Содержание
- 2. Thread Local Storage callbacks were discovered in 2000. However, widespread use didn’t occur until 2004. Now,
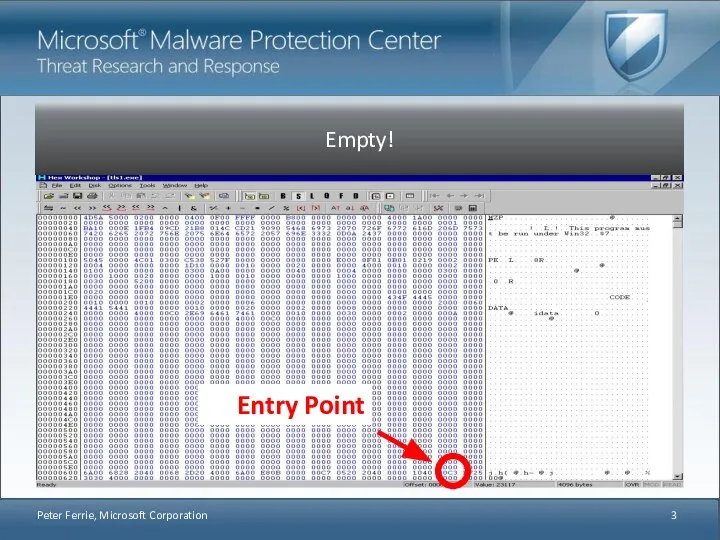
- 3. Peter Ferrie, Microsoft Corporation Entry Point
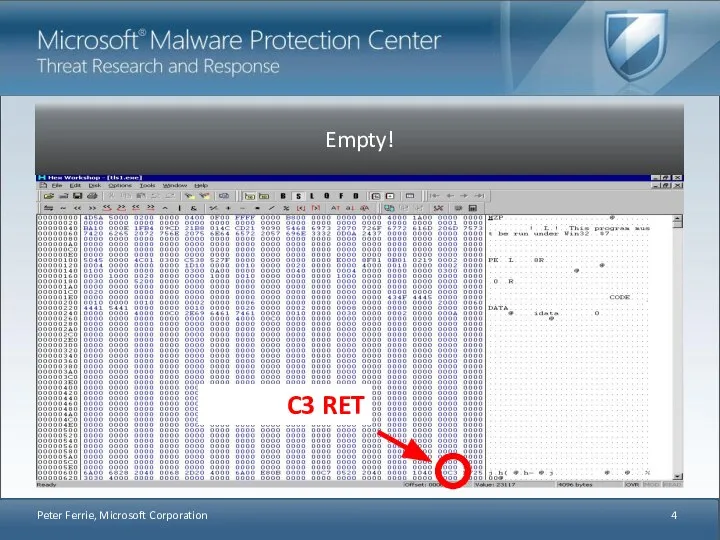
- 4. Peter Ferrie, Microsoft Corporation C3 RET
- 5. So the main file does nothing. If we assume that the structure is normal, then we
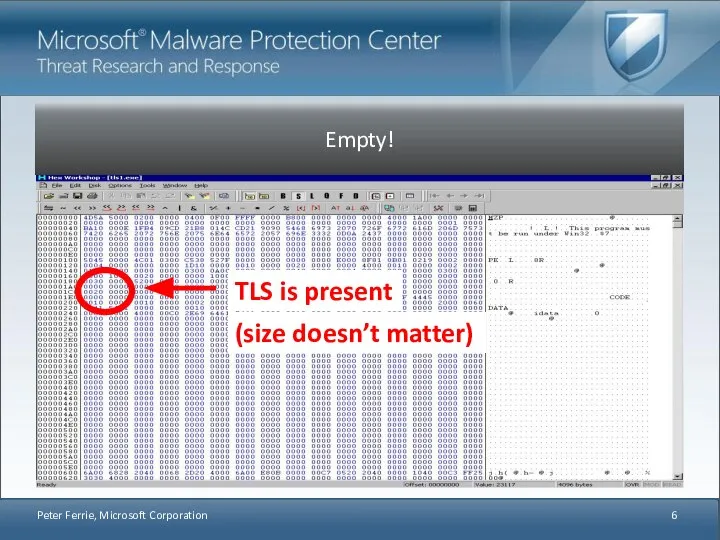
- 6. Peter Ferrie, Microsoft Corporation TLS is present (size doesn’t matter)
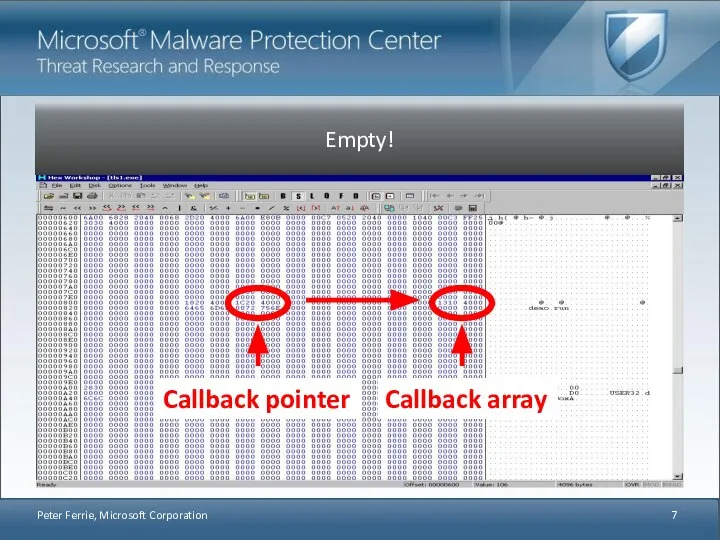
- 7. Peter Ferrie, Microsoft Corporation Callback pointer Callback array
- 8. So the search moves to the callbacks, of which there is only one... or is there?
- 9. Peter Ferrie, Microsoft Corporation
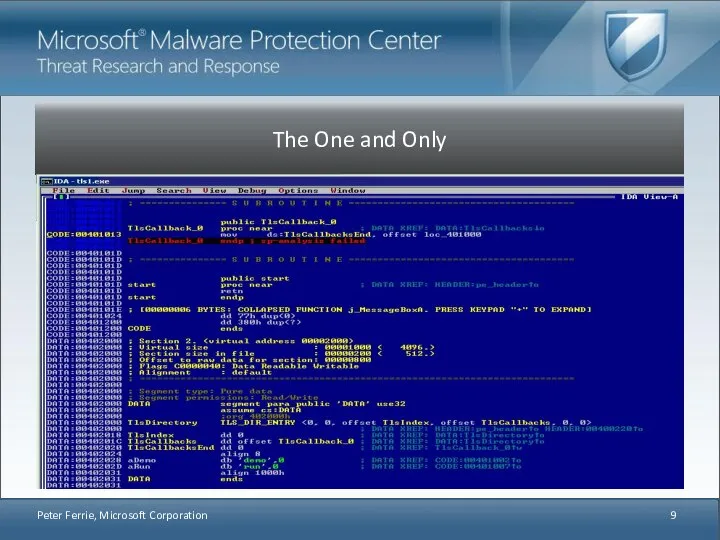
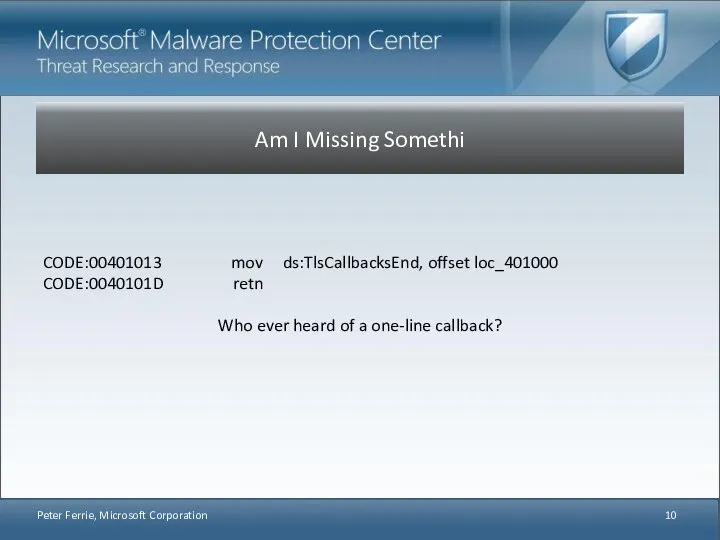
- 10. Am I Missing Somethi CODE:00401013 mov ds:TlsCallbacksEnd, offset loc_401000 CODE:0040101D retn Who ever heard of a
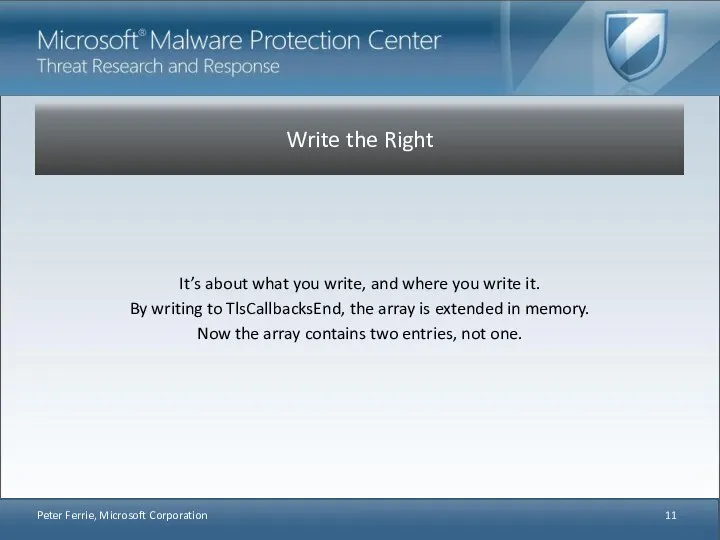
- 11. It’s about what you write, and where you write it. By writing to TlsCallbacksEnd, the array
- 12. Peter Ferrie, Microsoft Corporation
- 13. The second entry is executed after the first one returns. The array can be extended infinitely.
