Содержание
- 2. Security Governance Concepts, Principles, and Policies Understand and align security function to goals, mission, and objectives
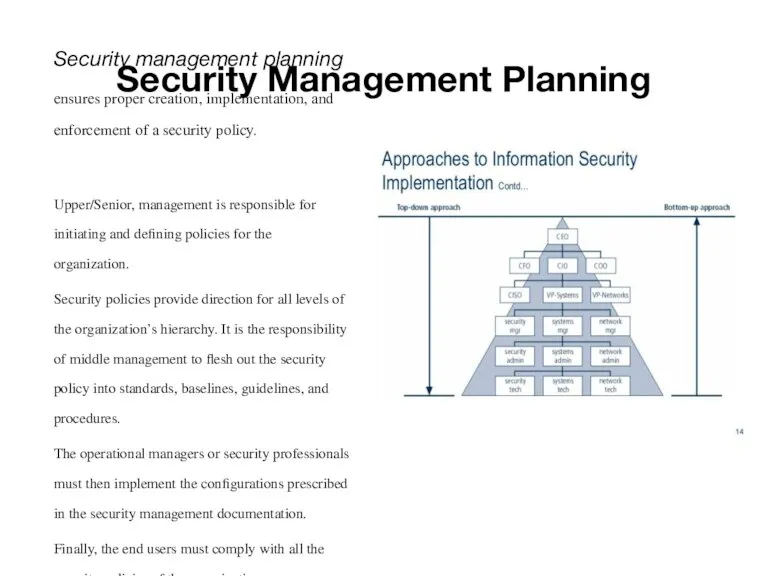
- 3. Security Management Planning Security management planning ensures proper creation, implementation, and enforcement of a security policy.
- 4. Security Management Planning defining security roles; prescribing how security will be managed, who will be responsible
- 5. “The best security plan is useless without one key factor: approval by senior management.”
- 6. A security management planning team should develop three types of plans: Strategic plan Long-term plan. It
- 7. Security Governance Security governance is the collection of practices related to supporting, defining, and directing the
- 8. Security Roles and Responsibilities Senior manager Security professional, Information Security officer, computer incident response team Data
- 9. Protection Mechanisms Layering, also known as defense in depth, is simply the use of multiple controls
- 10. Security Management Concepts and Principles SELF-READING CHAPTER 5
- 11. Develop and Implement Security Policy A security policy is a document that defines the scope of
- 12. Security Standards, Baselines, and Guidelines What are the four components of a complete organizational security policy
- 13. Policies are broad security statements. Standards are definitions of hardware and software security compliance. Standards are
- 15. Скачать презентацию










 СИСТЕМА РАБОТЫ ПО ГРАЖДАНСКОМУ ВОСПИТАНИЮ НА УРОКАХ РУССКОГО ЯЗЫКА, ЛИТЕРАТУРЫ И ВО ВНЕУРОЧНОЕ ВРЕМЯ
СИСТЕМА РАБОТЫ ПО ГРАЖДАНСКОМУ ВОСПИТАНИЮ НА УРОКАХ РУССКОГО ЯЗЫКА, ЛИТЕРАТУРЫ И ВО ВНЕУРОЧНОЕ ВРЕМЯ ПОЧЕМУ УМ, НЕ ВСЕГДА УСПЕХ.
ПОЧЕМУ УМ, НЕ ВСЕГДА УСПЕХ. учись учиться всему
учись учиться всему Олимпийские мгновения. XXII Олимпийские игры в Москве – 1980 год
Олимпийские мгновения. XXII Олимпийские игры в Москве – 1980 год The San Andreas Rift
The San Andreas Rift Презентация на тему СЛОЖЕНИЕ И ВЫЧИТАНИЕ ДВУЗНАЧНЫХ ЧИСЕЛ
Презентация на тему СЛОЖЕНИЕ И ВЫЧИТАНИЕ ДВУЗНАЧНЫХ ЧИСЕЛ  Презентация магистерской программы направление «Строительство» 270100.68.03«Современные методы расчета плоских и пространственных
Презентация магистерской программы направление «Строительство» 270100.68.03«Современные методы расчета плоских и пространственных  Морская беспилотная платформа FALCO military
Морская беспилотная платформа FALCO military Спортивный туризм Руководитель: Гусева Ю.В.
Спортивный туризм Руководитель: Гусева Ю.В. Вести из леса. Берёза
Вести из леса. Берёза Модернизация ПК
Модернизация ПК Решающая битва за независимость страны
Решающая битва за независимость страны Страноведение9 класс
Страноведение9 класс Центр образования цифрового и гуманитарного профилей Точка роста МАОУ СОШ № 7 г. Южноуральск
Центр образования цифрового и гуманитарного профилей Точка роста МАОУ СОШ № 7 г. Южноуральск Приморье в годы русско-японской войны
Приморье в годы русско-японской войны Шрифт чертежный ГОСТ 2.304-81
Шрифт чертежный ГОСТ 2.304-81 Международный стандарт с озвучкой
Международный стандарт с озвучкой Мы выбираем жизнь!!! жизнь без наркотиков!
Мы выбираем жизнь!!! жизнь без наркотиков! Проект Здоровый образ жизни
Проект Здоровый образ жизни Русские национальные виды спорта и игры
Русские национальные виды спорта и игры Обзор законодательства и государственных программ в сфере профилактики абортов и повышения рождаемости
Обзор законодательства и государственных программ в сфере профилактики абортов и повышения рождаемости Проектирование бизнеса. Формы организации бизнеса и организационная структура
Проектирование бизнеса. Формы организации бизнеса и организационная структура Инвестиционная деятельность и жилищное строительство
Инвестиционная деятельность и жилищное строительство Правила баскетбола
Правила баскетбола Что такое светская этика
Что такое светская этика СООТНОШЕНИЕ ФИГУРЫ И ФОНА
СООТНОШЕНИЕ ФИГУРЫ И ФОНА «Высшая математика» в контекстной рекламе
«Высшая математика» в контекстной рекламе Медицинское обследование математического здоровья Внеклассное мероприятие для учащихся 5-8 классов
Медицинское обследование математического здоровья Внеклассное мероприятие для учащихся 5-8 классов