Содержание
- 2. Introduction Symmetric encryption, also referred to as conventional encryption or single-key encryption, was the only type
- 3. Content Symmetric cipher Secure Use of Conventional Encryption 1. – – 2. 3. – – Symmetric
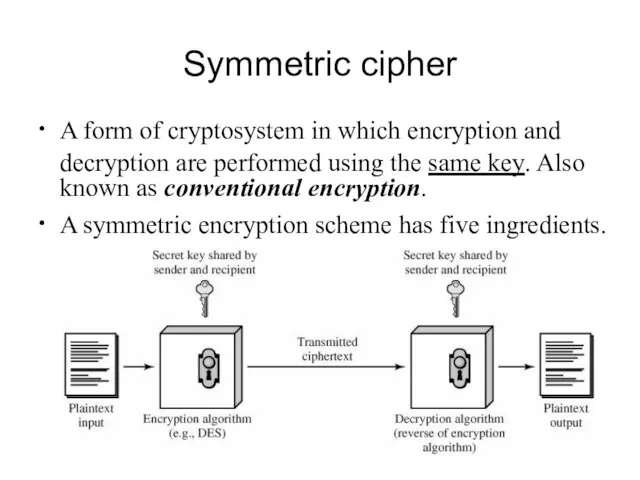
- 4. Symmetric cipher A form of cryptosystem in which encryption and decryption are performed using the same
- 5. Secure Use of Conventional Encryption Two requirements for secure use of conventional encryption: 1. Strong algorithm
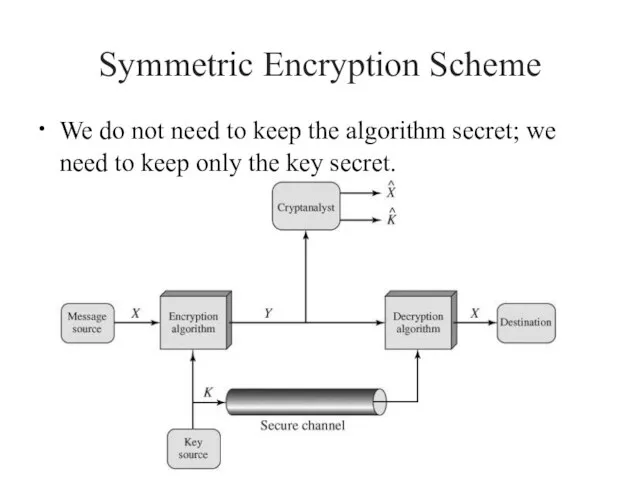
- 6. Symmetric Encryption Scheme We do not need to keep the algorithm secret; we need to keep
- 7. Cryptographic systems Characterized 1. The type plaintext to along three independent dimensions: of operations used for
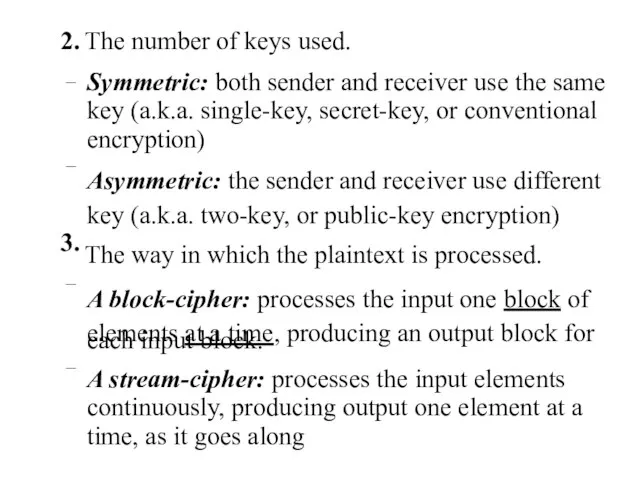
- 8. 2. – The number of keys used. Symmetric: both sender and receiver use the same key
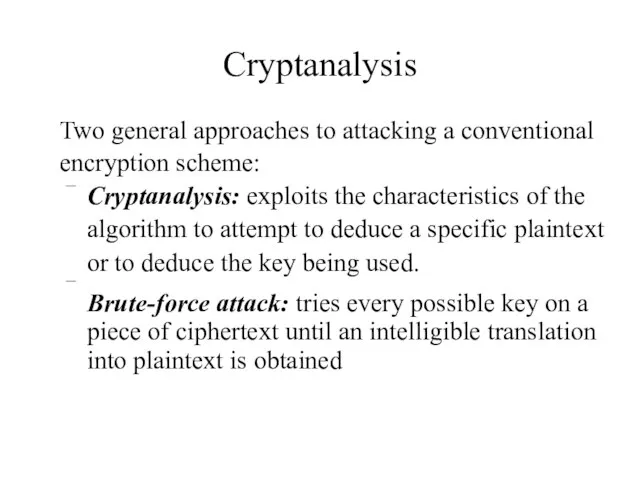
- 9. Cryptanalysis Two general approaches to attacking a conventional encryption scheme: Cryptanalysis: exploits the characteristics of the
- 10. Cryptanalytic Attacks Ciphertext only: ● Encryption algorithm Ciphertext – – Known plaintext: ● Encryption algorithm Ciphertext
- 11. Chosen plaintext: ● Encryption algorithm Ciphertext Plaintext message chosen by cryptanalyst, – – – together with
- 12. Chosen text: ● Encryption algorithm Ciphertext Plaintext message chosen by cryptanalyst, – – – together with
- 13. A Brute-Force Attack Trying every possible key until an intelligible ● translation of the ciphertext into
- 14. Brute-Force Cryptanalysis of Caesar Cipher Three important characteristics of this problem enabled us to use a
