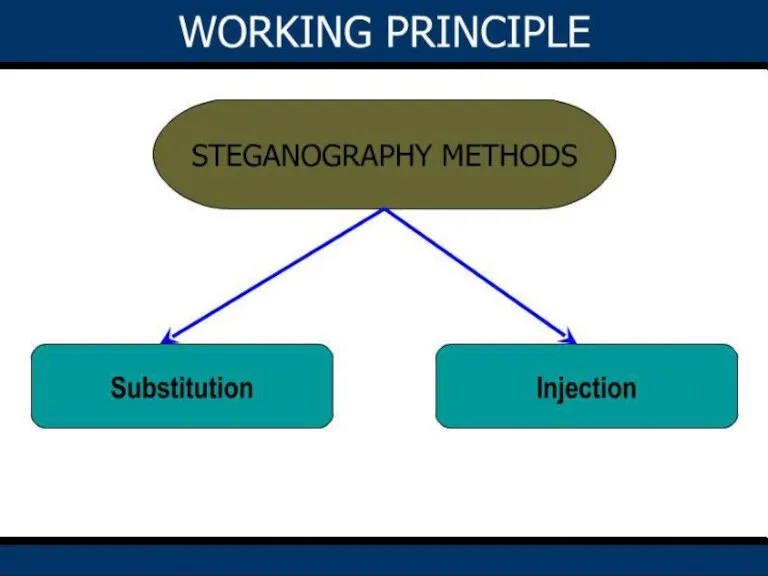
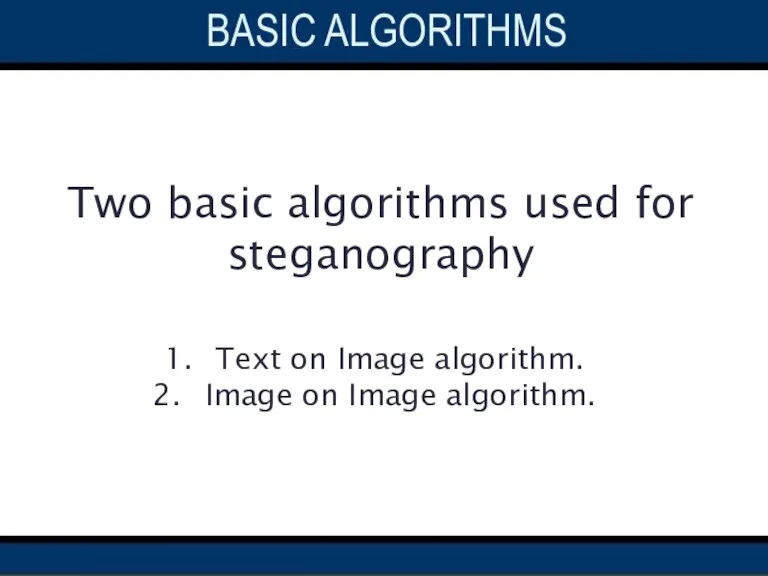
- 15. Two basic algorithms used for steganography Text on Image algorithm. Image on Image algorithm. BASIC ALGORITHMS
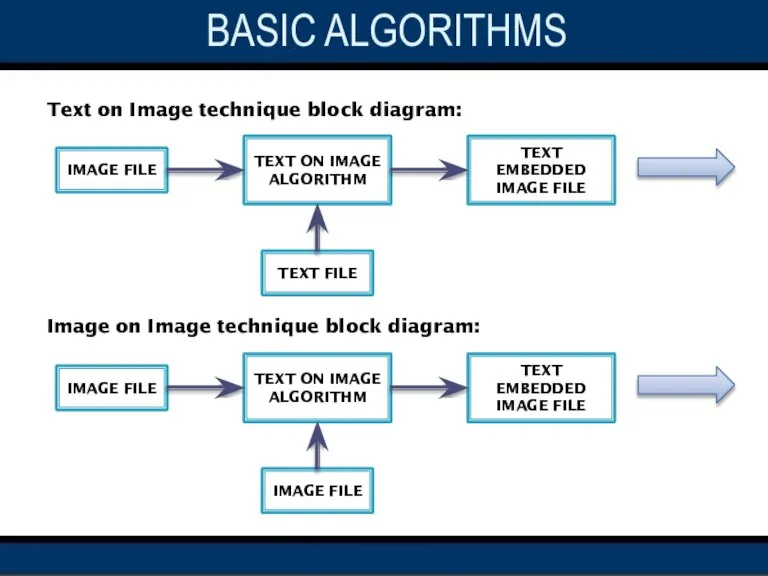
- 16. Text on Image technique block diagram: Image on Image technique block diagram: IMAGE FILE TEXT ON
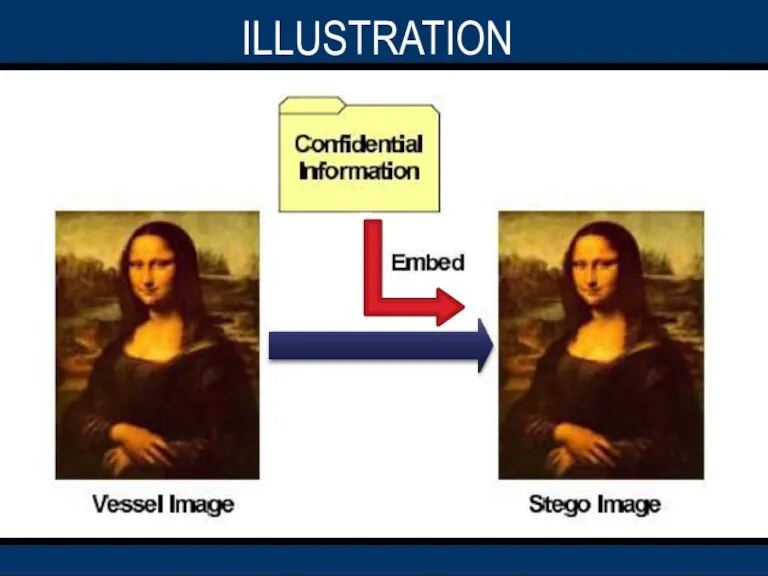
- 17. ILLUSTRATION
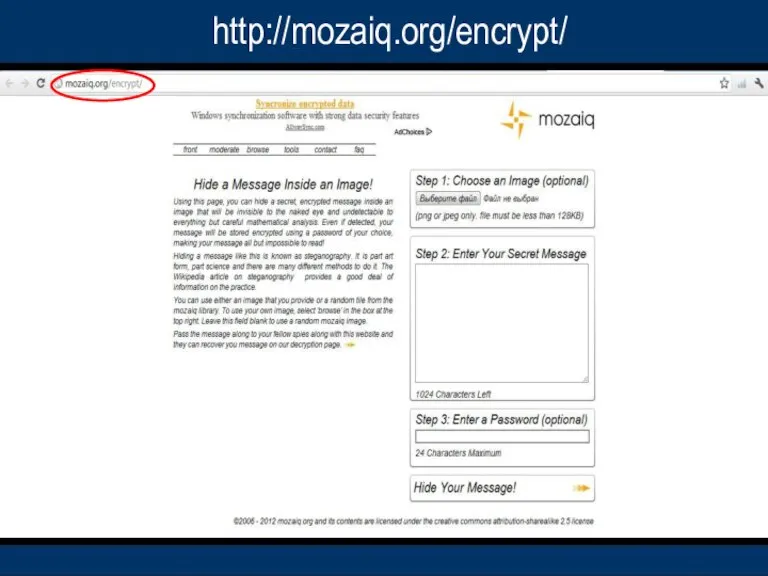
- 19. http://mozaiq.org/encrypt/
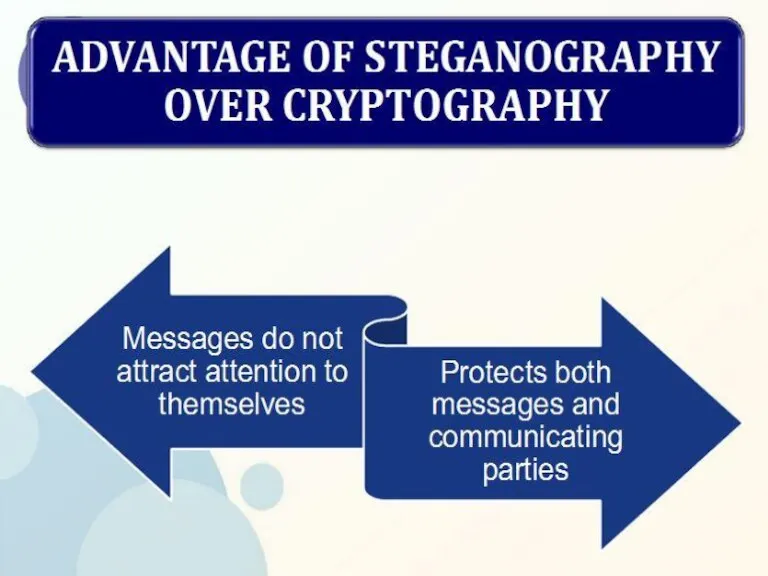
- 20. ADVANTAGES Internet privacy. Secret communication between the organizations like boarder security force and defense organization. Effective
- 21. ADVANTAGES
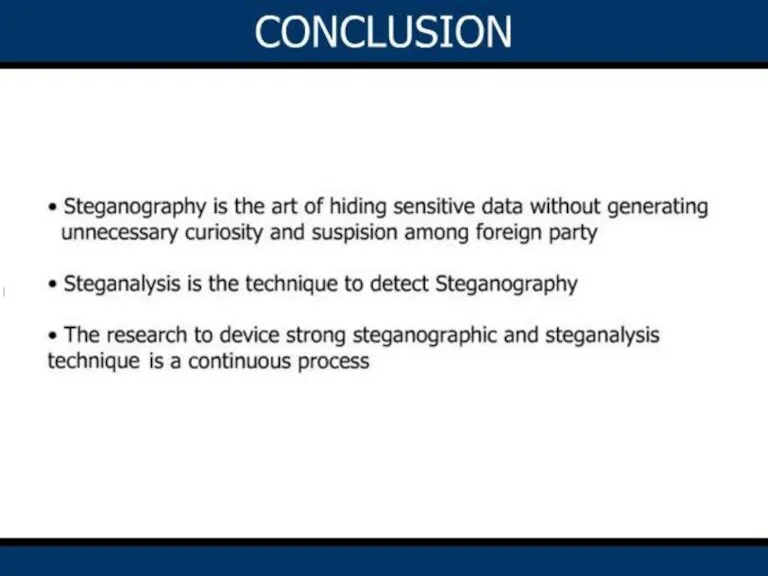
- 22. CONCLUSION
- 24. Скачать презентацию






 Внешняя политика России 2 -й половины
Внешняя политика России 2 -й половины 1-е послание ап. Павла к Коринфянам гл. 15, ст. 12-19 (Зач. 159)
1-е послание ап. Павла к Коринфянам гл. 15, ст. 12-19 (Зач. 159) Хуран кукли
Хуран кукли Сейсмика на Венере.(для справки)
Сейсмика на Венере.(для справки) Старославянизмы в современном русском языке
