Содержание
- 2. Upon completion of this chapter, you will be able to: Explain the need for the Transport
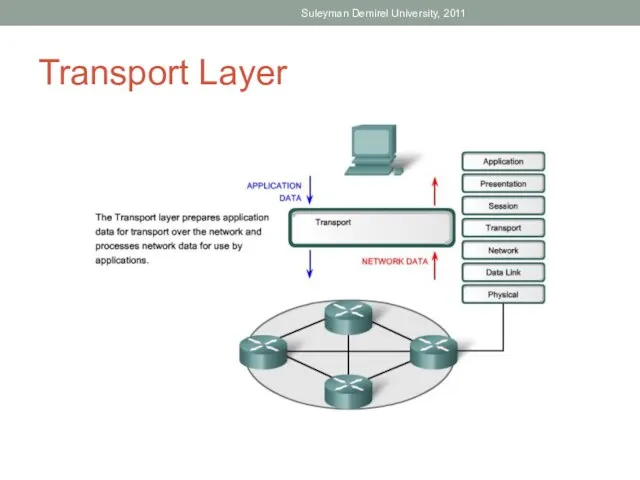
- 3. Transport Layer Suleyman Demirel University, 2011
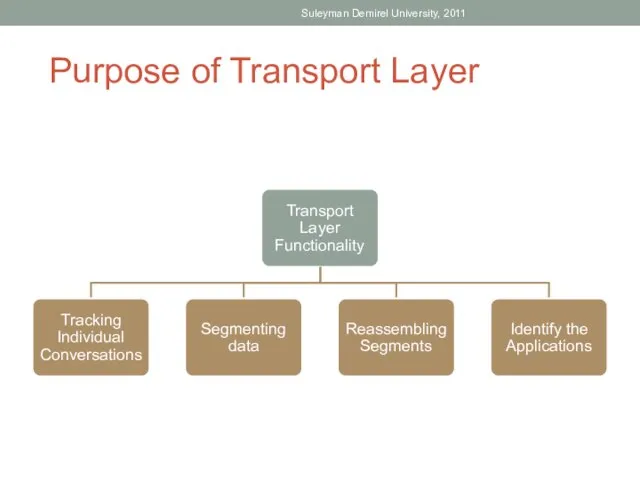
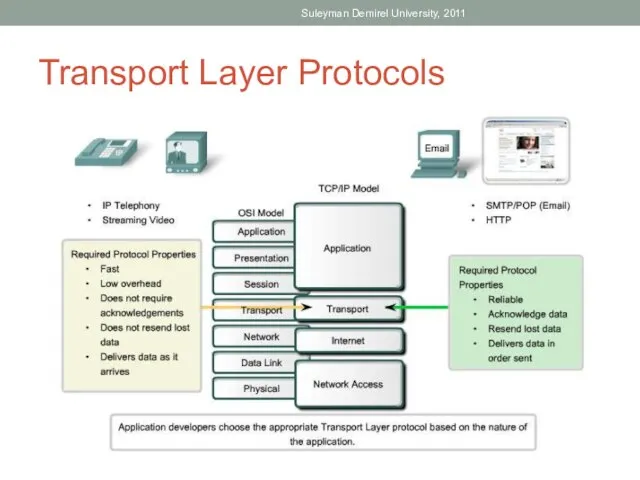
- 4. Suleyman Demirel University, 2011 Purpose of Transport Layer
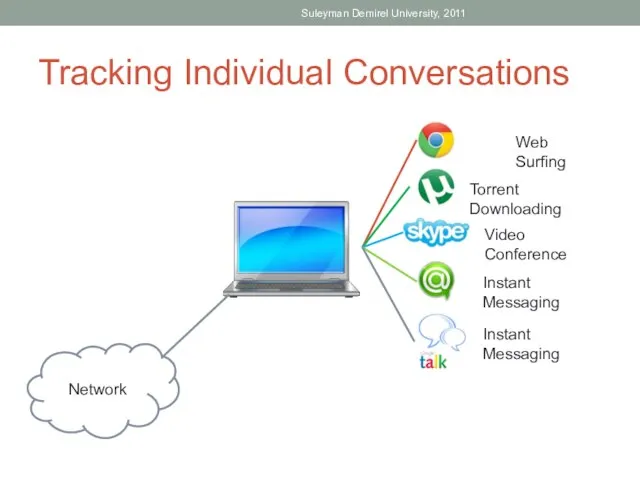
- 5. Tracking Individual Conversations Any host may have multiple applications that are communicating across the network. Each
- 6. Tracking Individual Conversations Suleyman Demirel University, 2011
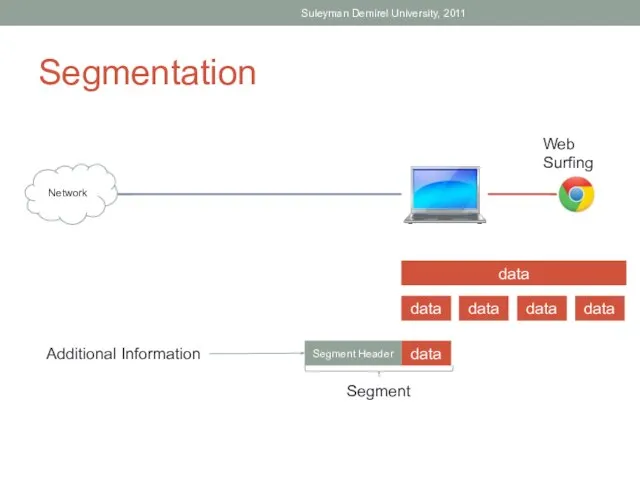
- 7. Segmenting Data The Transport layer protocols describe services that segment data from the Application layer. This
- 8. Segmentation Suleyman Demirel University, 2011 Web Surfing Network data data data data data data Segment Header
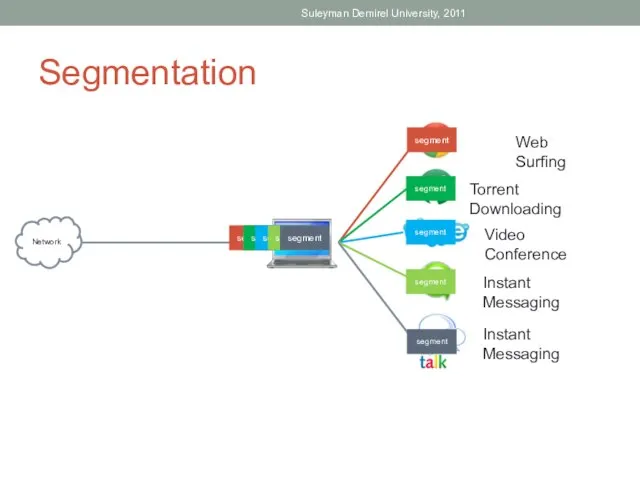
