Слайд 2Что такое шаблоны требований?
Шаблоны требований — это описание типичного поведения системы при

выполнении типичных операций пользователем.
Слайд 3UI Patterns
Designing Web Interfaces: Principles and Patterns for Rich Interactions.
Слайд 4UI Patterns
Designing Interfaces
Patterns for Effective Interaction Design

Слайд 5Requirement sepecification vs requirement implementation
Является ли задачей бизнес аналитика, определение как

будет построен пользовательский интерфейс?
Должен ли бизнес-аналитик думать о том какой будет интерфейс у системы?
Слайд 6Software Requirement Patterns (Best Practices)
Слайд 7User Registration Requirement Pattern
Class of users
This identifies the type of user

that is created by the registration process described by this requirement. If all users are registered in the same way, but the system treats different classes of users in different ways, explain how the user class is determined.
User details What information do we want to record about each user? You can either list every item individually, or refer to a data structure (as per the data structure requirement pattern) that defines them, or a mixture of both. Alternatively, some details can be defined in extra requirements. Indicate which information is mandatory and which is optional. Not all information about a user needs to be entered when they register: concentrate on what information the system must be able to handle, rather than on which items must be entered during registration. It's useful to divide this information into the following five categories:
Identification details, such as user ID, name, and email address-things used to distinguish this person from someone else. Sometimes other facts about a person are used to assist identification (for example date of birth), but they should be regarded as identification details in their own right only if they are essential to uniquely identify a particular person.
Authentication information, most commonly a password. It might be augmented by further information that's called upon if the user forgets their password (such as a "secret phrase" or a few questions and answers that an impostor is unlikely to know). These details indicate that a person who knows them when logging in is the same person who registered.
Facts
about the person (that aren't used for identification), such as date of birth, title, gender, address, and phone number(s).
Слайд 8User Registration Requirement Pattern
Access privileges, that define what this user is permitted

to do and see. One way is for the user registration requirement to mention that one or more "roles" can be assigned to a user. This subject is covered in greater depth in the user authorization requirement patterns-though it is the registration process that assigns at least some initial access privileges to the user.
Registration process
This can be as simple as entering information about the user, or it can involve additional steps.
Слайд 9Chronicle Requirement Pattern
Use the chronicle requirement pattern to specify that a
certain type or range of types of event (occurrence) in the life of the system must be recorded.
The type(s) of occurrence to record A chronicle requirement can specify the recording of a specific type of event or the recording of a range of types of events-in ways that can be defined quite broadly.
The information to record about each occurrence Every occurrence pertaining to a user action must include the ID of the user.
Severity (Optionally.) If the occurrence indicates a problem, the severity tells how serious it is. Either identify a severity value defined in a separate severity scheme requirement








 Социальная стратификация и мобильность
Социальная стратификация и мобильность ФормЫ обращений в английском языке как компоненты эмоциональности речи
ФормЫ обращений в английском языке как компоненты эмоциональности речи Malsharuashylyq
Malsharuashylyq Диод КД103. Диод кремниевый диффузионный
Диод КД103. Диод кремниевый диффузионный ВЫЕЗДНОЕ ЗАСЕДАНИЕ СТУДЕНЧЕСКОГО СОВЕТА 16-18 октября 2009
ВЫЕЗДНОЕ ЗАСЕДАНИЕ СТУДЕНЧЕСКОГО СОВЕТА 16-18 октября 2009 Организационный менеджмент
Организационный менеджмент Банковская система. Функции банков
Банковская система. Функции банков Фразеологизмите
Фразеологизмите Шолохов
Шолохов Реформа электроэнергетики: Финишная прямая
Реформа электроэнергетики: Финишная прямая Микрофинансирование в банковском секторе РоссииБанк развития KfW
Микрофинансирование в банковском секторе РоссииБанк развития KfW Политические партии
Политические партии Основы конституционного строя России. Конституционный строй и его принципы
Основы конституционного строя России. Конституционный строй и его принципы Интеграционные процессы в Африке
Интеграционные процессы в Африке Процессоры фирмы Intel до Pentium III
Процессоры фирмы Intel до Pentium III Восточные единоборства
Восточные единоборства Игрушки Агния Барто
Игрушки Агния Барто Автомобилестроение, авиастроение. Легкая и мебельная промышленность
Автомобилестроение, авиастроение. Легкая и мебельная промышленность Team System - фреймворк для автоматизации тестирования от Microsoft
Team System - фреймворк для автоматизации тестирования от Microsoft МОДУЛЬ «БРОНИРОВАНИЕ»
МОДУЛЬ «БРОНИРОВАНИЕ»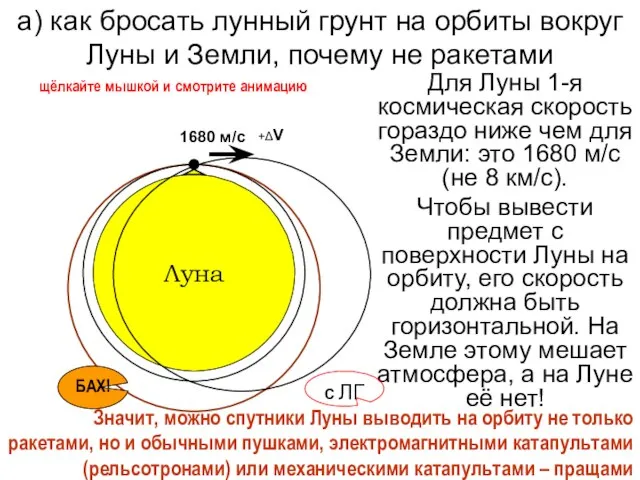 а) как бросать лунный грунт на орбиты вокруг Луны и Земли, почему не ракетами
а) как бросать лунный грунт на орбиты вокруг Луны и Земли, почему не ракетами О Т Ч Е То работе Управления записи актов гражданского состояния за 2004 год
О Т Ч Е То работе Управления записи актов гражданского состояния за 2004 год Українська мова. 4 клас
Українська мова. 4 клас PHIL 1- Lecture 3 - Week 3 moodle
PHIL 1- Lecture 3 - Week 3 moodle Эвены
Эвены Что такое предпринимательство и бизнес + конспект
Что такое предпринимательство и бизнес + конспект © МОУ СОШ №6, г.Тутаев, 2006
© МОУ СОШ №6, г.Тутаев, 2006 ТЕАТР XIX ВЕКА Западноевропейский театр романтизма и реализма Русский театр романтизма и реализма
ТЕАТР XIX ВЕКА Западноевропейский театр романтизма и реализма Русский театр романтизма и реализма