- 15. Скачать презентацию
 Презентация на тему Государственный строй Испании
Презентация на тему Государственный строй Испании  Понятие мультимедиа.Компьютерные презентации.
Понятие мультимедиа.Компьютерные презентации. Мастерская чудес
Мастерская чудес Ростсельмаш. Поставка запасных частей для комбайнов
Ростсельмаш. Поставка запасных частей для комбайнов Генетический алгоритм и его модификация для формирования оптимального подмножества тестов
Генетический алгоритм и его модификация для формирования оптимального подмножества тестов Референсы, Екатеринбург
Референсы, Екатеринбург Конкуренция в живой природе
Конкуренция в живой природе Decision Making
Decision Making  Проектное управление в рамках РИП через организацию работы предметно-цикловой комиссии в ЧГПГТ
Проектное управление в рамках РИП через организацию работы предметно-цикловой комиссии в ЧГПГТ Генеральный директор
Генеральный директор Казочка про фею Теплинку
Казочка про фею Теплинку Мое здоровье
Мое здоровье Видеоряд для уроков в 1 классе РАЗДЕЛ 1. «МЫ И НАША КУЛЬТУРА» – 30 часов
Видеоряд для уроков в 1 классе РАЗДЕЛ 1. «МЫ И НАША КУЛЬТУРА» – 30 часов Опера «Князь Игорь». Русская эпическая опера. Ария князя Игоря
