Содержание
- 2. Virtualization: rejuvenation 1960’s: first track of virtualization Time and resource sharing on expensive mainframes IBM VM/370
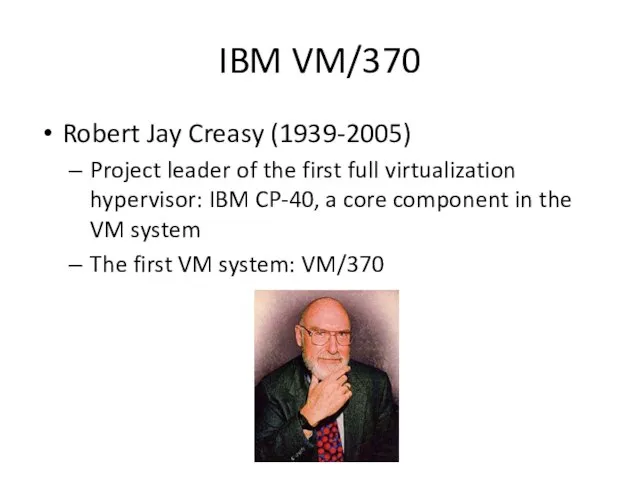
- 3. IBM VM/370 Robert Jay Creasy (1939-2005) Project leader of the first full virtualization hypervisor: IBM CP-40,
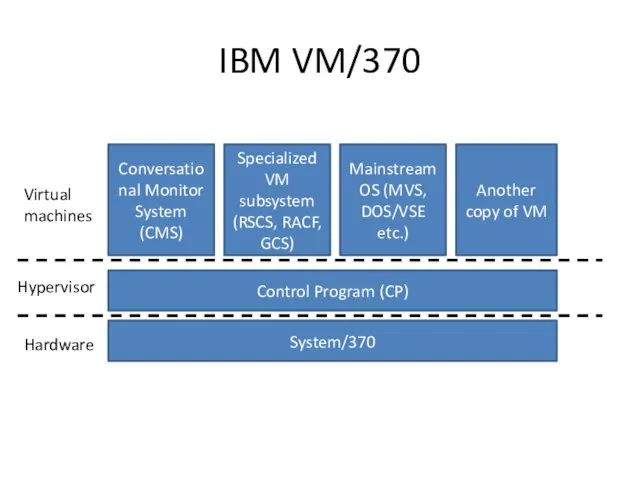
- 4. IBM VM/370 System/370 Control Program (CP) Conversational Monitor System (CMS) Mainstream OS (MVS, DOS/VSE etc.) Specialized
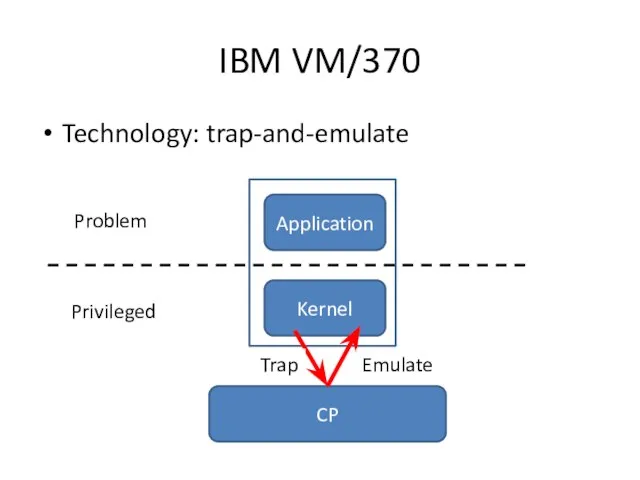
- 5. IBM VM/370 Technology: trap-and-emulate Kernel Application CP
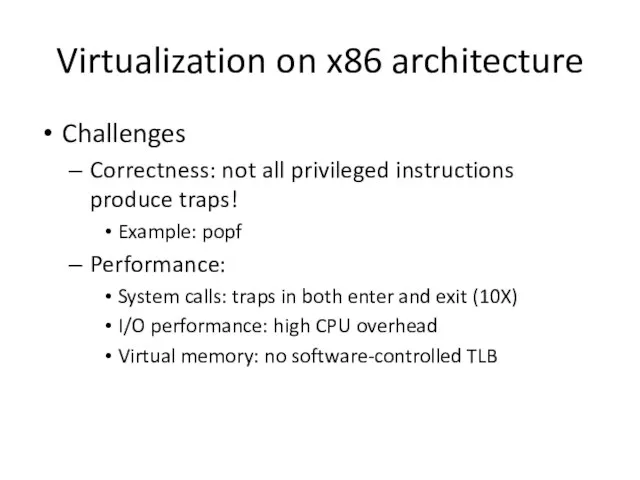
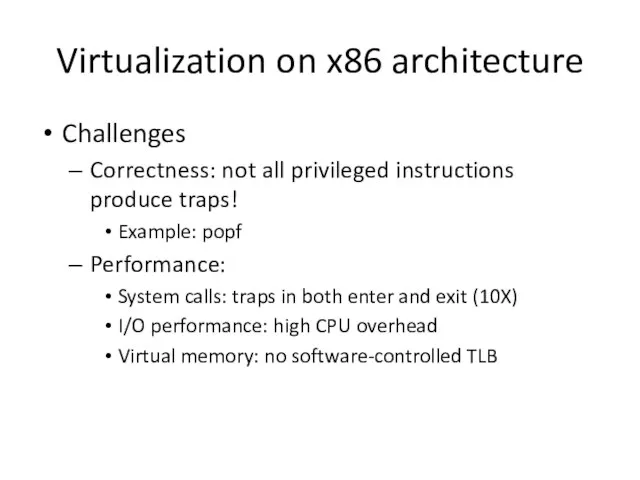
- 6. Virtualization on x86 architecture Challenges Correctness: not all privileged instructions produce traps! Example: popf Performance: System
