Содержание
- 2. Understand the core of Operations Security (OPSEC) Define & identify targets and threats Establish countermeasures Identify
- 3. What is Operation Security…? Have you ever taken precautions against Someone… …breaking into your house while
- 4. OPSEC is a risk management instrument that enables a manager or commander to view an operation
- 5. Identify Critical Information Analyze Threats Discover Vulnerabilities Assess Risks Develop Countermeasures What is Operation Security …?
- 6. Identify Critical Information: Credit card numbers, travel dates, passwords, patterns, changes in patterns, inspection results, information
- 7. Discover Vulnerabilities: Flow of information, operations, timing of events, how an adversary would acquire the information,
- 8. Develop Countermeasures: are based on the vulnerabilities and inherent risks. What is Operation Security …?
- 9. Viruses and Other Malicious Content computer viruses have got a lot of publicity one of a
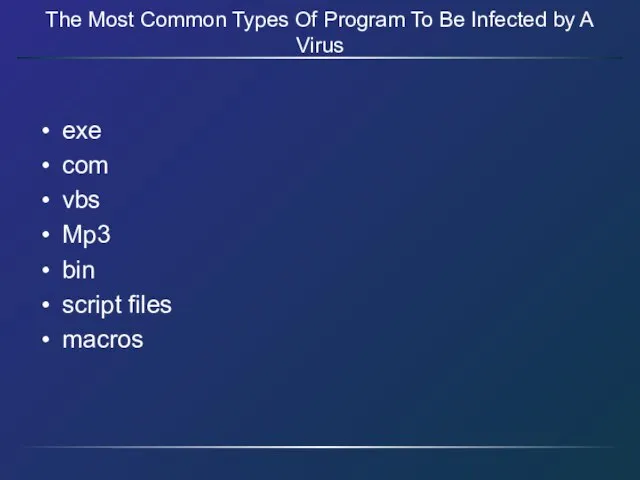
- 10. The Most Common Types Of Program To Be Infected by A Virus exe com vbs Mp3
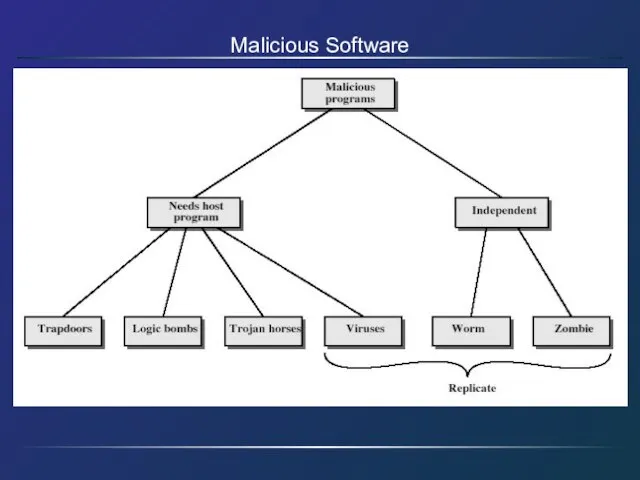
- 11. Malicious Software
- 12. Trapdoors secret entry point into a program allows those who know access bypassing usual security procedures
- 13. Logic Bomb one of oldest types of malicious software code embedded in legitimate program activated when
- 14. Trojan Horse program with hidden side-effects which is usually superficially attractive eg game, s/w upgrade etc
- 15. Zombie program which secretly takes over another networked computer then uses it to indirectly launch attacks
- 16. Viruses a piece of self-replicating code attached to some other code propagates itself & carries a
- 17. Virus Operation virus phases: dormant – waiting on trigger event propagation – replicating to programs/disks triggering
