Содержание
- 2. Full information http://www.stanford.edu/class/cs101/network-1-introduction.html http://www.stanford.edu/class/cs101/network-2-internet.html
- 3. Outline How to send data? Dividing into packets Protocols (HTTP, FTP, SMTP) Error correction Types of
- 4. Basics of network The computer network is like a phone system When a user enters sdu.edu.kz
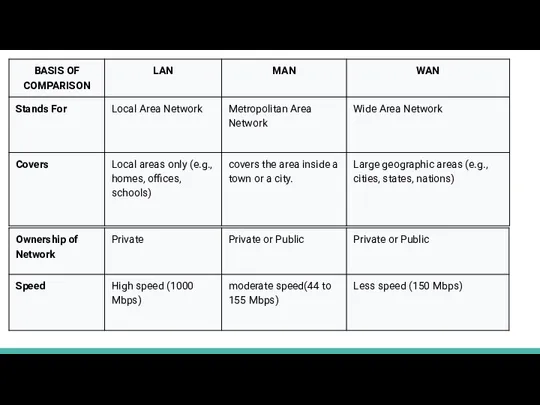
- 5. LAN, WAN, MAN A LAN (local area network) is a group of computers and network devices
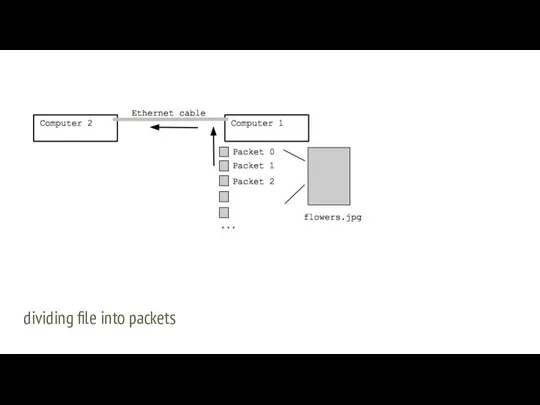
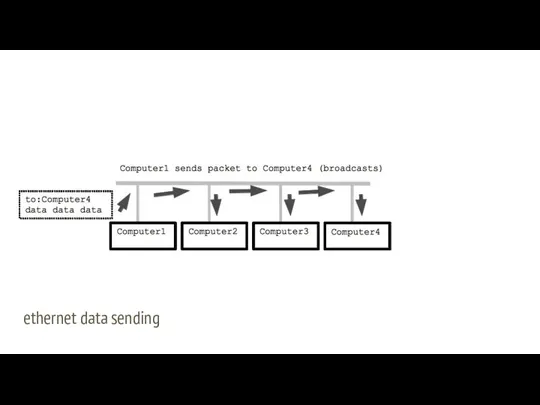
- 7. Packets data from here to there Problem: Send image from one computer to another on ethernet
- 8. dividing file into packets
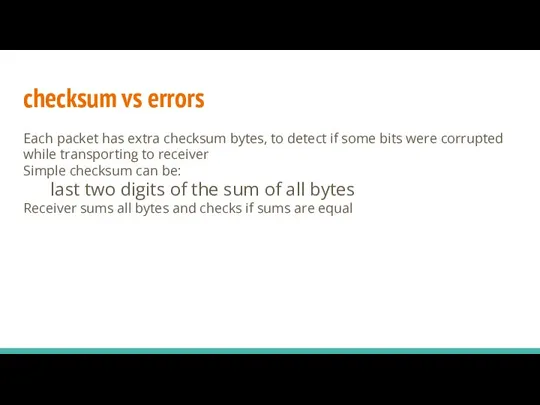
- 9. Problem: While sending packets through errors may occur Solution: We must check if received packet is
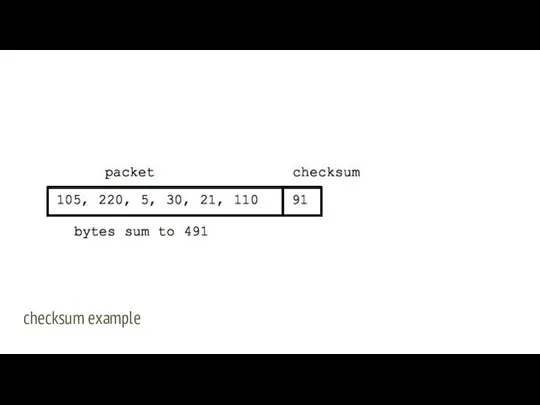
- 10. Each packet has extra checksum bytes, to detect if some bits were corrupted while transporting to
- 11. checksum example
- 12. Ethernet is the type of computer network: One wire shared by all the computers No central
- 13. ethernet data sending