- 7. Virtualization on x86 architecture Solutions: Dynamic binary translation & shadow page table Hardware extension Para-virtualization (Xen)
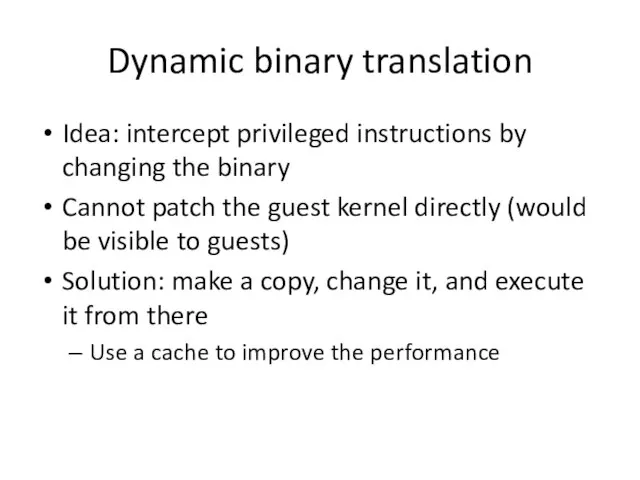
- 8. Dynamic binary translation Idea: intercept privileged instructions by changing the binary Cannot patch the guest kernel
- 9. Dynamic binary translation Pros: Make x86 virtualizable Can reduce traps Cons: Overhead Hard to improve system
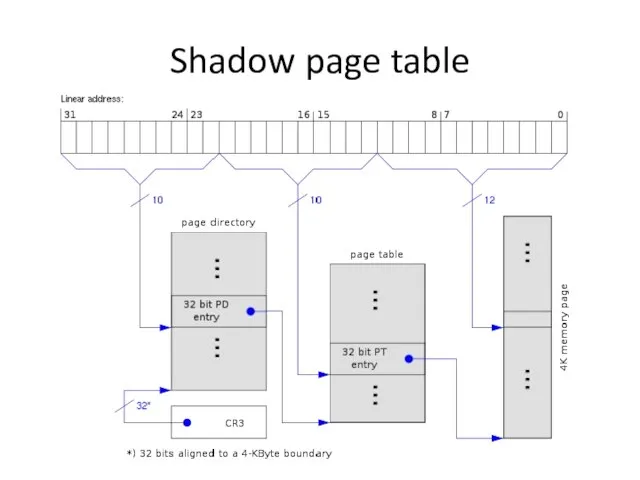
- 10. Shadow page table
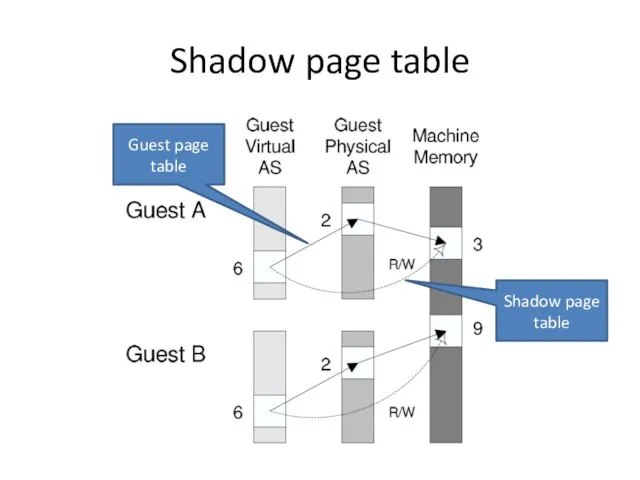
- 11. Shadow page table Guest page table Shadow page table
- 12. Shadow page table Pros: Transparent to guest VMs Good performance when working set fit into shadow
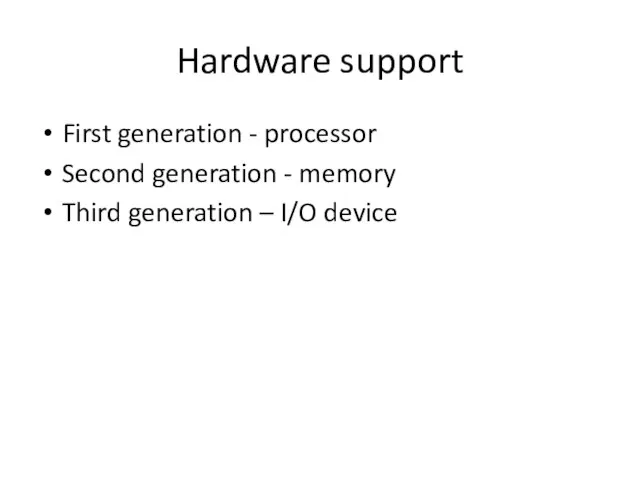