- 18. Types of Viruses - can classify on basis of how they attack parasitic virus memory-resident virus
- 19. Macro Virus macro code attached to some data file interpreted by program using file eg Word/Excel
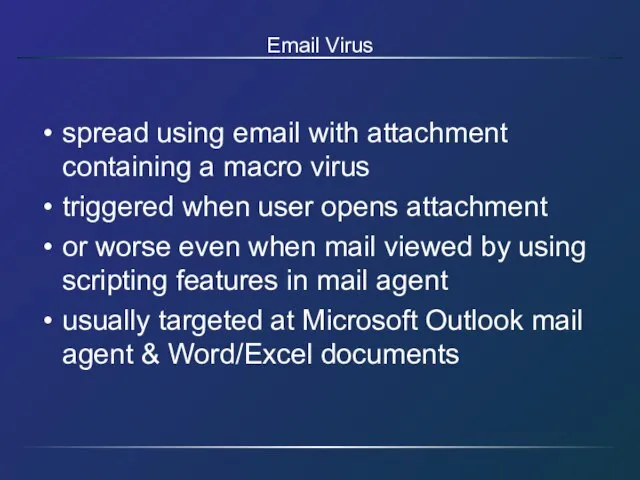
- 20. Email Virus spread using email with attachment containing a macro virus triggered when user opens attachment
- 21. Worms replicating but not infecting program typically spreads over a network using users distributed privileges or
- 22. Worm Operation worm phases like those of viruses: dormant propagation search for other systems to infect
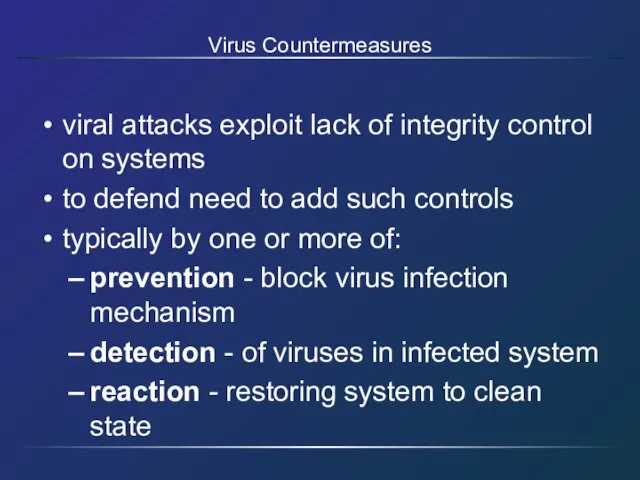
- 23. Virus Countermeasures viral attacks exploit lack of integrity control on systems to defend need to add
- 24. Summary have considered: various malicious programs trapdoor, logic bomb, trojan horse, zombie viruses worms countermeasures
- 25. Public Key Cryptosystem Essential steps of public key cryptosystem Each end generates a pair of keys
- 26. RSA (public key encryption) Alice wants Bob to send her a message. She: selects two (large)
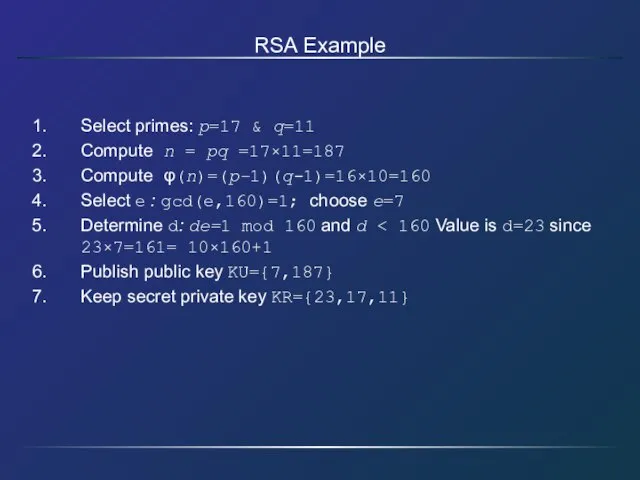
- 27. RSA Example Select primes: p=17 & q=11 Compute n = pq =17×11=187 Compute φ(n)=(p–1)(q-1)=16×10=160 Select e
- 28. RSA Example cont sample RSA encryption/decryption is: given message M = 88 (nb. 88 encryption: C
- 30. Скачать презентацию






















 Поколение молодости REV 7-2014
Поколение молодости REV 7-2014 Взаимодействие агентов в многоагентных системах
Взаимодействие агентов в многоагентных системах ФАКТОГРАФИЧЕСКИЕ БАЗЫ ДАННЫХ НАЦИОНАЛЬНОЙ БИБЛИОТЕКИ БЕЛАРУСИ КАК ИСТОЧНИК ИНФОРМАЦИИ О НАЦИОНАЛЬНЫХ ОБЪЕКТАХ Кузьминич Т. Нац
ФАКТОГРАФИЧЕСКИЕ БАЗЫ ДАННЫХ НАЦИОНАЛЬНОЙ БИБЛИОТЕКИ БЕЛАРУСИ КАК ИСТОЧНИК ИНФОРМАЦИИ О НАЦИОНАЛЬНЫХ ОБЪЕКТАХ Кузьминич Т. Нац Филиппова Елена Константиновна – учитель Филиппова Елена Константиновна – учитель русского языка и литературы Квалификационная