Старославянизмы в современном русском языке «Современный сайт, как способ коммуникации между органами государственной власти и населением: тенденции, технологии, требования
«Современный сайт, как способ коммуникации между органами государственной власти и населением: тенденции, технологии, требования Реализм XIX век
Реализм XIX век Lecture Туб бренд укор
Lecture Туб бренд укор Презентация на тему Описание предметов 2 класс
Презентация на тему Описание предметов 2 класс  Презентация на тему Солженицын - Жить не по лжи
Презентация на тему Солженицын - Жить не по лжи  Современные знаки различия, эмблемы и другие различительные знаки военнослужащих РФ
Современные знаки различия, эмблемы и другие различительные знаки военнослужащих РФ Презентация на тему Всестороннее развитие детей дошкольного возраста
Презентация на тему Всестороннее развитие детей дошкольного возраста Презентация по английскому Как написать свое имя и фамилию на английском языке
Презентация по английскому Как написать свое имя и фамилию на английском языке Ринок-“невидимка” – реклама в b2b пресі
Ринок-“невидимка” – реклама в b2b пресі Технологии обучения
Технологии обучения Государственная символика РФ
Государственная символика РФ Animal Quiz
Animal Quiz ПРОЕКТ 4а КЛАССА
ПРОЕКТ 4а КЛАССА Писатели и их картины к повести Гоголя Тарас Бульба
Писатели и их картины к повести Гоголя Тарас Бульба Отчетная выставка за первое полугодие по образовательной робототехнике Mindstorms
Отчетная выставка за первое полугодие по образовательной робототехнике Mindstorms Физическая культура как средство оздоровления населения
Физическая культура как средство оздоровления населения Психоэмоциональное здоровье
Психоэмоциональное здоровье День Русской Тельняшки. Игра Нас мало, но мы в тельняшках
День Русской Тельняшки. Игра Нас мало, но мы в тельняшках Формирование месторождений
Формирование месторождений  Техника запоминания иностранных слов
Техника запоминания иностранных слов Визаж. Макияж глаз
Визаж. Макияж глаз Методы автоматизации доказательства NP-полноты двумерных локально зависимых задач
Методы автоматизации доказательства NP-полноты двумерных локально зависимых задач Понятие проекта. Тема 8
Понятие проекта. Тема 8