- 9. Segmentation Suleyman Demirel University, 2011 Network segment segment segment segment segment
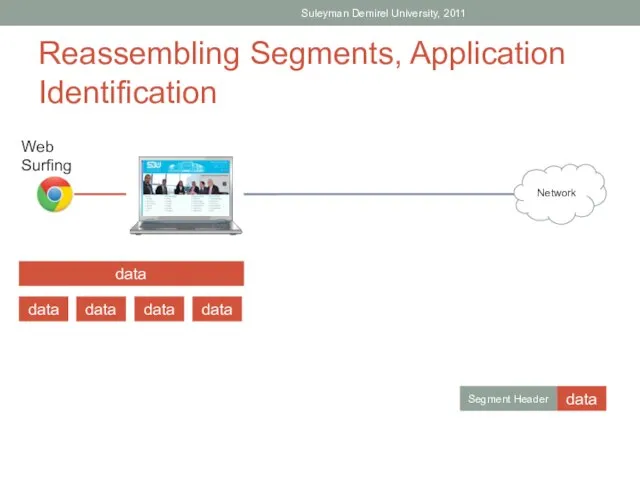
- 10. Reassembling Segments At the receiving host, each piece of data may be directed to the appropriate
- 11. Reassembling Segments, Application Identification Suleyman Demirel University, 2011 Web Surfing Network data data data data data
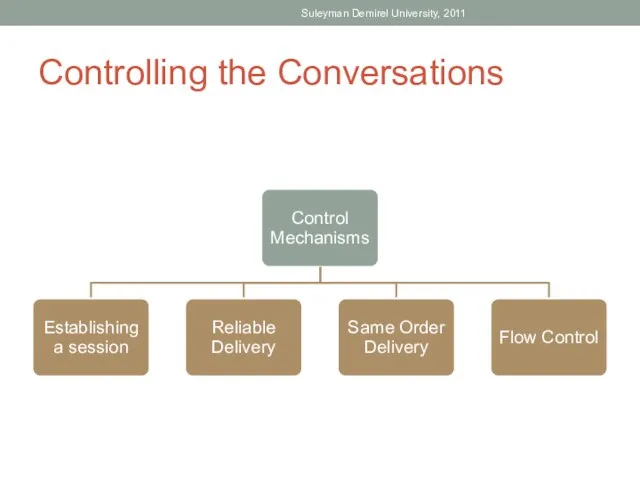
- 12. Controlling the Conversations Suleyman Demirel University, 2011
- 13. Establishing a Session The Transport layer can provide this connection orientation by creating a sessions between
- 14. Reliable Delivery For many reasons, it is possible for a piece of data to become corrupted,
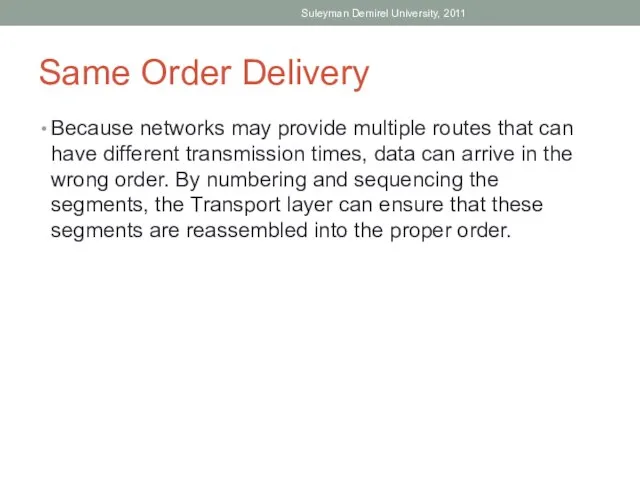
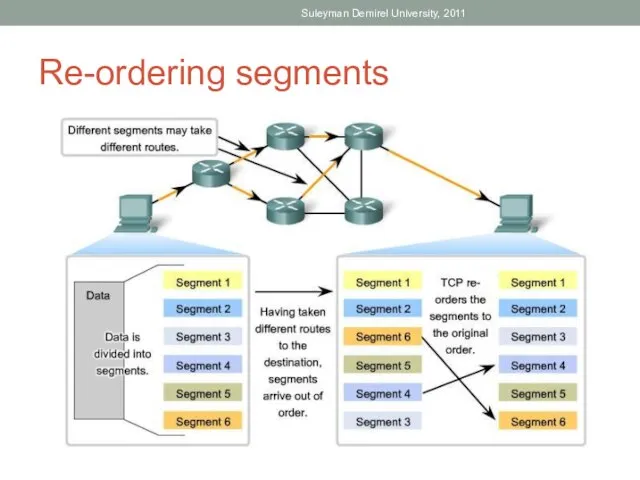
- 15. Same Order Delivery Because networks may provide multiple routes that can have different transmission times, data