- 13. Hardware support First generation - processor Second generation - memory Third generation – I/O device
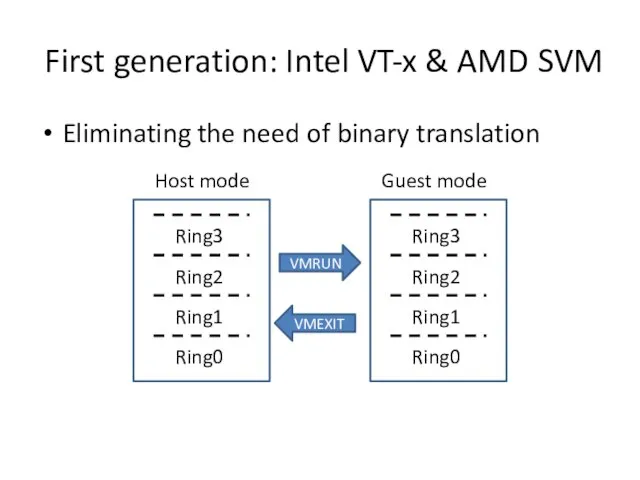
- 14. First generation: Intel VT-x & AMD SVM Eliminating the need of binary translation Host mode Guest
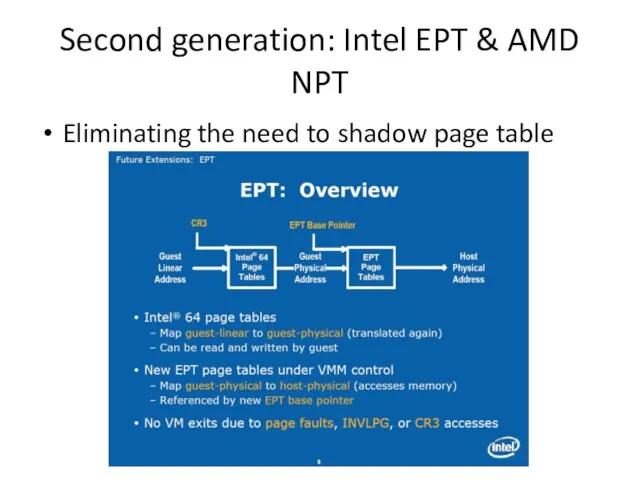
- 15. Second generation: Intel EPT & AMD NPT Eliminating the need to shadow page table
- 16. Third generation: Intel VT-d & AMD IOMMU I/O device assignment VM owns real device DMA remapping
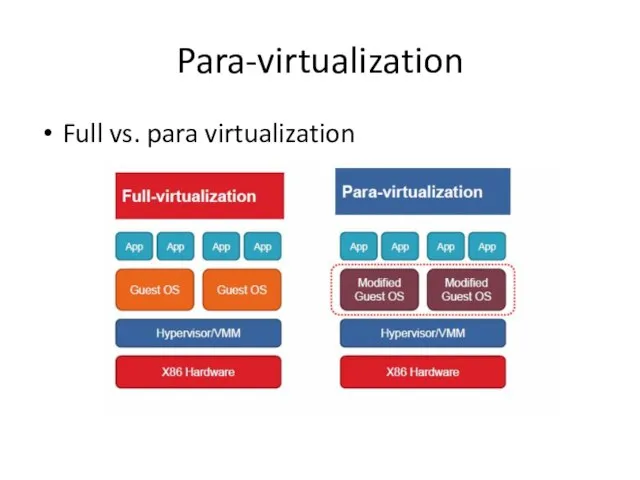
- 17. Para-virtualization Full vs. para virtualization
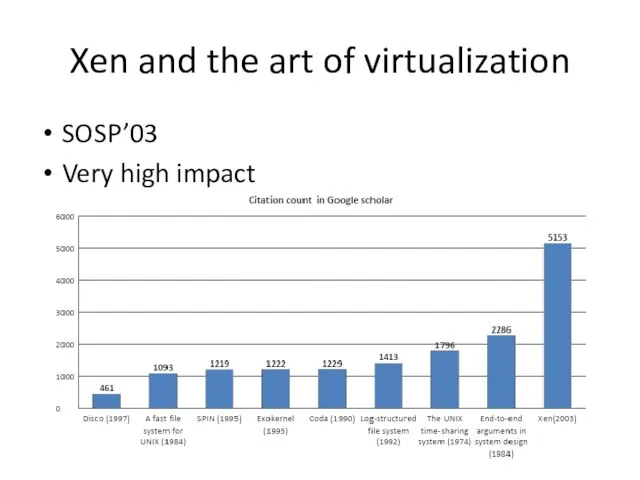
- 18. Xen and the art of virtualization SOSP’03 Very high impact
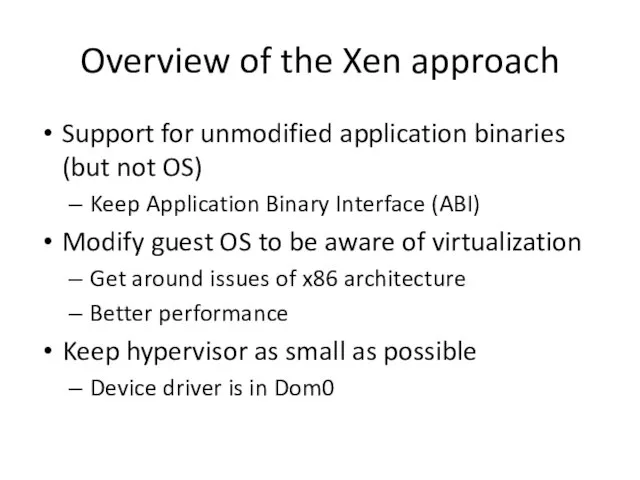
- 19. Overview of the Xen approach Support for unmodified application binaries (but not OS) Keep Application Binary