Опера «Князь Игорь». Русская эпическая опера. Ария князя Игоря Réservoirs
Réservoirs Педагогический конфликт
Педагогический конфликт Молодежная политика и специальные программы для молодежи в библиотеках Великобритании
Молодежная политика и специальные программы для молодежи в библиотеках Великобритании Государственное общеобразовательное учреждение Гимназия № 631 Приморского района Санкт-Петербурга ПРЕДСТАВЛЯЕТ на конкурс инно
Государственное общеобразовательное учреждение Гимназия № 631 Приморского района Санкт-Петербурга ПРЕДСТАВЛЯЕТ на конкурс инно Инновационные программы. Предмет «Музицирование»
Инновационные программы. Предмет «Музицирование» Траєкторія.Шлях.Переміщення
Траєкторія.Шлях.Переміщення И. А. Гончаров (1812 – 1891)
И. А. Гончаров (1812 – 1891) Руссу Кристина 2 класс школа №14
Руссу Кристина 2 класс школа №14 Пьеса «На дне »
Пьеса «На дне » ЧАСТНЫЙ БУХГАЛТЕР
ЧАСТНЫЙ БУХГАЛТЕР Проект – презентация«Город Николаевск – на – Амуре»
Проект – презентация«Город Николаевск – на – Амуре» Введение дошкольника в мир искусства
Введение дошкольника в мир искусства Психическое здоровье
Психическое здоровье ФизАрт. Клуб физического развития
ФизАрт. Клуб физического развития