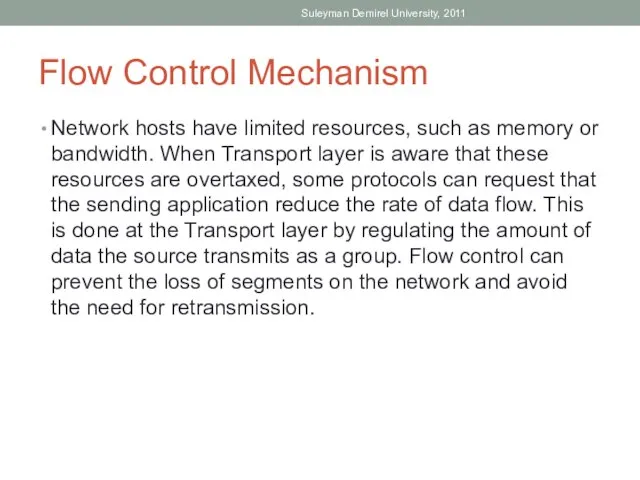
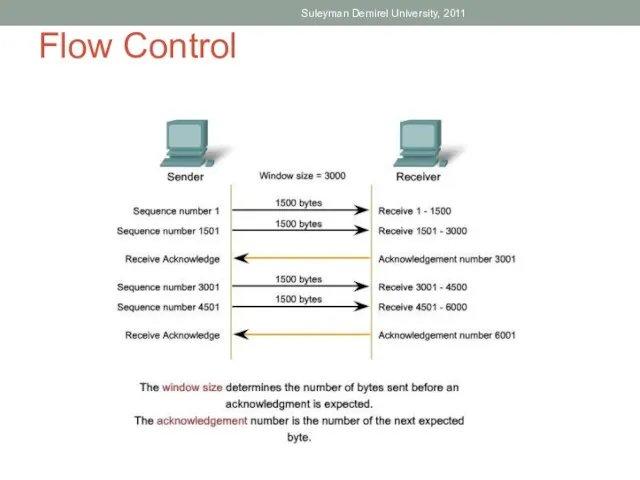
- 16. Flow Control Mechanism Network hosts have limited resources, such as memory or bandwidth. When Transport layer
- 17. Transport Layer Protocols Computers uses different types of Transport layers protocols by some reasons. What is
- 18. Question What kind of Computer Network Communications do you know? Suleyman Demirel University, 2011
- 19. Different kinds of Computer Networks Web Browsing File sharing IP Telephony Video Streaming (conference or online
- 20. Question For which of them we need reliability in delivery? Suleyman Demirel University, 2011
- 21. Question For which of them we need Speed in delivery? Suleyman Demirel University, 2011
- 22. Transport Layer Protocols Suleyman Demirel University, 2011
- 23. TCP - Transmission Control Protocol and UDP – User Datagram Protocol TCP Web Browsers E-mail File
