Содержание
- 3. After completing this learning unit, you will have an understanding of: The impact security has, the
- 4. Lesson 1: Security, attacks and threats Introduction Lesson 2: Securing the environment Basics Help protect credentials
- 5. Security Threat Landscape Lesson 1: Security, attacks and threats Section: Introduction
- 6. Increasing incidents Multiple motivations Bigger risk Security is a Top Priority for IT
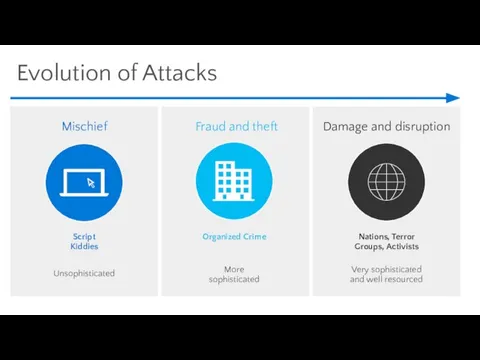
- 7. Evolution of Attacks
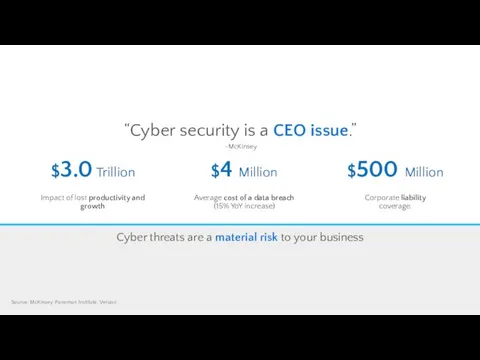
- 8. Source: McKinsey, Ponemon Institute, Verizon “Cyber security is a CEO issue.” -McKinsey
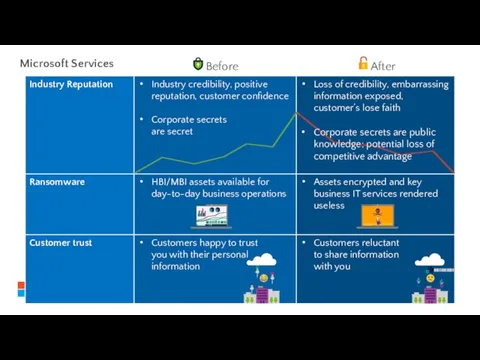
- 10. Corporate secrets are public knowledge; potential loss of competitive advantage
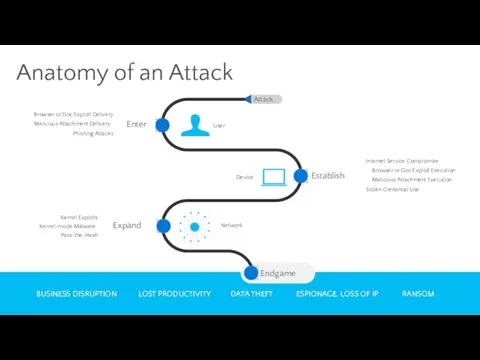
- 11. Different Attack Vectors
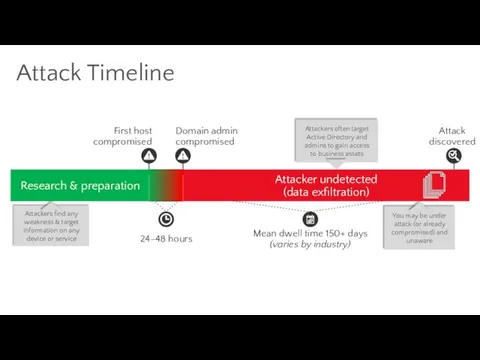
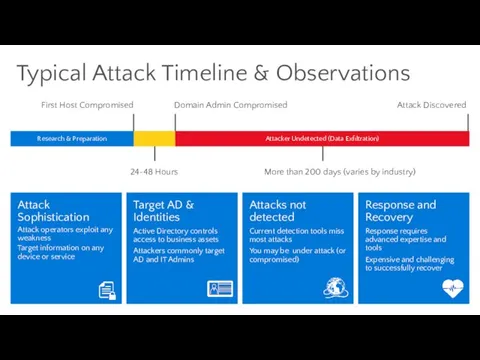
- 12. Attack Timeline 24–48 hours Mean dwell time 150+ days (varies by industry) First host compromised Domain
- 13. Malicious Attachment Execution Browser or Doc Exploit Execution Stolen Credential Use Internet Service Compromise Kernel-mode Malware
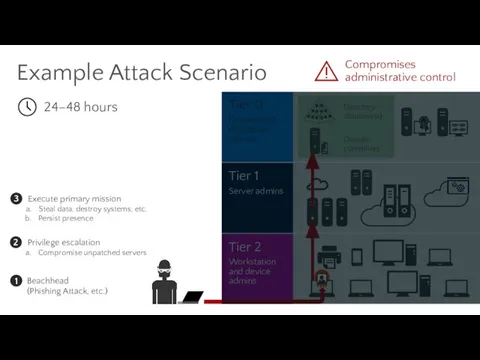
