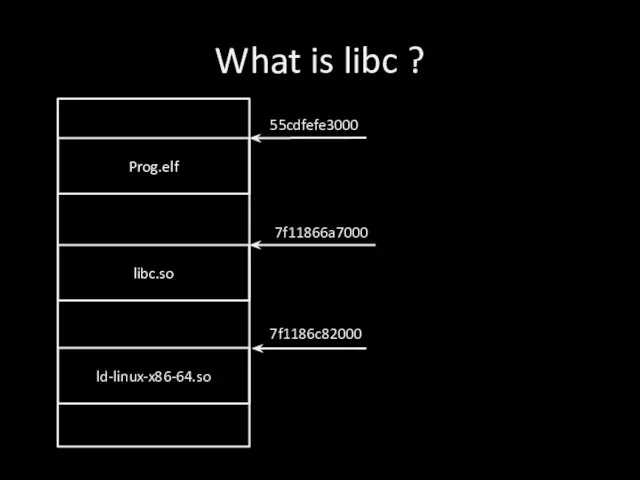
Слайд 2What is libc ?
Prog.elf
libc.so
ld-linux-x86-64.so
55cdfefe3000
7f11866a7000
7f1186c82000
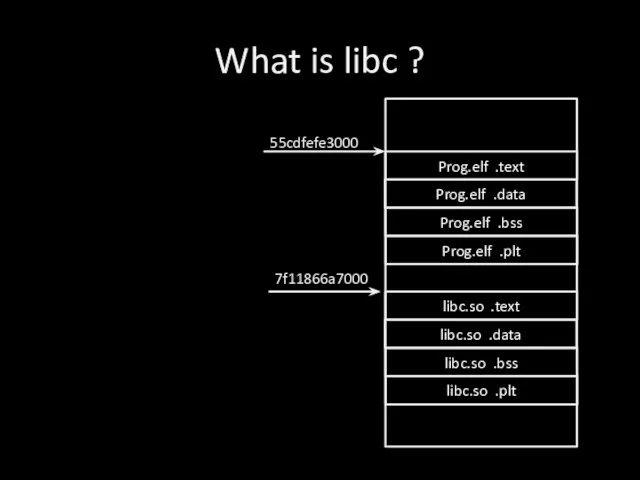
Слайд 3What is libc ?
Prog.elf .text
Prog.elf .data
Prog.elf .bss
Prog.elf .plt
libc.so .text
libc.so .data
libc.so .bss
libc.so .plt
55cdfefe3000
7f11866a7000
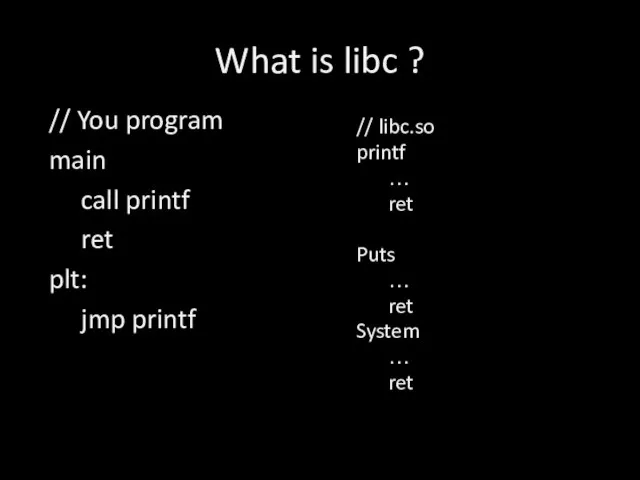
Слайд 4What is libc ?