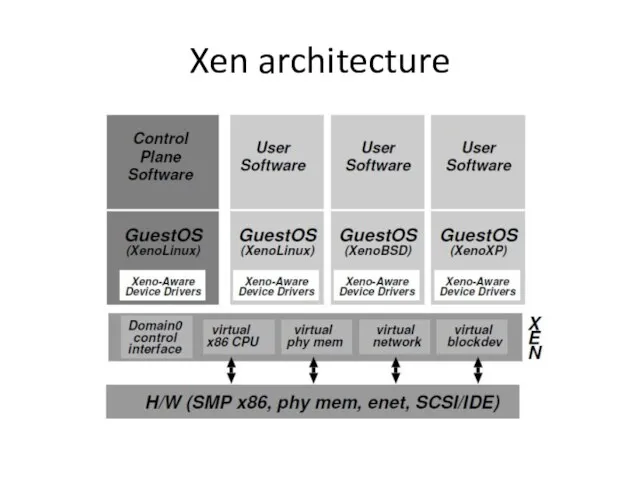
- 20. Xen architecture
- 21. Virtualization on x86 architecture Challenges Correctness: not all privileged instructions produce traps! Example: popf Performance: System
- 22. CPU virtualization Protection Xen in ring0, guest kernel in ring1 Privileged instructions are replaced with hypercalls
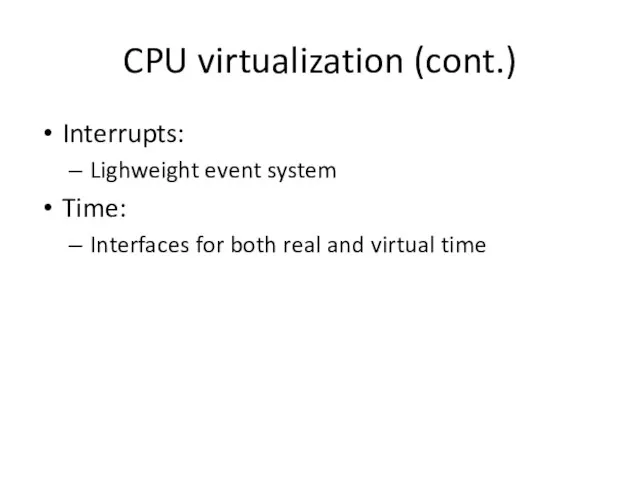
- 23. CPU virtualization (cont.) Interrupts: Lighweight event system Time: Interfaces for both real and virtual time
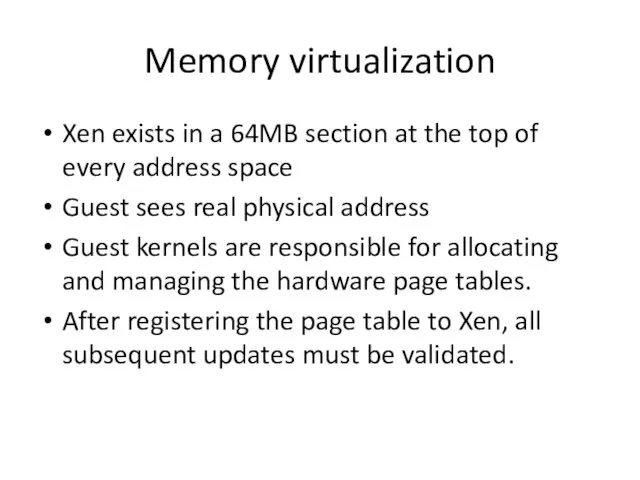
- 24. Memory virtualization Xen exists in a 64MB section at the top of every address space Guest
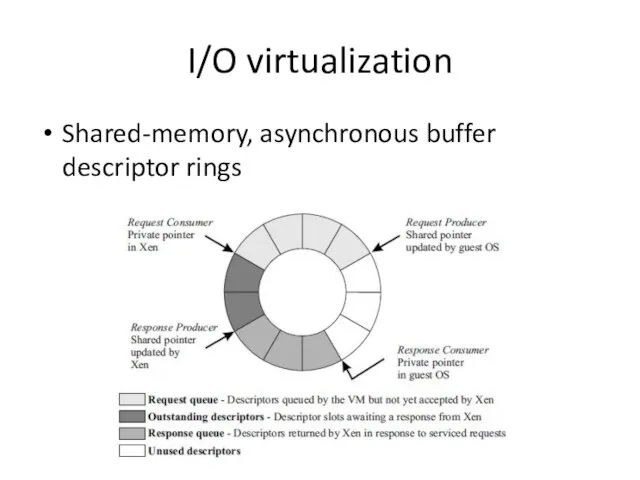
- 25. I/O virtualization Shared-memory, asynchronous buffer descriptor rings
- 26. Porting effort
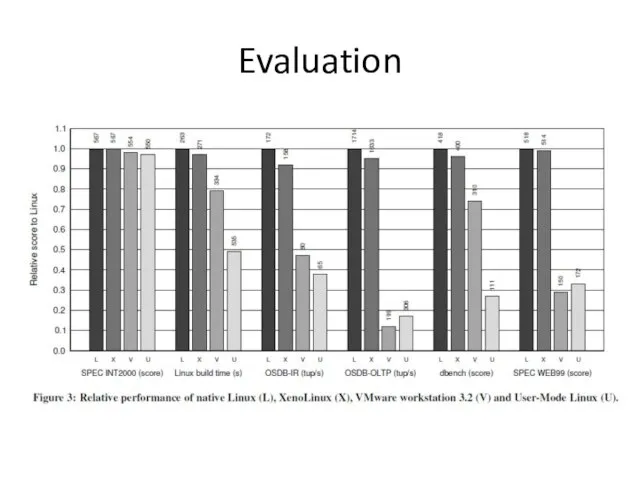