- 14. Example Attack Scenario Domain controllers Directory database(s) Persist presence
- 15. Schoolboard 50 Employees 300 Students Public funds Construction 4,000 Employees $30 millions YR Private funds Energy
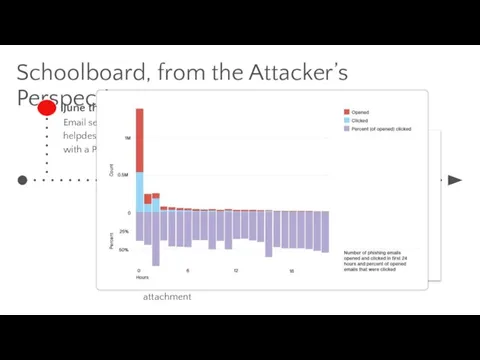
- 16. Schoolboard, from the Attacker’s Perspective June the 3rd Email sent to [email protected] with a PPTX attached
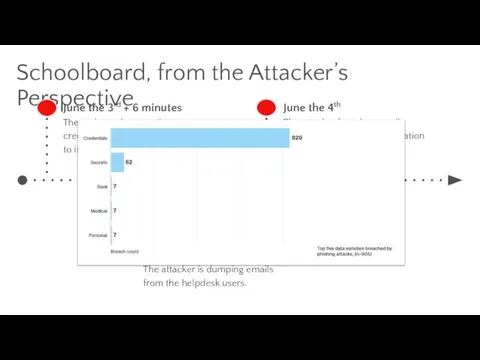
- 17. Schoolboard, from the Attacker’s Perspective June the 3rd + 6 minutes The malware is extracting credentials
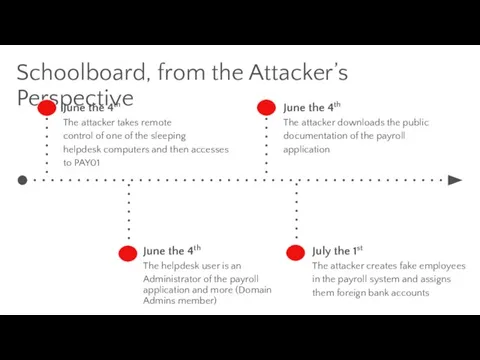
- 18. Schoolboard, from the Attacker’s Perspective June the 4th The attacker takes remote control of one of
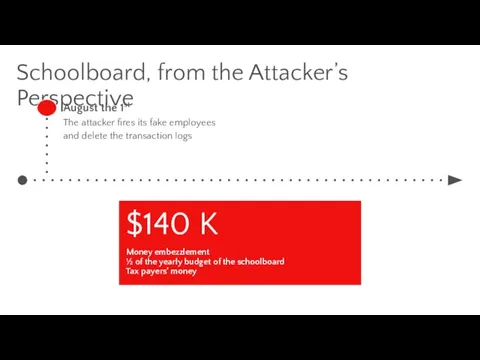
- 19. Schoolboard, from the Attacker’s Perspective August the 1st The attacker fires its fake employees and delete
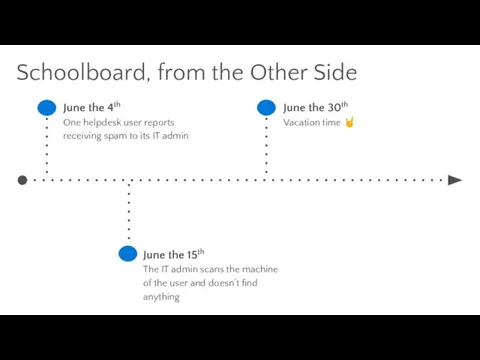
- 20. Schoolboard, from the Other Side June the 4th One helpdesk user reports receiving spam to its
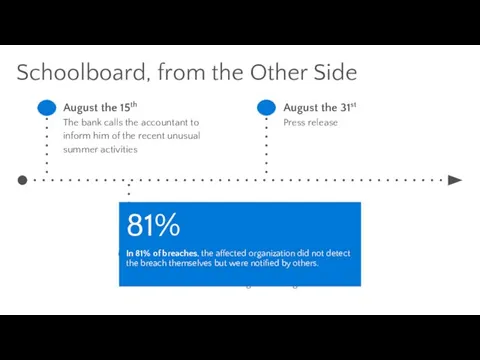
- 21. Schoolboard, from the Other Side August the 15th The bank calls the accountant to inform him