// libc.so
printf
…
ret
Puts
…
ret
System
…
ret
// You program
main
call printf
ret
plt:
jmp printf
Слайд 5ret2libc
We know version of libc.so
We know address of libc.so
We know any function

address at libc.so
Слайд 6ret2libc
int main (){
char buf [16];
gets(buf);
}
ret from main
ebp before main
char buf[16]
![ret2libc int main (){ char buf [16]; gets(buf); } ret from main](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/858975/slide-5.jpg)
Слайд 7ret2libc
.stack ; segment with stack
Main:
push ebp
mov ebp, esp
sub esp, 16
lea edx, buf
push
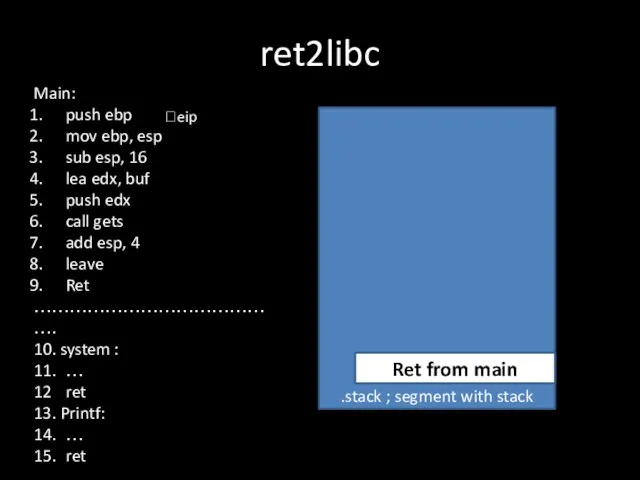
edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Ret from main
?eip
Слайд 8ret2libc
.stack ; segment with stack
Ret from main
?eip
old ebp
Main:
push ebp
mov ebp, esp
sub esp,
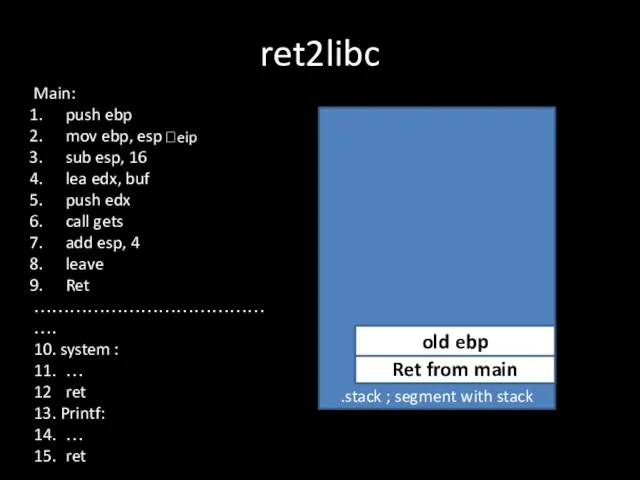
16
lea edx, buf
push edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 9ret2libc
.stack ; segment with stack
Ret from main
?eip
old ebp
ebp=8
1
2
3
4
5
6
7
8
9
Main:
push ebp
mov ebp, esp
sub esp,
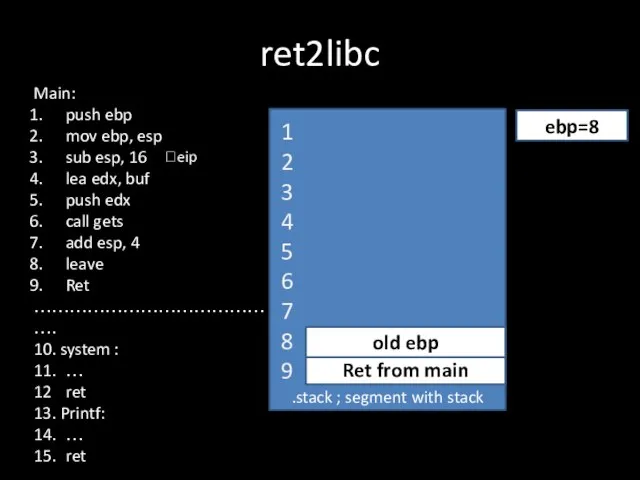