- 14. MAC (Media Access Control) MAC address is burned at the factory Every computer (phone, desktop, laptop)
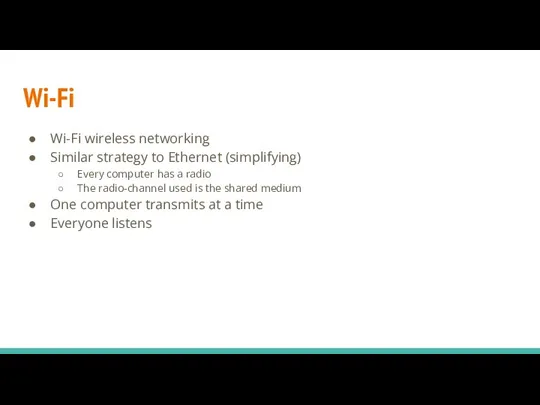
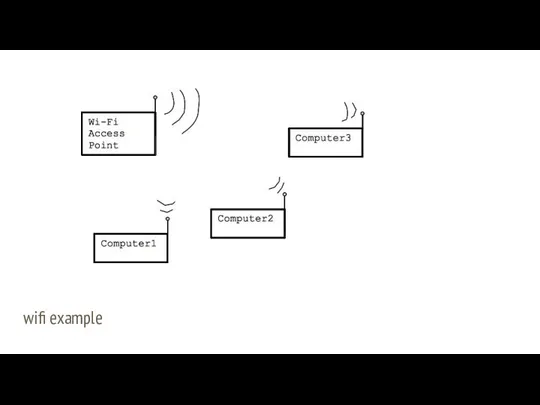
- 15. Wi-Fi wireless networking Similar strategy to Ethernet (simplifying) Every computer has a radio The radio-channel used
- 16. wifi example
- 17. ‘Protocol’ is a fancy word for simply saying “an agreed way to do something”. You might
- 18. HTTP The HyperText Transfer Protocol (HTTP) is the most common protocol in use on the internet.
- 19. Previously .. LAN, e.g. ethernet, Wi-Fi, one house Internet - world-wide network built on open standards
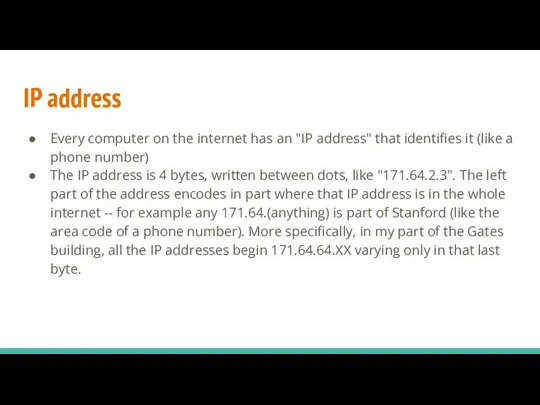
- 20. IP address Every computer on the internet has an "IP address" that identifies it (like a
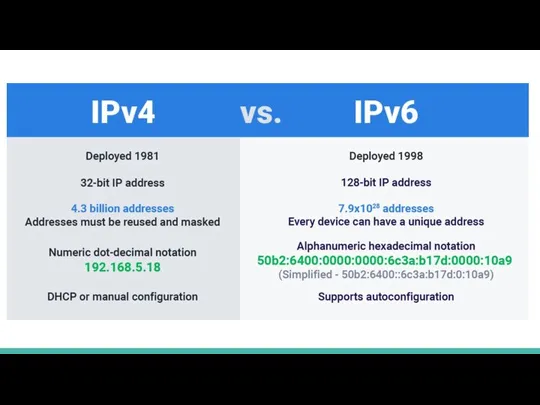
- 21. IPv4 vs IPv6 IPv4 can contain 2^8^4 = 2^32 = about 4.3 billion addresses IPv6 can
- 23. Internet of Things The Internet of Things (IoT) is the network of physical objects or "things"
- 24. What is web-site Web-site is some resource located on web-server Web-server is computer: always turned on
- 25. Domain names Basically human-readable synonyms for IP addresses codingbat.com (synonym for 173.255.219.70) Domain names are easy