- 22. Spam/phishing detection Phishing awareness training Suspicious activities reporting process (Security Incident Management) No separation of privileged
- 23. Construction 4,000 Employees $30 millions YR Private funds
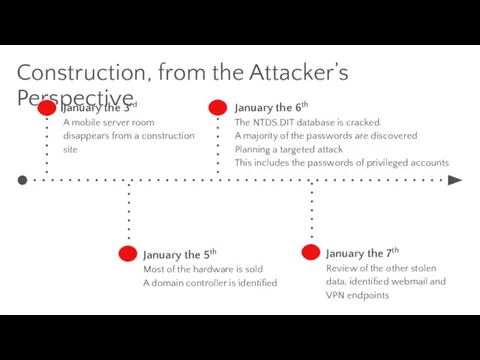
- 24. Construction, from the Attacker’s Perspective January the 3rd A mobile server room disappears from a construction
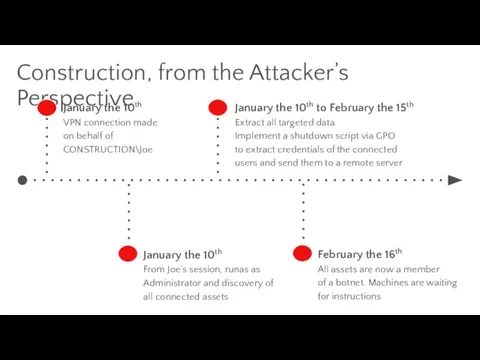
- 25. Construction, from the Attacker’s Perspective January the 10th VPN connection made on behalf of CONSTRUCTION\Joe January
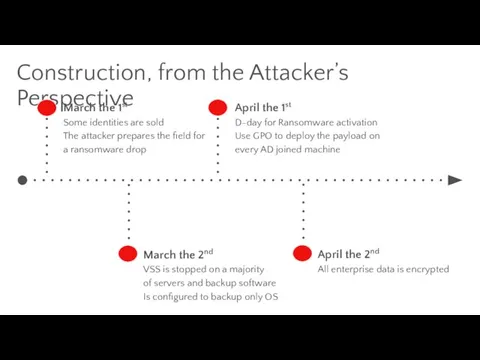
- 26. Construction, from the Attacker’s Perspective March the 1st Some identities are sold The attacker prepares the
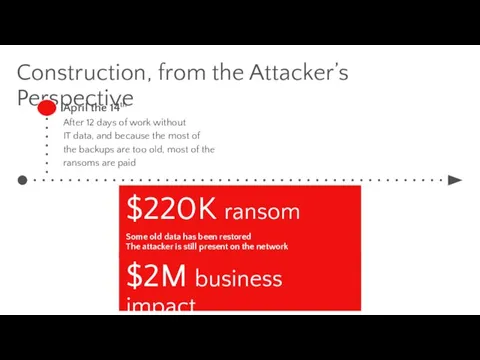
- 27. Construction, from the Attacker’s Perspective April the 14th After 12 days of work without IT data,
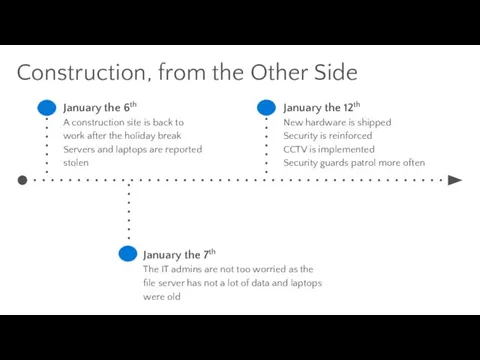
- 28. Construction, from the Other Side January the 6th A construction site is back to work after
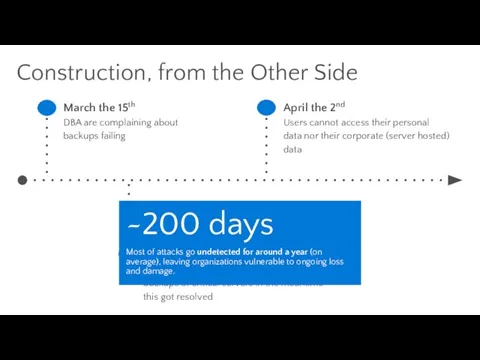
- 29. Construction, from the Other Side March the 15th DBA are complaining about backups failing March the
- 30. Physical protection Procedures in case of theft Inefficient monitoring What went wrong?