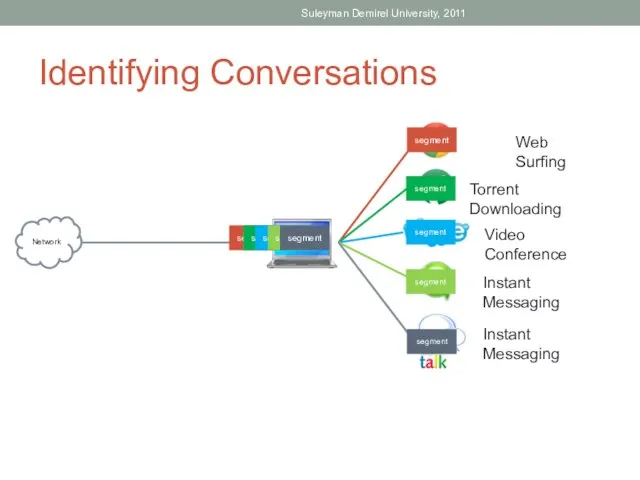
- 24. Identifying Conversations Suleyman Demirel University, 2011 Network segment segment segment segment segment
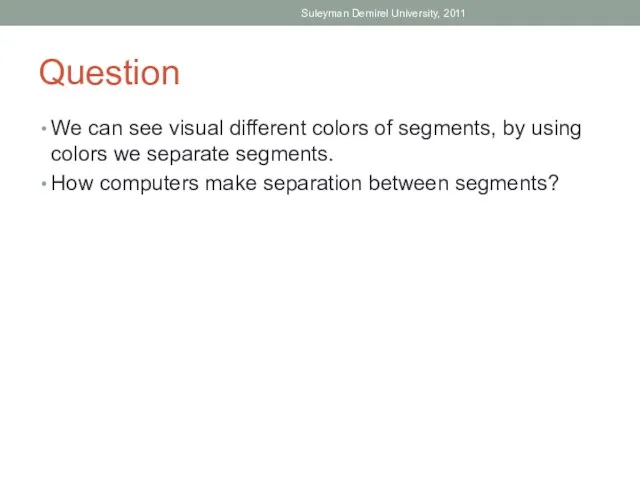
- 25. Question We can see visual different colors of segments, by using colors we separate segments. How
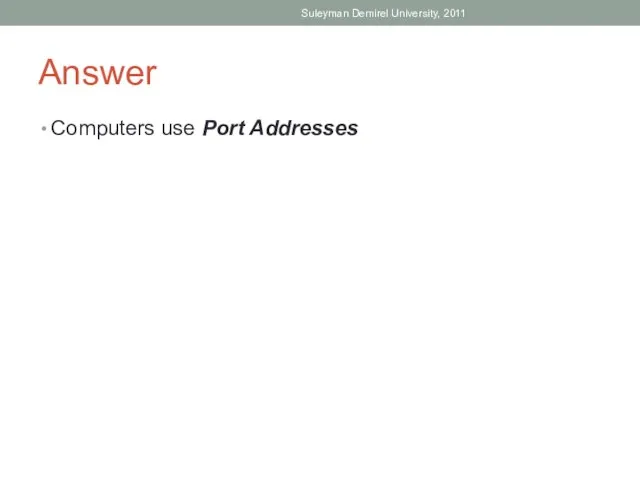
- 26. Answer Computers use Port Addresses Suleyman Demirel University, 2011
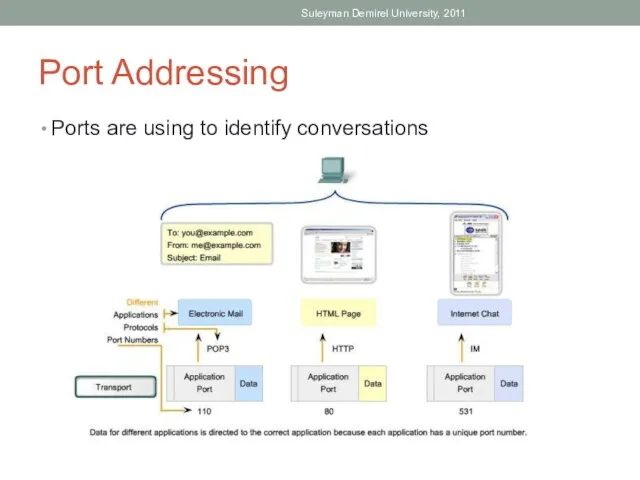
- 27. Port Addressing Ports are using to identify conversations Suleyman Demirel University, 2011
- 28. Port Addresses Well Known Ports (Numbers 0 to 1023) Registered Ports (Numbers 1024 to 49151) Dynamic
- 29. Well Known Ports Are served for services and applications. They are commonly used for applications such
- 30. Registered Ports Are assigned to user processes or applications. These processes are primarily individual applications that