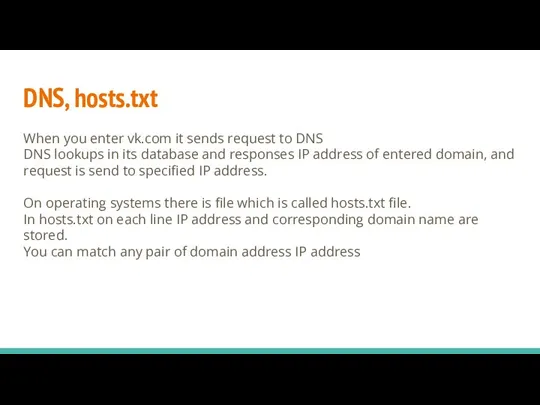
- 26. DNS, hosts.txt When you enter vk.com it sends request to DNS DNS lookups in its database
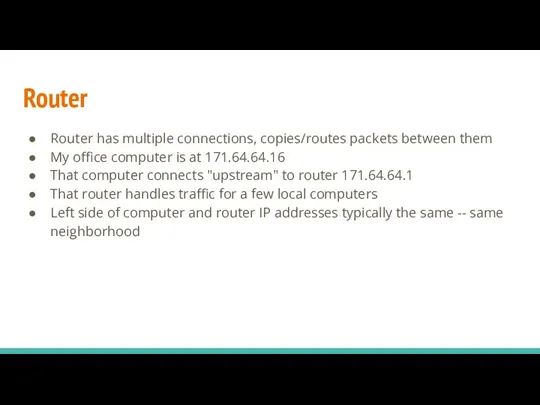
- 27. Router Router has multiple connections, copies/routes packets between them My office computer is at 171.64.64.16 That
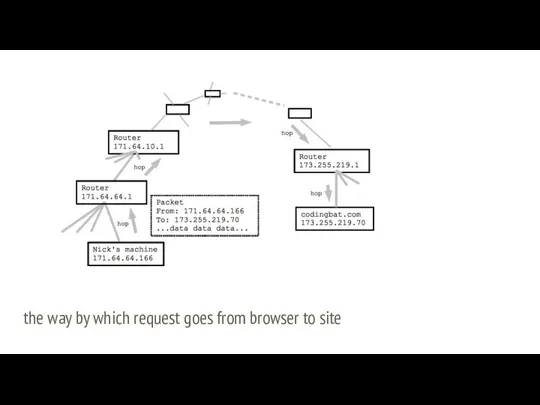
- 28. the way by which request goes from browser to site
- 29. Note that 10.x.x.x , 172.16.x.x and 192.168.x.x addresses are special "local" IP addresses These addresses are
- 30. Ping and traceroute Ping is command to check computer on some address is working Traceroute to
- 31. Switch A switch connects multiple computers together in a LAN. After the first data transfer, it
- 32. Hub A hub connects multiple computers together in a Local Area Network (LAN). All information sent
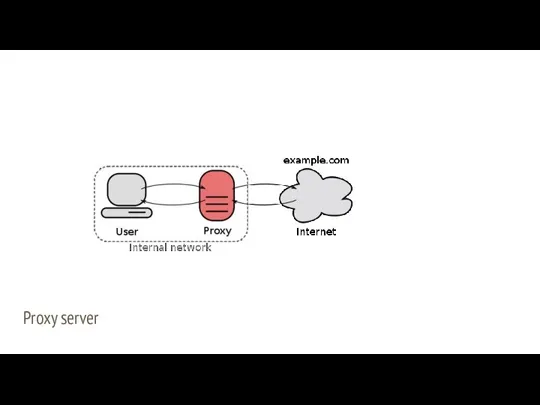
- 33. Proxy server Server software which is located between server and client. So that all requests from
- 34. Proxy server
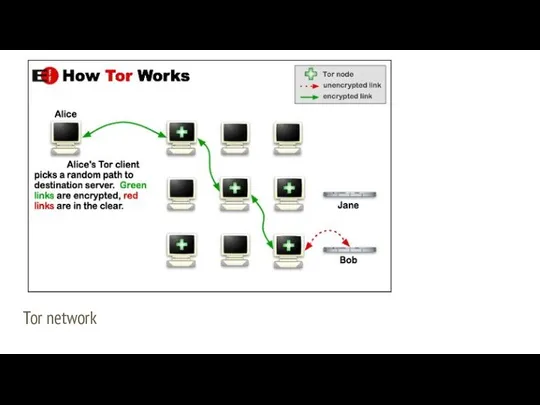
- 35. TOR - The Onion Router Tor is a network that keeps users anonymous on the Internet.