- 27. Evaluation
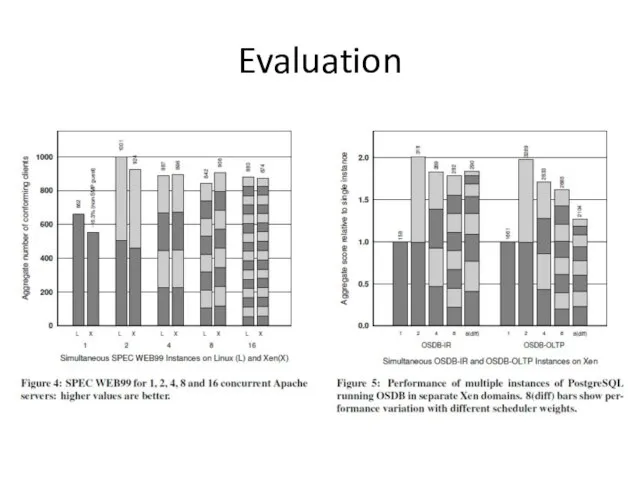
- 28. Evaluation
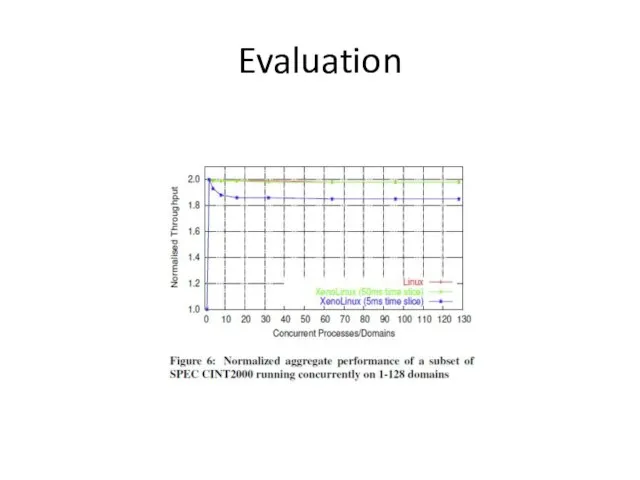
- 29. Evaluation
- 31. Скачать презентацию






 webp
webp Пьеса На Дне
Пьеса На Дне Моя история tatto
Моя история tatto Безударная гласная
Безударная гласная Классицизм в архитектуре, искусстве, литературе, музыке
Классицизм в архитектуре, искусстве, литературе, музыке Роль налогов в жизни людей
Роль налогов в жизни людей Контроль качества уборки номеров в гостинице
Контроль качества уборки номеров в гостинице Peter Piper
Peter Piper «Общественное движение людей с инвалидностью как фактор модификации публичной сферы (на примере социокультурных проектов РООИ «
«Общественное движение людей с инвалидностью как фактор модификации публичной сферы (на примере социокультурных проектов РООИ « Профессиональные стандарты педагогических работников: изменения и нововведения