- 31. Dynamic or Private Ports Also known as Ephemeral Ports, these are usually assigned dynamically to client
- 32. Question How to view states of connection in your computer? Suleyman Demirel University, 2011
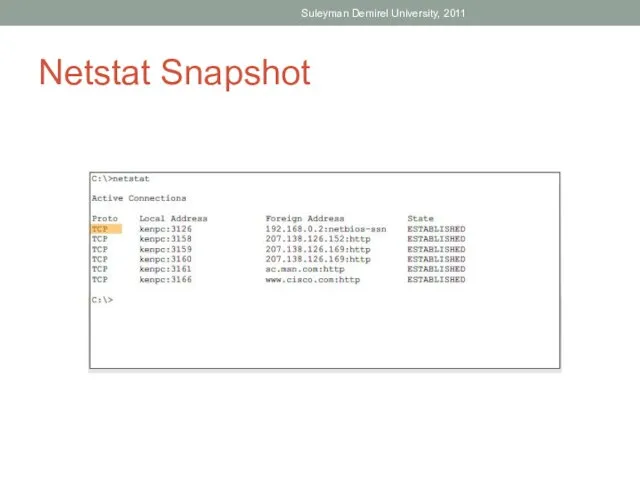
- 33. Answer Use Netstat Suleyman Demirel University, 2011
- 34. Netstat Snapshot Suleyman Demirel University, 2011
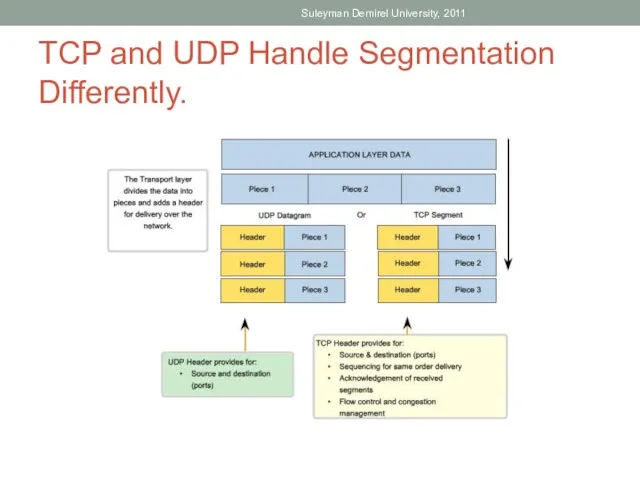
- 35. TCP and UDP Handle Segmentation Differently. Suleyman Demirel University, 2011
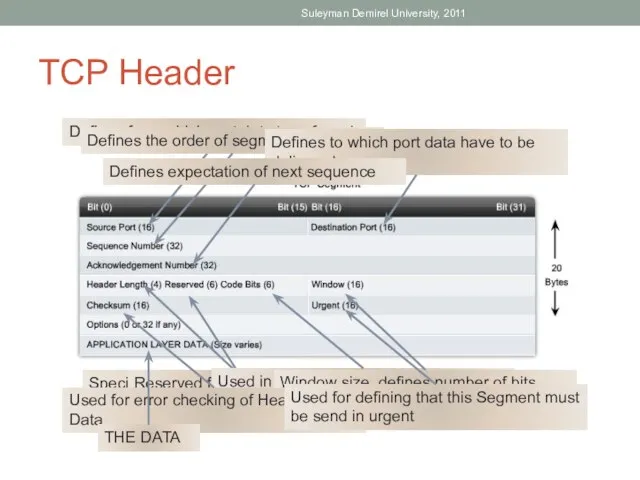
- 36. TCP Header Suleyman Demirel University, 2011
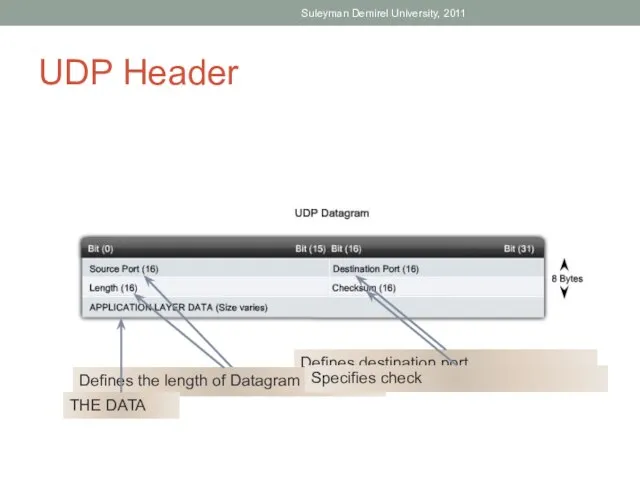
- 37. UDP Header Suleyman Demirel University, 2011
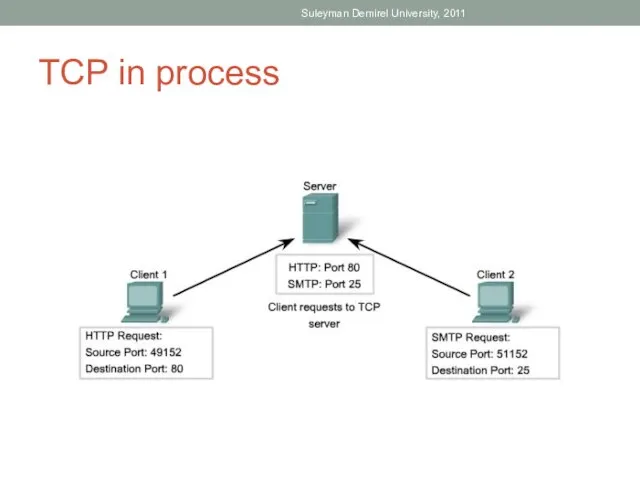
- 38. TCP in process Suleyman Demirel University, 2011
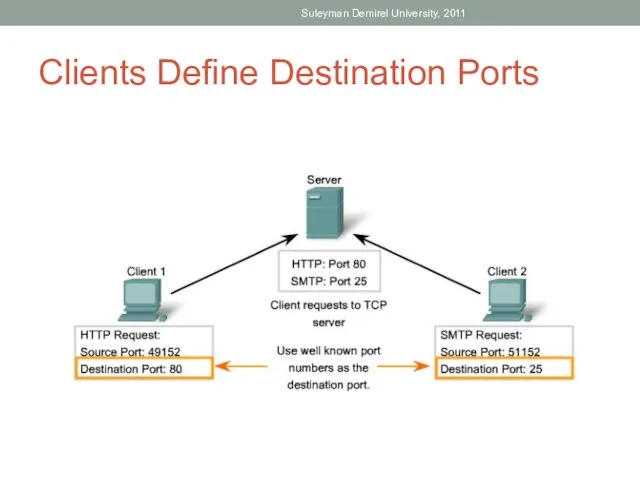
- 39. Clients Define Destination Ports Suleyman Demirel University, 2011
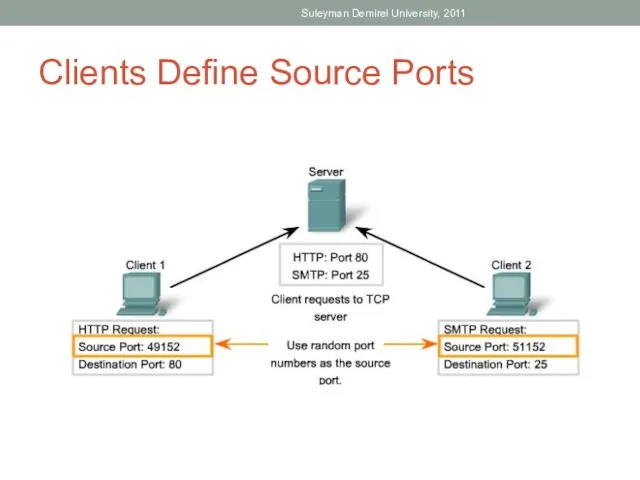