- 31. Energy 95,000 Employees $5 billions YR Private funds Shareholders Networks Corporate network Closed network in production
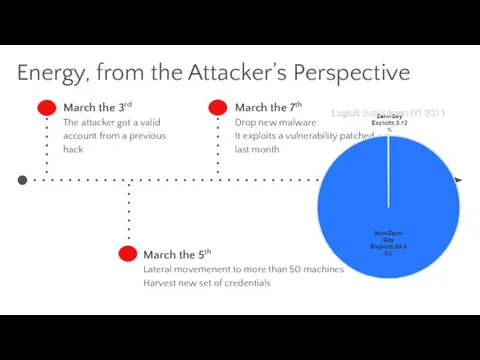
- 32. Energy, from the Attacker’s Perspective March the 3rd The attacker got a valid account from a
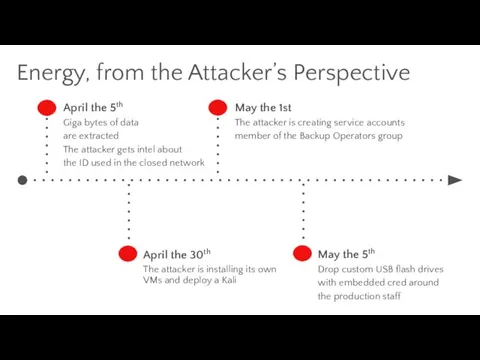
- 33. Energy, from the Attacker’s Perspective April the 5th Giga bytes of data are extracted The attacker
- 34. Energy, from the Attacker’s Perspective May the 7th The production is down in one critical site
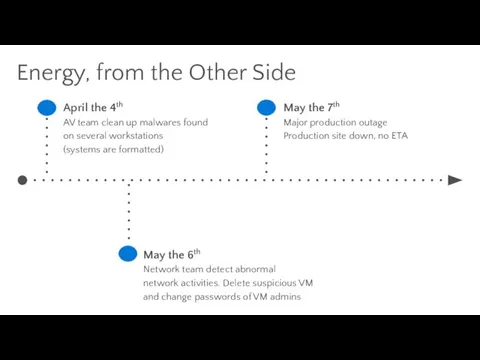
- 35. Energy, from the Other Side April the 4th AV team clean up malwares found on several
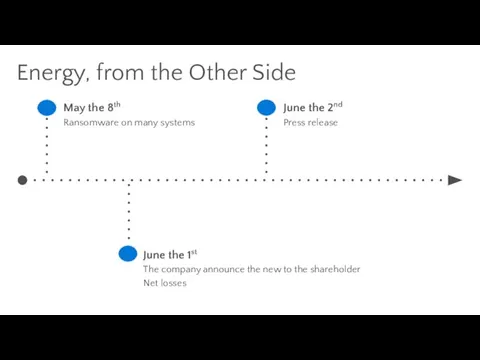
- 36. Energy, from the Other Side May the 8th Ransomware on many systems June the 1st The
- 37. More than 200 days (varies by industry) Typical Attack Timeline & Observations Attack Sophistication Attack operators
- 38. Cost of an attack The cost of these attacks to the global economy, and to an
- 39. Security Threat Landscape Lesson 2: Securing the environment Section: Basics
- 40. Hard Lessons…
- 41. Windows Server Security Posture
- 42. Secure the OS Managed privileged identities Secure virtualization What do we need to secure and how?