Филиппова Елена Константиновна – учитель Филиппова Елена Константиновна – учитель русского языка и литературы Квалификационная Новости недели. Новосибирск
Новости недели. Новосибирск Художники Сенгилеевского района
Художники Сенгилеевского района ПрезентацияРаздел 2.2
ПрезентацияРаздел 2.2 Международные модели управления персоналом
Международные модели управления персоналом Цели внедрения системы бюджетирования
Цели внедрения системы бюджетирования Деление плоскости на четыре части, в зарисовке
Деление плоскости на четыре части, в зарисовке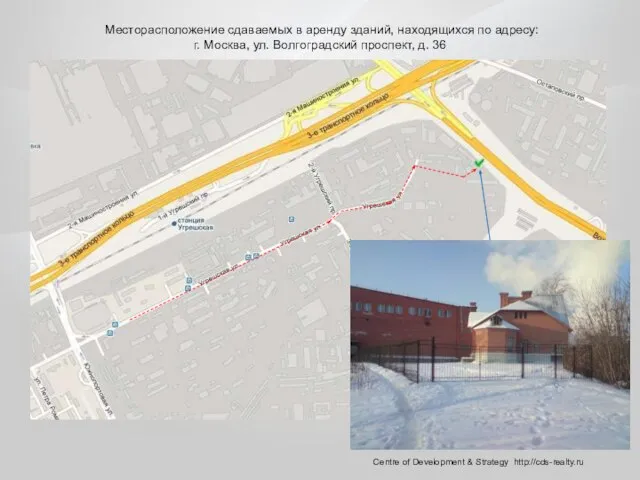 Месторасположение сдаваемых в аренду зданий, находящихся по адресу: г. Москва, ул. Волгоградский проспект, д. 36
Месторасположение сдаваемых в аренду зданий, находящихся по адресу: г. Москва, ул. Волгоградский проспект, д. 36 Филимоновская игрушка. Фотоотчет
Филимоновская игрушка. Фотоотчет Фридрих Шиллер
Фридрих Шиллер Презентация на тему Особые экономические зоны стран мира
Презентация на тему Особые экономические зоны стран мира  Фотоэлектрические модули. (Лекция 5)
Фотоэлектрические модули. (Лекция 5) The Victorian Era 1837 -1901
The Victorian Era 1837 -1901 Династический кризис 1825 г. Выступление декабристов
Династический кризис 1825 г. Выступление декабристов ВЕЛИКАЯ ОТЕЧЕСТВЕННАЯ ВОЙНА СОВЕТСКОГО СОЮЗА.
ВЕЛИКАЯ ОТЕЧЕСТВЕННАЯ ВОЙНА СОВЕТСКОГО СОЮЗА. Электронное взаимодействие между организациями ислужбой занятости населения
Электронное взаимодействие между организациями ислужбой занятости населения Порядок подачи заявления о преступлении
Порядок подачи заявления о преступлении Избушка
Избушка Сказочный мир Шарля Перро
Сказочный мир Шарля Перро ПОП-АРТ
ПОП-АРТ Осенние поделки
Осенние поделки Управление эмоциями
Управление эмоциями КОТЕЛЬНАЯ 4 Х 15 МВт
КОТЕЛЬНАЯ 4 Х 15 МВт Основные этапы разработки ООП
Основные этапы разработки ООП «Свирель серебряного века»
«Свирель серебряного века»