16
lea edx, buf
push edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 10ret2libc
.stack ; segment with stack
Ret from main
?eip
old ebp
ebp=8
1
2
3
4
5
6
7
8
9
Char buf[16]
Main:
push ebp
mov ebp, esp
sub
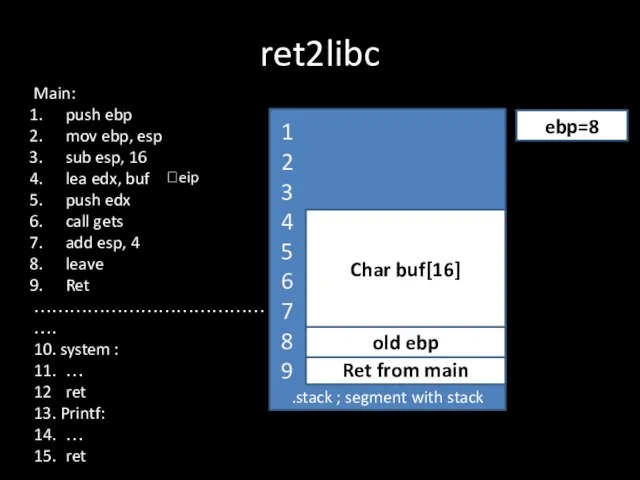
esp, 16
lea edx, buf
push edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 11ret2libc
.stack ; segment with stack
Ret from main
?eip
old ebp
ebp=8
1
2
3
4
5
6
7
8
9
Char buf[16]
edx=4
Main:
push ebp
mov ebp, esp
sub
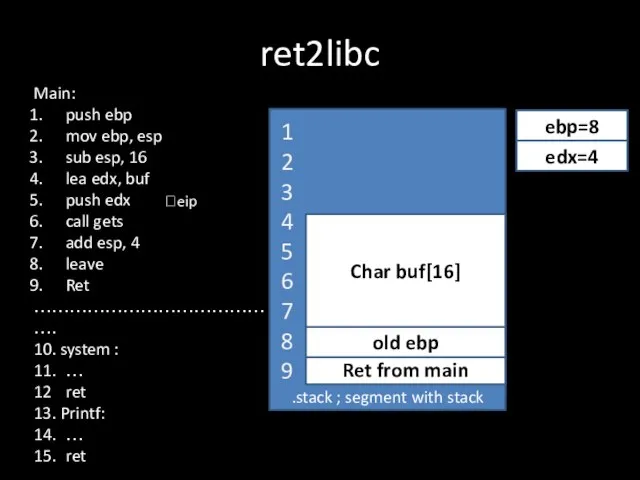
esp, 16
lea edx, buf
push edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 12ret2libc
.stack ; segment with stack
Ret from main
?eip
old ebp
ebp=8
1
2
3
4
5
6
7
8
9
Char buf[16]
edx=4
4
Main:
push ebp
mov ebp, esp
sub
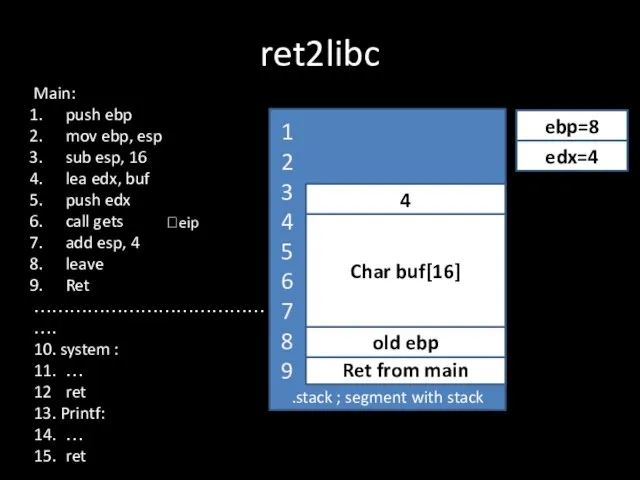
esp, 16
lea edx, buf
push edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 13ret2libc
.stack ; segment with stack
Ret from main|AAAA
?eip
old ebp|AAAA
ebp=8
1
2
3
4
5
6
7
8
9
AAAA
AAAA
AAAA
AAAA
edx=4
4
Main:
push ebp
mov ebp, esp
sub esp,
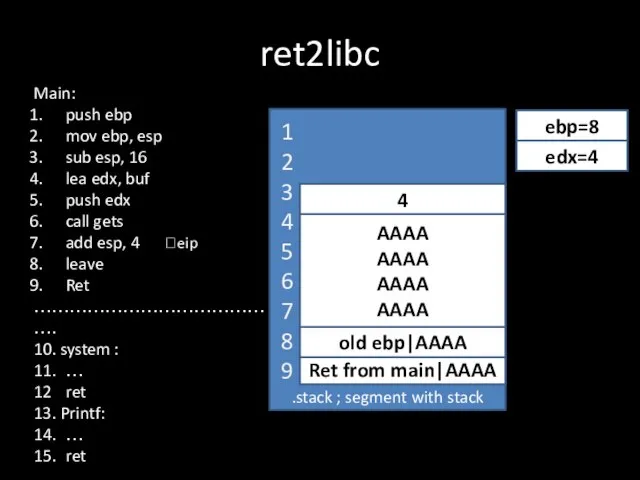