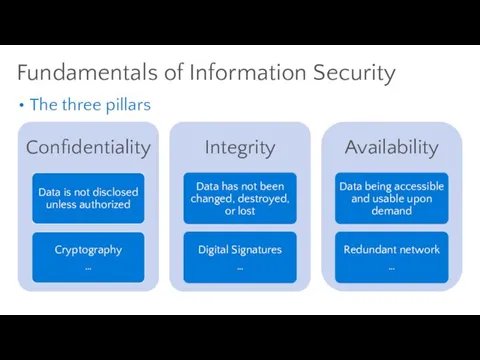
- 43. Fundamentals of Information Security
- 44. Information Security Concepts and Fundamental Principles Confidentiality Integrity Availability The CIA Triad
- 45. The three pillars Fundamentals of Information Security
- 46. References for Canada • Annex 1 - Departmental IT Security Risk Management Activities: IT Security Risk
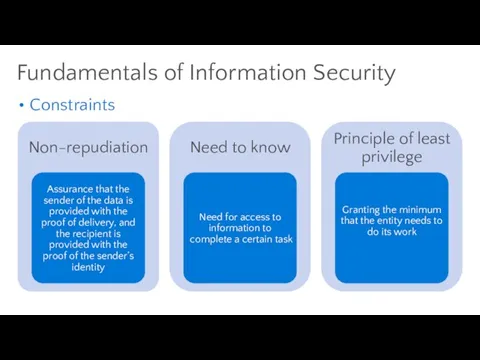
- 47. Constraints Fundamentals of Information Security
- 48. You want to make it… Harder Longer More noisy … for the attacker You want to
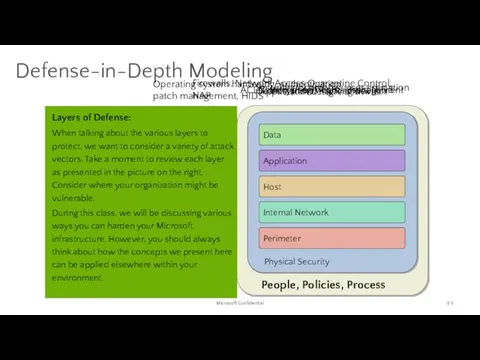
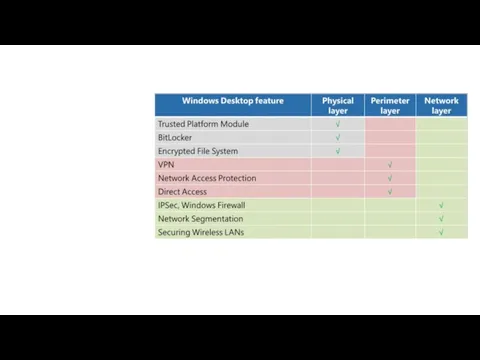
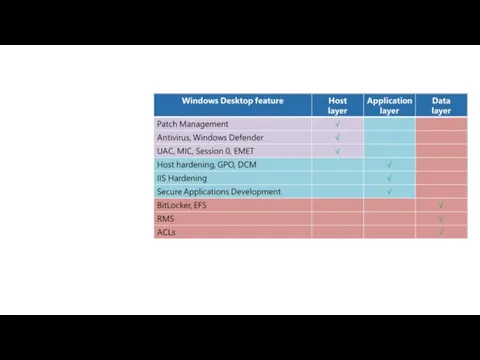
- 49. Defense-in-Depth Modeling Layers of Defense: When talking about the various layers to protect, we want to
- 52. Strategic shift Defense-in-Depth Modeling From perimeter security … … to assumed breach Protect information Establish security
- 53. Risk Management
- 54. What is a vulnerability? A flaw or weakness in a system’s design, implementation, or operation and
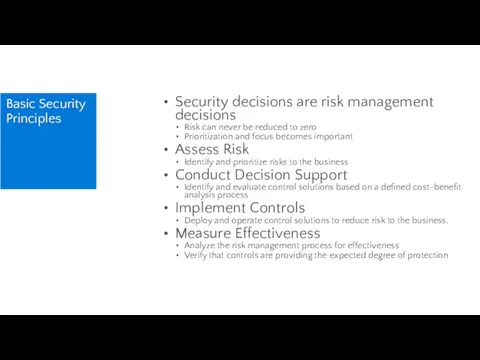
- 55. Basic Security Principles Security decisions are risk management decisions Risk can never be reduced to zero
- 56. Basic Security Principles: How We Protect It Principle of Least Privilege (POLP) Access varies based on
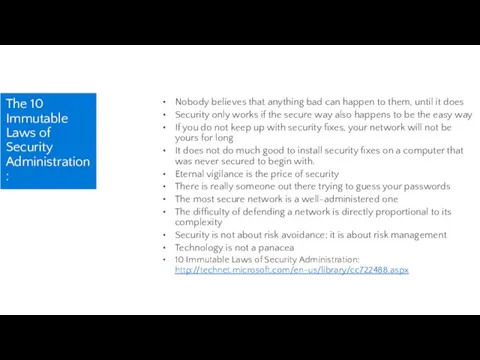
- 57. The 10 Immutable Laws of Security Administration: Nobody believes that anything bad can happen to them,
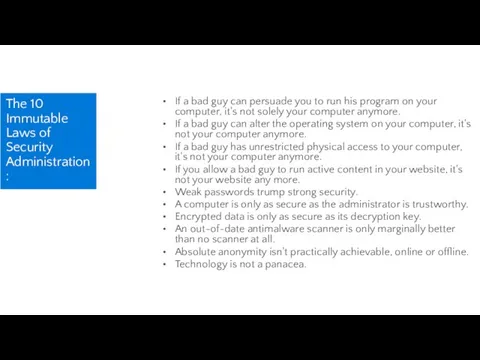
- 58. The 10 Immutable Laws of Security Administration: If a bad guy can persuade you to run
- 59. Sample AD assets Domain Controllers Active Directory Backups Administrative Accounts and Groups Identities and attributes Group
- 60. Vulnerabilities A flaw or weakness in a system’s design, implementation, or operation and management that could