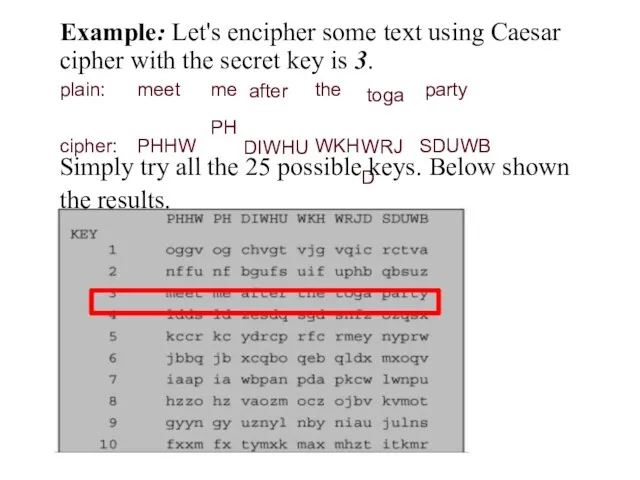
- 15. Example: Let's encipher some text using Caesar cipher with the secret key is 3. toga WRJD
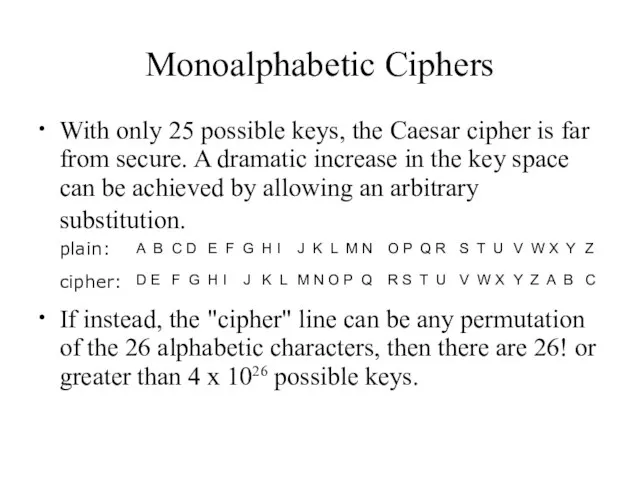
- 16. Monoalphabetic Ciphers With only 25 possible keys, the Caesar cipher is far ● from secure. A
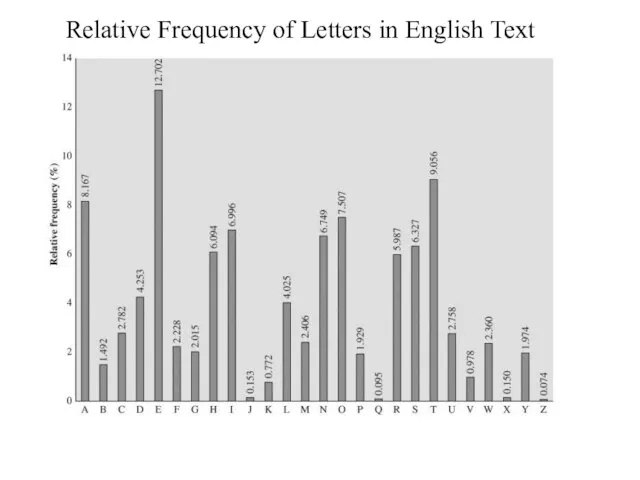
- 17. Breaking Monoalphabetic Cipher The ciphertext to be solved is UZQSOVUOHXMOPVGPOZPEVSGZWSZOPFPESXU DBMETSXAIZVUEPHZHMDZSHZOWSFPAPPDTSV PQUZWYMXUZUHSXEPYEPOPDZSZUFPOMBZWPF UPZHMDJUDTMOHMQ The relative frequency
- 18. Relative Frequency of Letters in English Text
- 19. Comparing two previously shown letters P and Z are the equivalents and t, but it is
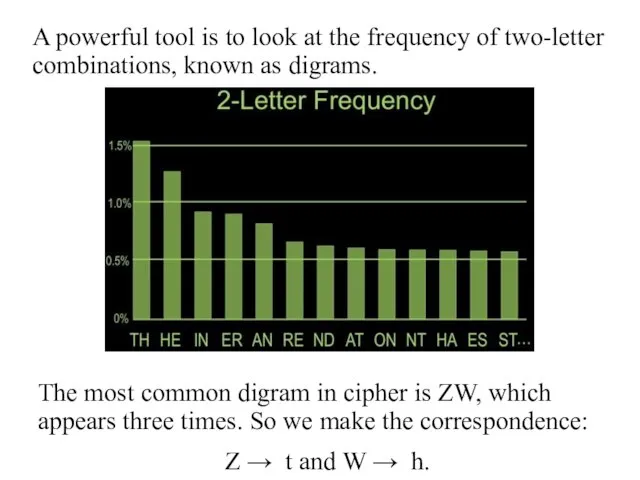
- 20. A powerful tool is to look at the frequency of two-letter combinations, known as digrams. The
- 21. So far, then, we have UZQSOVUOHXMOPVGPOZPEVSGZWSZOPFPESXUDBMETSXAIZ t a e e te a that e e a
- 22. Continued analysis of frequencies plus trial and error should easily yield a solution from this point.
- 24. Скачать презентацию











 Остеопороз
Остеопороз Меркантилизм как экономическая политика
Меркантилизм как экономическая политика Июльская ночь
Июльская ночь Общественная зарядка. Маркетинг
Общественная зарядка. Маркетинг нефть
нефть положения
положения занятие 5 ( кит )
занятие 5 ( кит ) Здоровые зубы, счастливый человек. Зубная паста для здоровья и блеска зубов Orecare
Здоровые зубы, счастливый человек. Зубная паста для здоровья и блеска зубов Orecare Анкеты РТК
Анкеты РТК ПРАВОВАЯ ГРАМОТНОСТЬ РОДИТЕЛЕЙ- ЗАЛОГ УСПЕШНОЙ СОЦИАЛЬНОЙ АДАПТАЦИИ ДЕТЕЙ.