- 40. Clients Define Source Ports Suleyman Demirel University, 2011
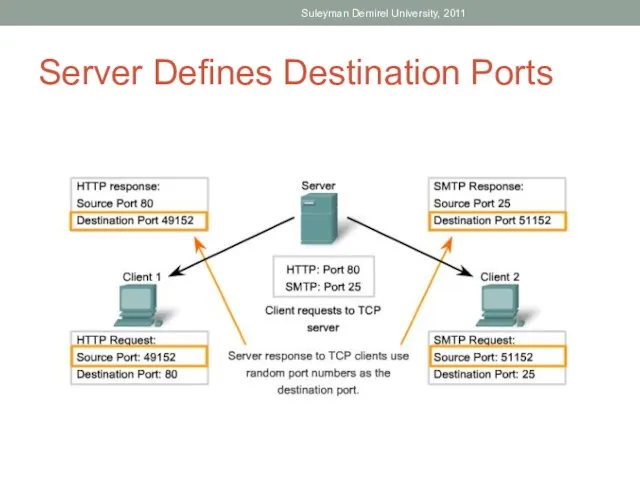
- 41. Server Defines Destination Ports Suleyman Demirel University, 2011
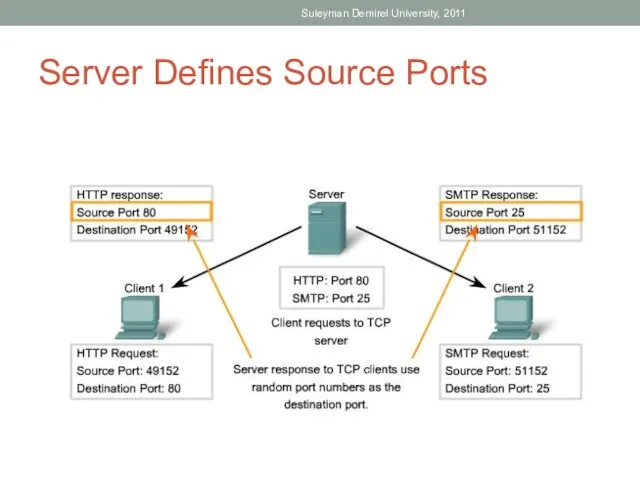
- 42. Server Defines Source Ports Suleyman Demirel University, 2011
- 43. TCP CONNECTION ESTABLISHMENT AND TERMINATION Suleyman Demirel University, 2011
- 44. Question Establishment? Suleyman Demirel University, 2011
- 45. Answer Suleyman Demirel University, 2011
- 46. Question How me make handshake? Suleyman Demirel University, 2011
- 47. Answer Suleyman Demirel University, 2011
- 48. Question How many way do we have in handshake process? Suleyman Demirel University, 2011
- 49. Answer Suleyman Demirel University, 2011
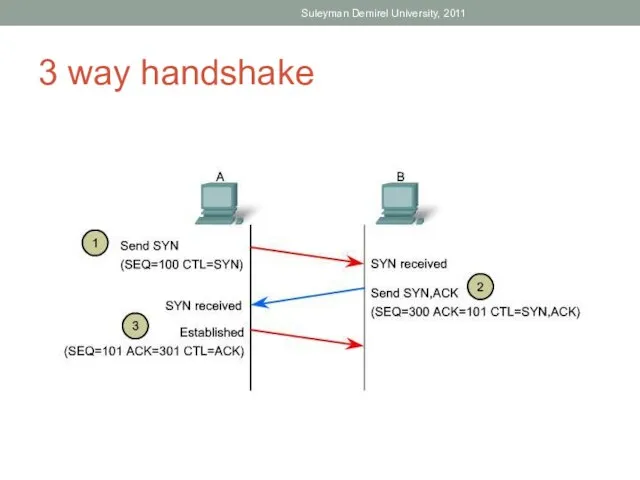
- 50. TCP Have to do Establishment before it Starts Transmission This process is called 3 way handshake