- 61. Vulnerabilities (continued) Hardware Outdated firmware Systems not physically secured Misconfigured systems Software Out-of-date antivirus software Missing
- 62. Vulnerabilities (continued) Communications Unencrypted network protocols Connections to multiple networks No filtering between network segments Human
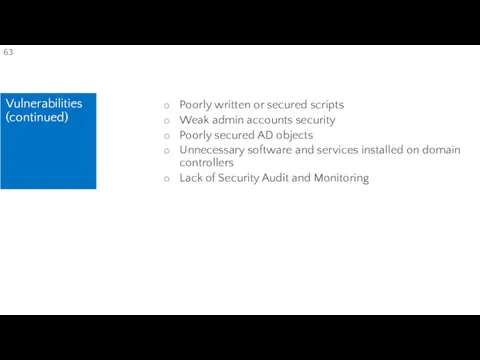
- 63. Vulnerabilities (continued) Poorly written or secured scripts Weak admin accounts security Poorly secured AD objects Unnecessary
- 64. Security Threat Landscape Lesson 2: Securing the environment Section: Help protect credentials and privileged access
- 65. Challenges in Protecting Credentials Ben Mary Jake Admin Domain admin Typical administrator Capability Time Social engineering
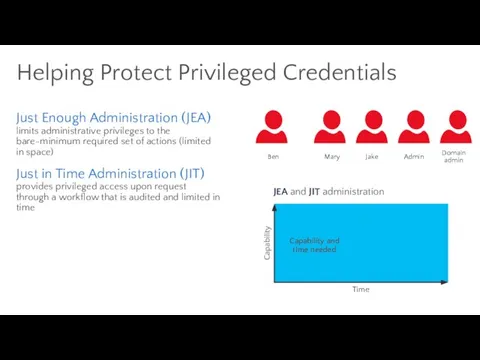
- 66. Helping Protect Privileged Credentials Ben Mary Jake Admin Domain admin JEA and JIT administration Capability Time
- 67. Helping Protect Privileged Credentials Ben Mary Jake Admin Domain admin JEA and JIT administration Capability Time
- 68. Helping Protect Privileged Credentials Ben Mary Jake Admin Domain admin JEA and JIT administration Capability Time
- 69. Security Threat Landscape Lesson 2: Securing the environment Section: Help protect applications and data in any
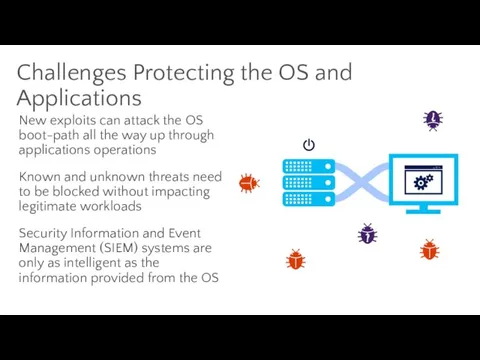
- 70. Challenges Protecting the OS and Applications New exploits can attack the OS boot-path all the way
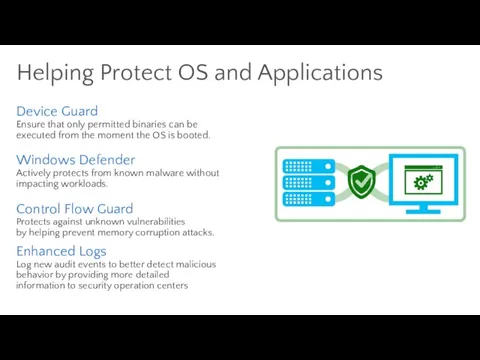
- 71. Helping Protect OS and Applications Device Guard Ensure that only permitted binaries can be executed from
- 72. Security Threat Landscape Lesson 2: Securing the environment Section: Help protect the virtualization fabric
- 73. Help Protect the Virtualization Fabric
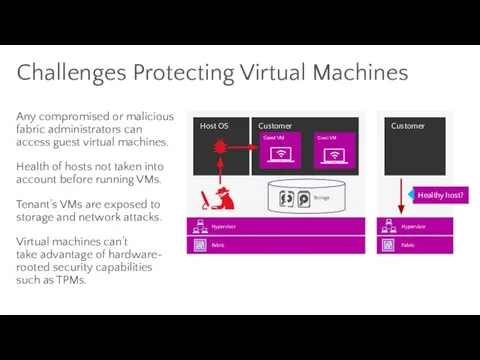
- 74. Challenges Protecting Virtual Machines Any compromised or malicious fabric administrators can access guest virtual machines. Health