ПРАВОВАЯ ГРАМОТНОСТЬ РОДИТЕЛЕЙ- ЗАЛОГ УСПЕШНОЙ СОЦИАЛЬНОЙ АДАПТАЦИИ ДЕТЕЙ. Презентация на тему Арифметические диктанты 3 класс
Презентация на тему Арифметические диктанты 3 класс  Презентация на тему год истории России
Презентация на тему год истории России  Информация. Кодирование информации
Информация. Кодирование информации Первое собрание для родителей будущих первоклассников
Первое собрание для родителей будущих первоклассников Справочно-информационные услуги – достижения, проблемы
Справочно-информационные услуги – достижения, проблемы Битва за серебряный столб (игра)
Битва за серебряный столб (игра) Судебная система РФ
Судебная система РФ Театральное искусство в VII веке
Театральное искусство в VII веке Презентация на тему Изобразительно – выразительная роль причастий
Презентация на тему Изобразительно – выразительная роль причастий  Введение в языкознание
Введение в языкознание Презентация на тему ВИДЫ ВСТУПЛЕНИЙ И ЗАКЛЮЧЕНИЙ К СОЧИНЕНИЮ ПО РУССКОМУ ЯЗЫКУ
Презентация на тему ВИДЫ ВСТУПЛЕНИЙ И ЗАКЛЮЧЕНИЙ К СОЧИНЕНИЮ ПО РУССКОМУ ЯЗЫКУ Современные обычные средства поражения
Современные обычные средства поражения Свадебный танец
Свадебный танец Материальное стимулирование труда
Материальное стимулирование труда ПРЕДСТАВЛЕНИЕ ЗВУКА В ПАМЯТИ КОМПЬЮТЕРА. ТЕХНИЧЕСКИЕ СРЕДСТВА МУЛЬТИМЕДИА.
ПРЕДСТАВЛЕНИЕ ЗВУКА В ПАМЯТИ КОМПЬЮТЕРА. ТЕХНИЧЕСКИЕ СРЕДСТВА МУЛЬТИМЕДИА. Латинский алфавит
Латинский алфавит Дано: ?ABC – равнобедренный BC – основание Доказа
Дано: ?ABC – равнобедренный BC – основание Доказа Сигурност и защита при работа в локална
Сигурност и защита при работа в локална