16
lea edx, buf
push edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 14ret2libc
.stack ; segment with stack
Ret from main|AAAA
?eip
old ebp|AAAA
ebp=8
1
2
3
4
5
6
7
8
9
AAAA
AAAA
AAAA
AAAA
edx=4
Main:
push ebp
mov ebp, esp
sub esp,
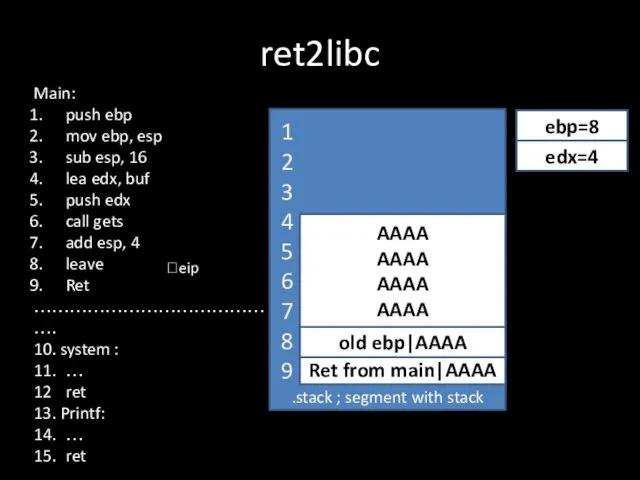
16
lea edx, buf
push edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 15ret2libc
.stack ; segment with stack
Ret from main|syscall
?eip
ebp=AAAA
1
2
3
4
5
6
7
8
9
edx=4
Main:
push ebp
mov ebp, esp
sub esp, 16
lea
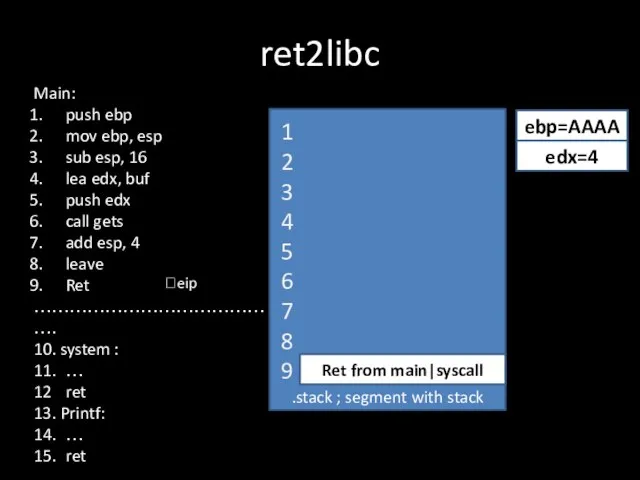
edx, buf
push edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 19ret2libc
.stack ; segment with stack
Ret from main|syscall
?eip
ebp=AAAA
1
2
3
4
5
6
7
8
9
edx=4
Main:
push ebp
mov ebp, esp
sub esp, 16
lea
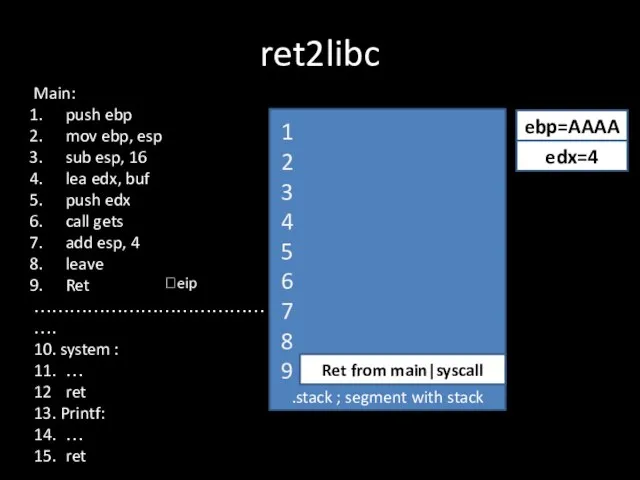
edx, buf
push edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 209. ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
ret2libc
.stack ; segment with stack
?eip
ebp=AAAA
1
2
3
4
5
6
7
8
9
10
11
edx=4

Слайд 219. ret
…………………………………….