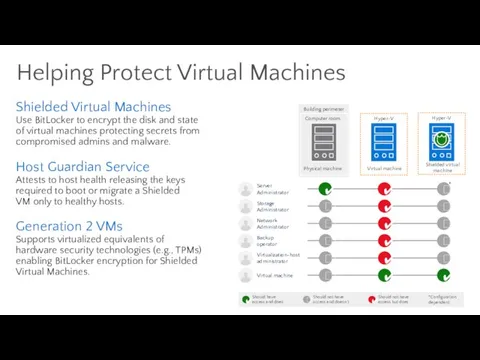
- 75. Helping Protect Virtual Machines Shielded Virtual Machines Use BitLocker to encrypt the disk and state of
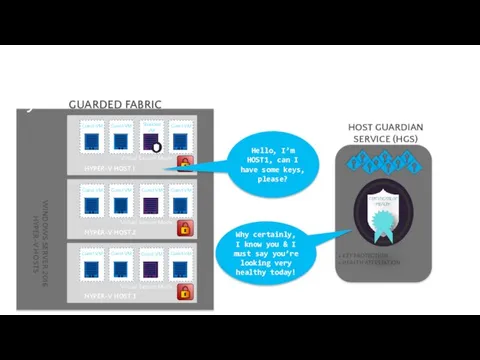
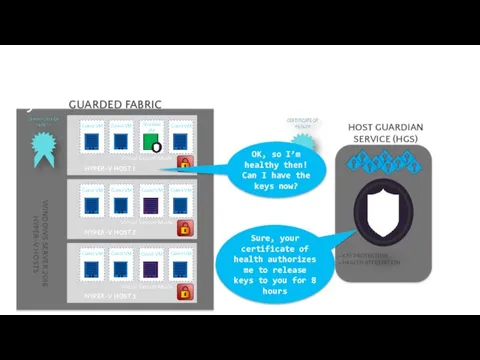
- 76. Decryption keys: controlled by external system HYPER-V HOST 1 + KEY PROTECTION + HEALTH ATTESTATION HOST
- 77. Decryption keys: controlled by external system HYPER-V HOST 1 + KEY PROTECTION + HEALTH ATTESTATION HOST
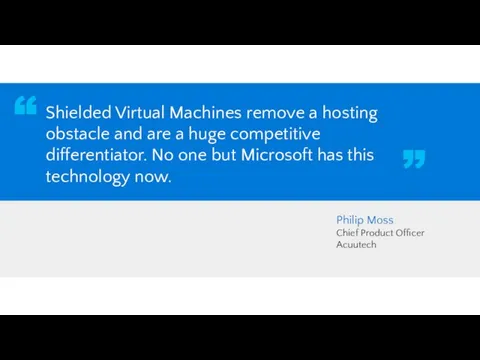
- 78. Philip Moss Chief Product Officer Acuutech Shielded Virtual Machines remove a hosting obstacle and are a
- 79. Security Threat Landscape Lesson 2: Securing the environment Section: Protect with just enough OS
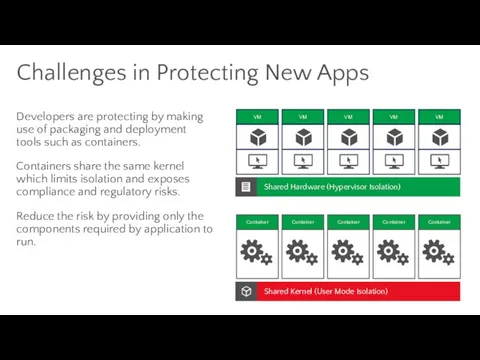
- 80. Challenges in Protecting New Apps Developers are protecting by making use of packaging and deployment tools
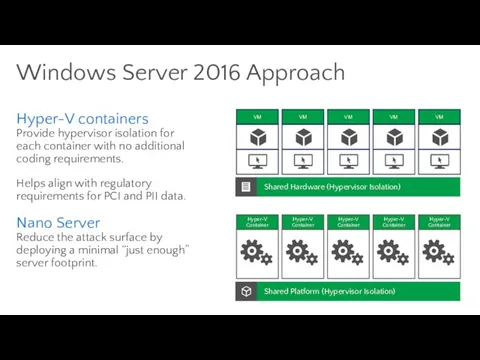
- 81. Windows Server 2016 Approach Hyper-V containers Provide hypervisor isolation for each container with no additional coding
- 82. Security Threat Landscape Lesson 2: Securing the environment Section: Windows Server 2016 security summary
- 83. Windows Server 2016 Security Summary
- 84. DO NOT REMOVE: this is a hidden slide for notes purposes
- 85. Question #1: What is the new security perimeter? Question #2: What are the four option we
- 87. Скачать презентацию
































 Неметаллы
Неметаллы Конструирование шкатулки из бросового материала
Конструирование шкатулки из бросового материала Кафедра ТИССУ
Кафедра ТИССУ Проект Зелёное кольцо
Проект Зелёное кольцо Урок литературного чтения в 1 классе
Урок литературного чтения в 1 классе Горные и маркшейдерские работы применительно к условиям разработки Лебединского месторождения
Горные и маркшейдерские работы применительно к условиям разработки Лебединского месторождения Химическая и нефтехимическая промышленность в России: роль государства в преодолении кризиса и дальнейшем развитии отрасли