- 51. 3 way handshake Suleyman Demirel University, 2011
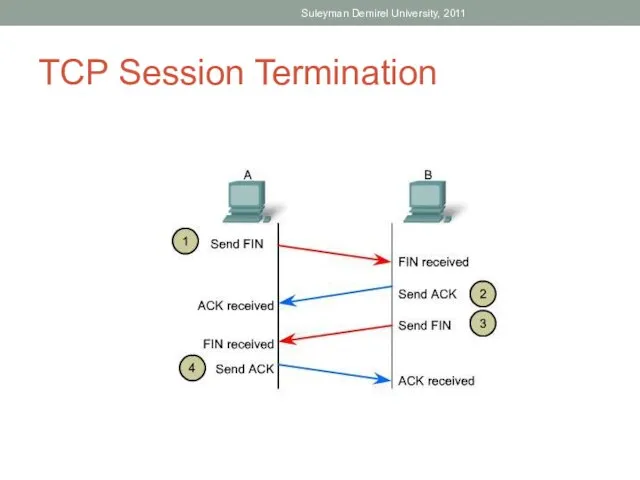
- 52. TCP Session Termination Suleyman Demirel University, 2011
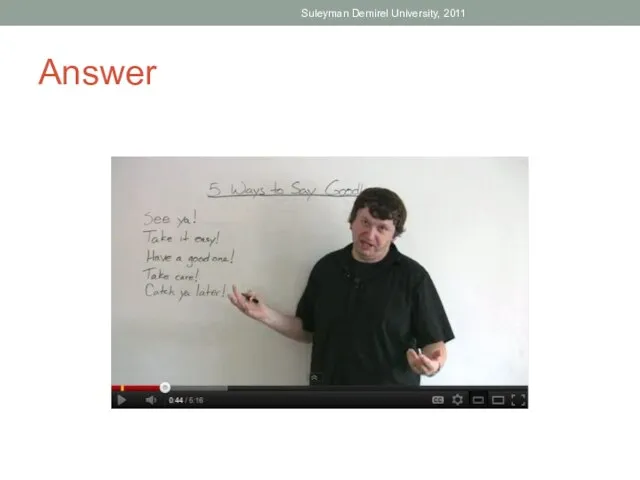
- 53. Question How people say goodbye? Suleyman Demirel University, 2011
- 54. Answer Suleyman Demirel University, 2011
- 55. REORDERING SEGMENTS AFTER RECEIVING Suleyman Demirel University, 2011
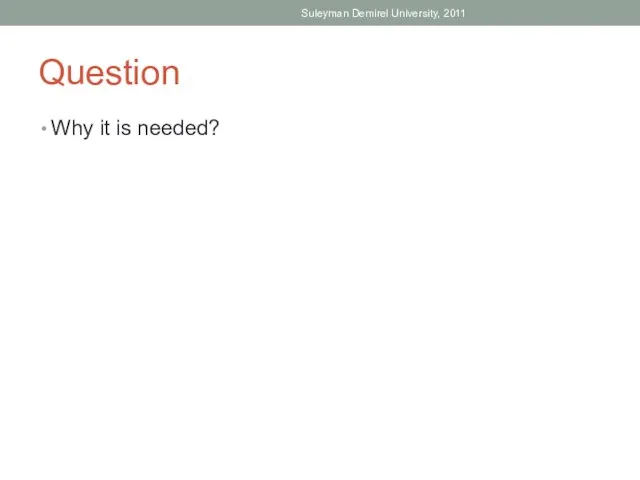
- 56. Question Why it is needed? Suleyman Demirel University, 2011
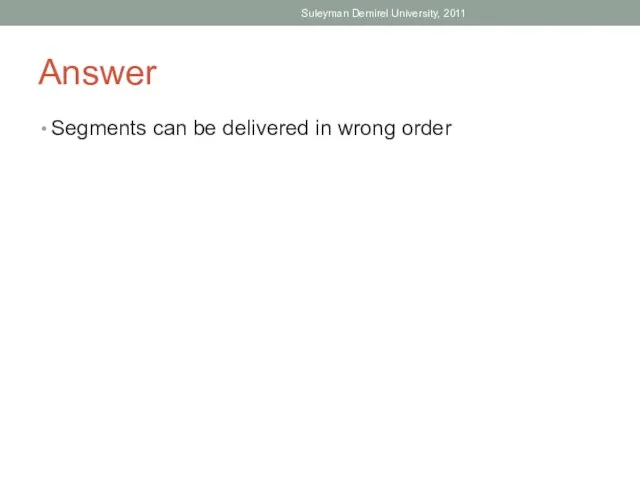
- 57. Answer Segments can be delivered in wrong order Suleyman Demirel University, 2011
- 58. Re-ordering segments Suleyman Demirel University, 2011
- 59. Acknowledgement is? Suleyman Demirel University, 2011
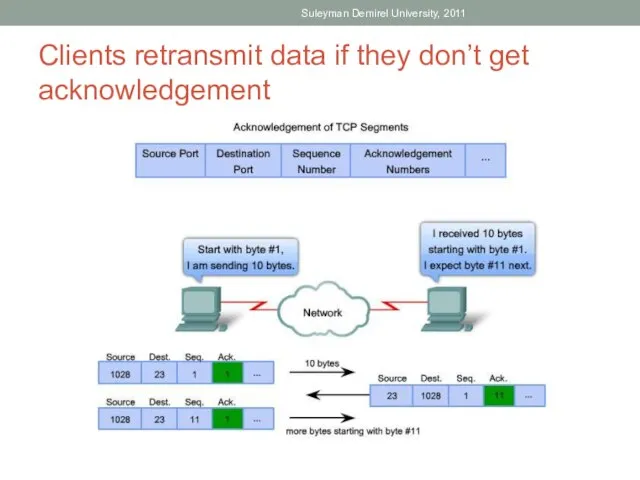
- 60. Computer Acknowledgment Computers often sends acknowledgement to each other, to confirm that they have received data.
