Слайд 3Objectives
What is Cyber
What is Cyber warfare
Types of Cyber Warfare
How its done
Uses

Слайд 4What is Cyber
It is a common term used computer interaction.
Cyber History
Cyber use
Слайд 6 What is Cyber warfare
It is politically motivated hacking to gain control over systems

and to spy.
Слайд 7Types of cyber warfare
1) Take control
2) Out of control

Слайд 8How it is done!
Interference
Construct code
Pick the required point
Reshape the code
Conquer

Слайд 9Interference
Different ways are adopted most common is through Electromagnetic waves.
Слайд 11Find the required point of code
Chris Domas 30 hours work:
For 15hr it
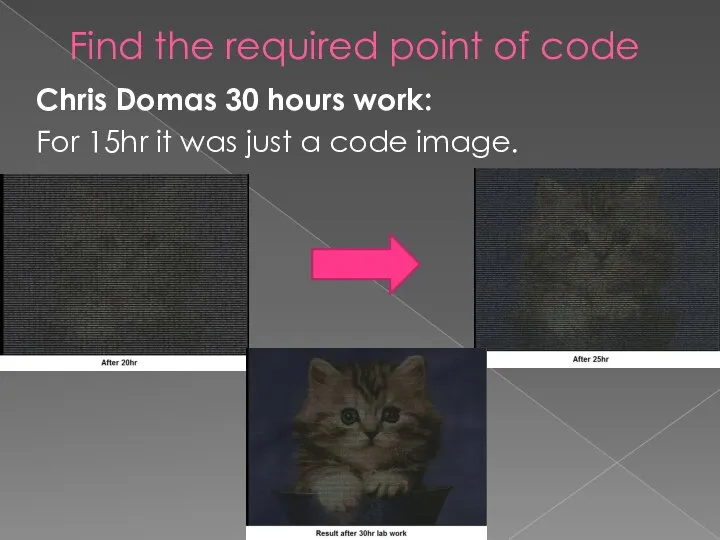
was just a code image.
Слайд 13Reshape the code
Modify according to performing task for device.
Слайд 15Uses
+ Positive uses
- Negative use

Слайд 16Conclusion
This is a beginning of a new cyber era. What your mode.












 Принцип организации и преимущества колонки-ориентированной со сжатым словарем базы данных в памяти
Принцип организации и преимущества колонки-ориентированной со сжатым словарем базы данных в памяти Делегати. Анонімні функції
Делегати. Анонімні функції Профессия репортер
Профессия репортер Евгений Валентинович Касперский
Евгений Валентинович Касперский Шаблон для презинтаций
Шаблон для презинтаций Для тестеров
Для тестеров Для обращения в ЦПК
Для обращения в ЦПК ЗЛП і її властивості
ЗЛП і її властивості Воздушно-космическая деятельность
Воздушно-космическая деятельность Рекурсивный перебор с возвратом. Семинар для учителей информатики
Рекурсивный перебор с возвратом. Семинар для учителей информатики Иинформационные технологии
Иинформационные технологии Operations on Bits
Operations on Bits С++. Язык программирования
С++. Язык программирования Протоколы сети Интернет. Протокол POP3
Протоколы сети Интернет. Протокол POP3 Учебный 2022 год с Марусей (всероссийский конкурс для учителей от VK)
Учебный 2022 год с Марусей (всероссийский конкурс для учителей от VK) Профессия гейм-дизайнер
Профессия гейм-дизайнер Информационно-поисковый язык и индексирование
Информационно-поисковый язык и индексирование Структура оператора выбор. Составление алгоритмов
Структура оператора выбор. Составление алгоритмов Правила оформления и публикации постов РДШ
Правила оформления и публикации постов РДШ Структуры и алгоритмы компьютерной обработки данных
Структуры и алгоритмы компьютерной обработки данных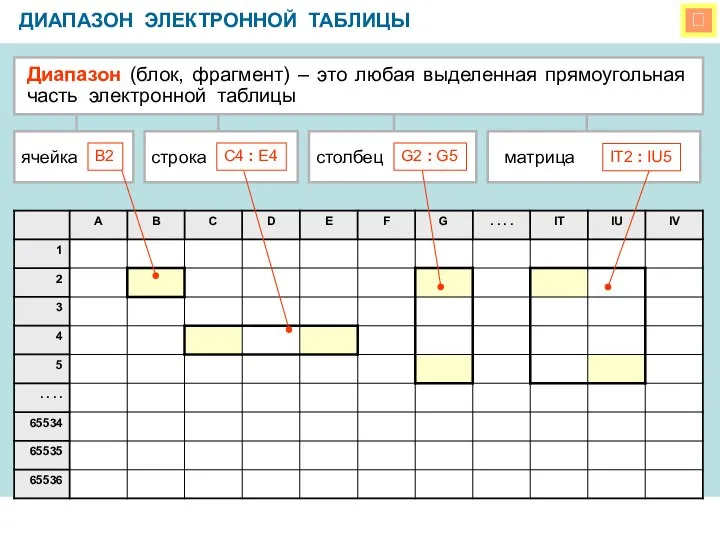 Диапазон электронной таблицы
Диапазон электронной таблицы Действия с фрагментом рисунка в графическом редакторе. 5 класс
Действия с фрагментом рисунка в графическом редакторе. 5 класс Телекоммуникационная компания интернет-провайдер ООО Аванта Телеком
Телекоммуникационная компания интернет-провайдер ООО Аванта Телеком Циклы
Циклы Макетирование с помощью таблиц
Макетирование с помощью таблиц Курс Microsoft Office
Курс Microsoft Office Лямбда-выражения
Лямбда-выражения Функции электронных таблиц Microsoft Excel
Функции электронных таблиц Microsoft Excel