- 36. Tor network
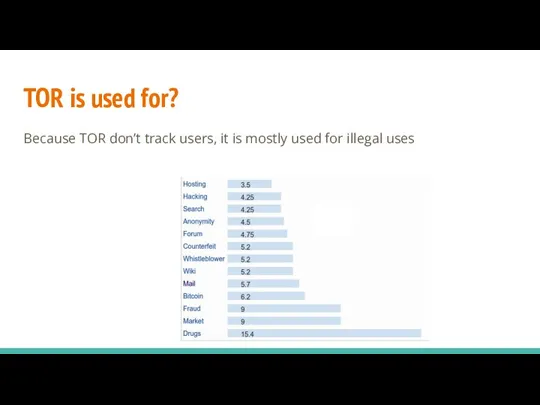
- 37. TOR is used for? Because TOR don’t track users, it is mostly used for illegal uses
- 38. Darknet Darknet is located inside TOR network TOR network recognizes .onion domain requests and sends it
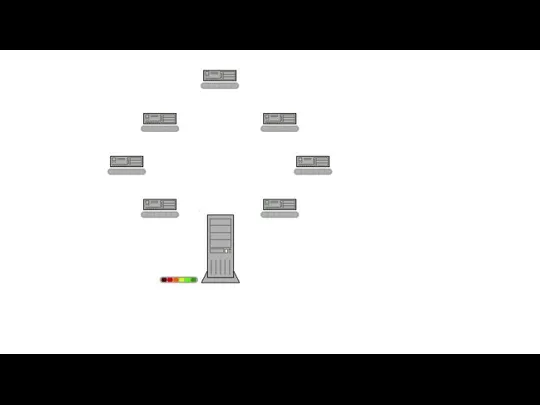
- 39. Server-client network On a client-server network, resources are located on and controlled by a central computer
- 40. P2P network In contrast to server-client network, P2P doesn’t have server. All computers in P2P network
- 41. BitTorrent BitTorrent protocol for peer-to-peer file sharing. File is located not in one server, but on
- 43. Because in server-client network there is only one server, and many clients. Server has limited bandwidth,
- 44. Firechat Mobile application that creates network from nearby devices, sends messages without using Internet, and cellular
- 45. Skype Skype (Sky peer to peer) was originally hybrid of client-server and peer-to-peer technology. Now it
- 47. Скачать презентацию


















 Информационные системы и технологии. Часть 2. Лекция 10. MES-системы
Информационные системы и технологии. Часть 2. Лекция 10. MES-системы Языки программирования и структуры данных. Лекция 8
Языки программирования и структуры данных. Лекция 8 Одобрение Онлайн по объектам на ДомКлик
Одобрение Онлайн по объектам на ДомКлик Ключевые слова. Файлы и файловые структуры
Ключевые слова. Файлы и файловые структуры Операции с целыми числами. 10 класс
Операции с целыми числами. 10 класс СКС Nikomax. Как работать с новым продуктом в портфеле
СКС Nikomax. Как работать с новым продуктом в портфеле Применение технологии формирующего оценивания Цепочка заметок на уроке информатики
Применение технологии формирующего оценивания Цепочка заметок на уроке информатики Единицы измерения информации
Единицы измерения информации лекция 21
лекция 21 Урок информатики в 7 классе
Урок информатики в 7 классе РКИС_лк1-2!!!!!!!
РКИС_лк1-2!!!!!!! vis02
vis02 Разработка информационной системы для решения задачи анализа финансовых потоков многоуровневой организации
Разработка информационной системы для решения задачи анализа финансовых потоков многоуровневой организации Организация вычислений в электронных таблицах
Организация вычислений в электронных таблицах ТЗ на приложение для сбора анкет
ТЗ на приложение для сбора анкет Основные доработки 2018 г. Развитие системы IVR (ITGC 51110 / 51111)
Основные доработки 2018 г. Развитие системы IVR (ITGC 51110 / 51111) Технологии программирования. Объектно-ориентированные языки программирования. Основные конструкции языка программирования С++
Технологии программирования. Объектно-ориентированные языки программирования. Основные конструкции языка программирования С++ Устройства ввода информации
Устройства ввода информации Наследование
Наследование ФЭПО тестирование
ФЭПО тестирование Веб-страница. Домашнее задание
Веб-страница. Домашнее задание TOP 5 MS Excel FEATURES
TOP 5 MS Excel FEATURES Компьютерные вирусы
Компьютерные вирусы Информационная безопасность
Информационная безопасность Системы счисления. Математические основы информатики
Системы счисления. Математические основы информатики Киберспортивная Лига РГГУ
Киберспортивная Лига РГГУ Работа с электронными таблицами
Работа с электронными таблицами Алгоритмы и исполнители
Алгоритмы и исполнители