Химическая и нефтехимическая промышленность в России: роль государства в преодолении кризиса и дальнейшем развитии отрасли Оптимизация процесса настройки рабочего места для работы в Единой информационной системе в сфере закупок
Оптимизация процесса настройки рабочего места для работы в Единой информационной системе в сфере закупок Презентация на тему Применение фотоэффекта
Презентация на тему Применение фотоэффекта ПРОГРАММЫ ПОДГОТОВКИ ЛЮБИТЕЛЬСКИХ КОМАНД
ПРОГРАММЫ ПОДГОТОВКИ ЛЮБИТЕЛЬСКИХ КОМАНД Роль отца в воспитании ребенка
Роль отца в воспитании ребенка Волевые качества
Волевые качества Урок-открытие
Урок-открытие Институциональные репозитории: создание и управление
Институциональные репозитории: создание и управление Паровые машины
Паровые машины Уимблдон
Уимблдон Современные модели образовательного процесса соответствии с ФГТ
Современные модели образовательного процесса соответствии с ФГТ Реклама в торговом комплексе «Фиолент»
Реклама в торговом комплексе «Фиолент» VXlkbvvDUSz19pGVCwhRfQ
VXlkbvvDUSz19pGVCwhRfQ Сайт для студии-ателье IRINA LAVINOVA
Сайт для студии-ателье IRINA LAVINOVA Kuv_2022_MS_13_Recons_авг (1)
Kuv_2022_MS_13_Recons_авг (1) Презентацию составила учитель математики БОУ СОШ26 п.Украинский Динского района Краснодарского края Краснощекова Л.Г.
Презентацию составила учитель математики БОУ СОШ26 п.Украинский Динского района Краснодарского края Краснощекова Л.Г. Живопись. Гармония по общему цветовому тону (тема 18)
Живопись. Гармония по общему цветовому тону (тема 18) www.ratsp.ru
www.ratsp.ru Последовательное соединение проводников
Последовательное соединение проводников Равнины и горы России
Равнины и горы России Фестиваль Бархатный сезон. Ялта
Фестиваль Бархатный сезон. Ялта Курс лекций по дисциплине Экология
Курс лекций по дисциплине Экология