10. system:
11. …
12 ret
13. Printf:
14. …
15. ret
ret2libc
.stack ; segment with stack
?eip
ebp=AAAA
1
2
3
4
5
6
7
8
9
10
11
edx=4
Ret from main|syscall
Ref to “/bin/sh”
Ret
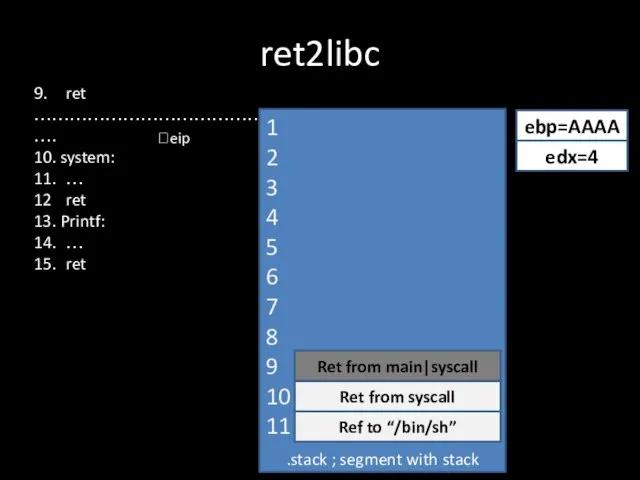
from syscall
Слайд 24What about randomization
/proc/sys/kernel/randomize_va_space
0 – No randomization. Everything is static.
1 – Conservative randomization.

Shared libraries, stack, mmap(), VDSO and heap are randomized.
2 – Full randomization. In addition to elements listed in the previous point, memory managed through brk() is also randomized.
Слайд 25Static compile
Prog.elf
libc.so
ld-linux-x86-64.so
55cdfefe3000
7f11866a7000
7f1186c82000
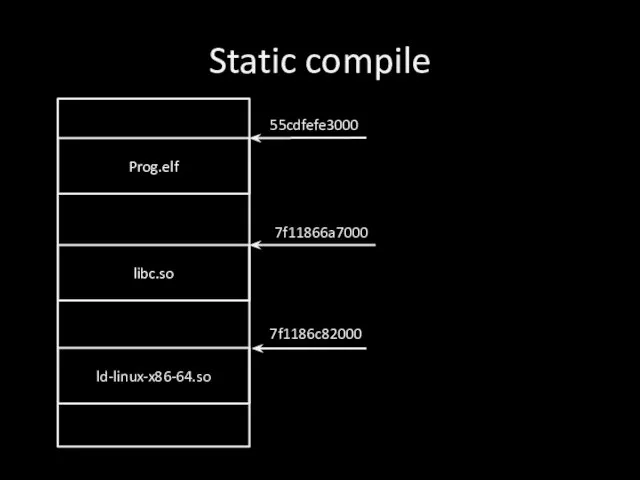
Слайд 26Static compile (-s)
Prog.elf
libc.so
ld-linux-x86-64.so
Prog.elf
libc.so
ld-linux-x86-64.so
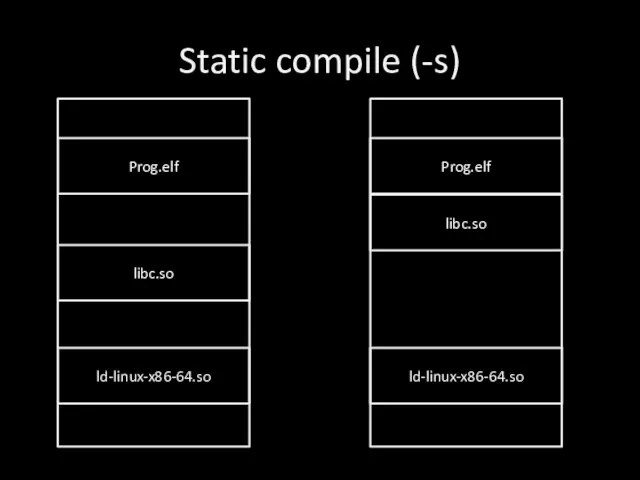
Слайд 27Static compile (-s)
Works in any linux with any libc installed
ELF contains entire

libraries
Very big binary
You can find many functions an gadgets - dangerous
Слайд 28GDB commands
gdb:
maint info sections – show sections
shell ps aux | grep test

– show process pid
cat /proc/[PID]/maps – show sections of process
find [START ADDRESS], [END ADDRESS], “[STRING]”
shell:
ldd test




![ret2libc int main (){ char buf [16]; gets(buf); } ret from main](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/858975/slide-5.jpg)





















 Ищем работу в сети. Занятие 9
Ищем работу в сети. Занятие 9 Planbus. Сервис планирования сложных автобусных маршрутов
Planbus. Сервис планирования сложных автобусных маршрутов Спрашивай взрослых
Спрашивай взрослых База данных Справочник отелей города
База данных Справочник отелей города IT технологии в гостницах
IT технологии в гостницах Классификация ИТ
Классификация ИТ Циклическая структура. Построение паркетов
Циклическая структура. Построение паркетов Topslide. Дизайн, эффективность, скорость