Профессиональные стандарты педагогических работников: изменения и нововведения Биосфера — живая оболочка Земли
Биосфера — живая оболочка Земли Tribes and small nations
Tribes and small nations OKiR_Lektsia_5
OKiR_Lektsia_5 Презентация на тему День космонавтики 12 апреля
Презентация на тему День космонавтики 12 апреля Классификация способов сварки давлением
Классификация способов сварки давлением ЭЛЕКТРОННАЯ ШКОЛА
ЭЛЕКТРОННАЯ ШКОЛА Презентация на тему Планирование классного руководителя
Презентация на тему Планирование классного руководителя Служба войск и ее задачи
Служба войск и ее задачи НОУ Школа карвинга
НОУ Школа карвинга Презентация на тему УПРАВЛЕНИЕ ТАМОЖЕННЫМ ДЕЛОМ В ТАМОЖЕННОМ СОЮЗЕ: ТЕОРЕТИКО-ПРАВОВОЙ АСПЕКТ
Презентация на тему УПРАВЛЕНИЕ ТАМОЖЕННЫМ ДЕЛОМ В ТАМОЖЕННОМ СОЮЗЕ: ТЕОРЕТИКО-ПРАВОВОЙ АСПЕКТ  Product placement в кинематографе
Product placement в кинематографе Сделки в гражданском праве
Сделки в гражданском праве Поля листа
Поля листа The museum. Информация о студии
The museum. Информация о студии Кальцимилк молочные конфеты, обогащенные кальцием, магнием, витаминами С и D 3.
Кальцимилк молочные конфеты, обогащенные кальцием, магнием, витаминами С и D 3. Мораль как форма общественного сознания Подготовила: Студентка группы Т-114с Климушина Юлия
Мораль как форма общественного сознания Подготовила: Студентка группы Т-114с Климушина Юлия Лыжные гонки. Зимние виды спорта
Лыжные гонки. Зимние виды спорта Падежи имени существительного
Падежи имени существительного