Topslide. Дизайн, эффективность, скорость Электронная почта. ВСР № 17
Электронная почта. ВСР № 17 Разработка приложения Test Creator
Разработка приложения Test Creator Безопасность информационных систем. Лекция 1
Безопасность информационных систем. Лекция 1 Механизм обработки и генерирования исключительных ситуаций. Лекция 21
Механизм обработки и генерирования исключительных ситуаций. Лекция 21 Базовые алгоритмические конструкции. Лекция 5
Базовые алгоритмические конструкции. Лекция 5 Система мониторинга для организации
Система мониторинга для организации Покупка в интернет-магазине
Покупка в интернет-магазине Базовые показатели эффективности (БПЭ)
Базовые показатели эффективности (БПЭ) Система автоматизированного проектирования (САПР)
Система автоматизированного проектирования (САПР) Автоматический подбор комплектующих ПК. PCHouse
Автоматический подбор комплектующих ПК. PCHouse Знакомство с компьютером
Знакомство с компьютером Введение в разработку приложений для смартфонов на OC Android
Введение в разработку приложений для смартфонов на OC Android Отдел реализации информационно-медийных проектов и программ
Отдел реализации информационно-медийных проектов и программ Знакомство с языками программирования
Знакомство с языками программирования Триггеры в презентации. Моя педагогическая инициатива
Триггеры в презентации. Моя педагогическая инициатива Информатика. Подготовка к ЕГЭ
Информатика. Подготовка к ЕГЭ Целые числа. Ограничение, связанное с разрядностью архитектуры
Целые числа. Ограничение, связанное с разрядностью архитектуры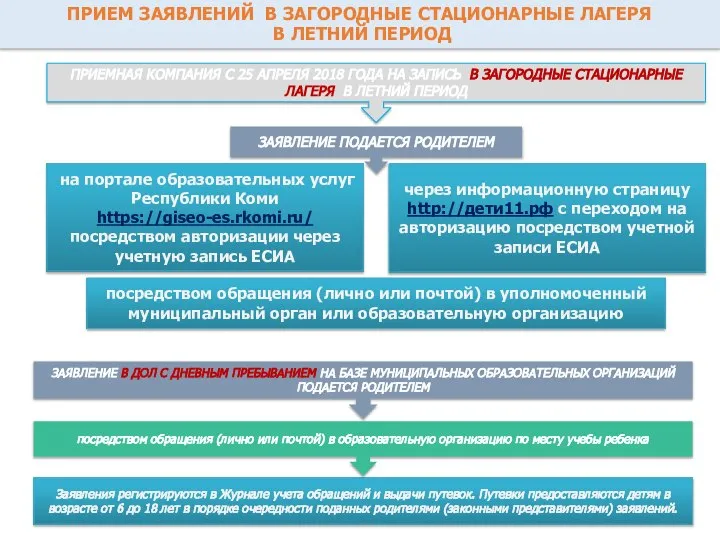 Прием заявлений в загородные стационарные лагеря в летний период
Прием заявлений в загородные стационарные лагеря в летний период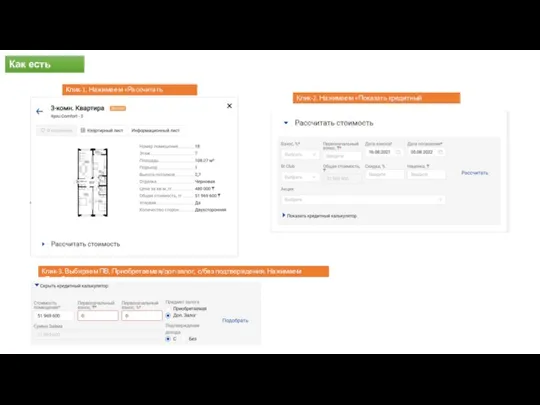 СРМ Калькулятор
СРМ Калькулятор Чайковский индустриальный колледж. Макет
Чайковский индустриальный колледж. Макет