- 61. Clients retransmit data if they don’t get acknowledgement Suleyman Demirel University, 2011
- 62. Flow Control Suleyman Demirel University, 2011
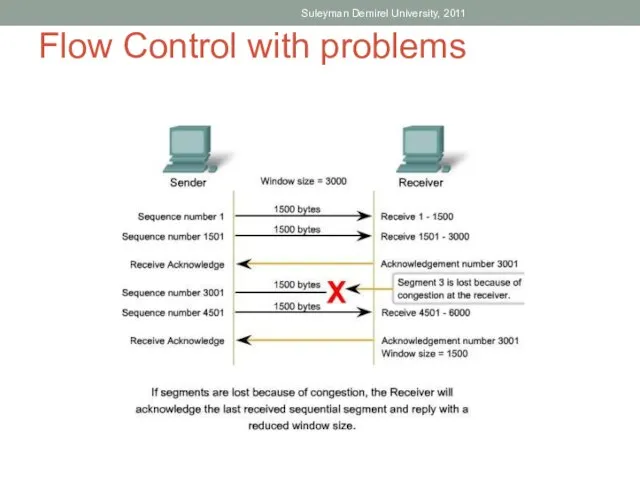
- 63. Flow Control with problems Suleyman Demirel University, 2011
- 64. UDP – USER DATAGRAM PROTOCOL Suleyman Demirel University, 2011
- 65. UDP UDP protocol is the protocol of OSI model’s 4th layer (transport layer), is not reliable
- 67. Скачать презентацию





















 Презентация на тему Четыре сестры и двенадцать братцев
Презентация на тему Четыре сестры и двенадцать братцев  Заячья капуста. Тренажёр по английскому языку
Заячья капуста. Тренажёр по английскому языку Роль социальных медиа в выводе нового бренда на рынок
Роль социальных медиа в выводе нового бренда на рынок Ночь искусств
Ночь искусств Лидерство и власть
Лидерство и власть САПОЖНИК
САПОЖНИК Отношения между понятиями
Отношения между понятиями Реализация образовательной программы для детей с ОВЗ
Реализация образовательной программы для детей с ОВЗ Белка и Стрелка. Звездные собаки
Белка и Стрелка. Звездные собаки Тотальная прозрачность. Управление информационной безопасностью в отделе продаж
Тотальная прозрачность. Управление информационной безопасностью в отделе продаж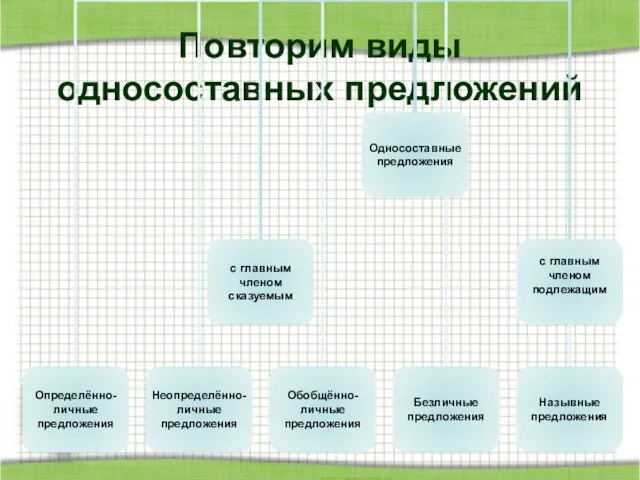 Повторим виды односоставных предложений
Повторим виды односоставных предложений Разукрасилась зима
Разукрасилась зима Об основных вопросах реализации Федерального закона от 27 июля 2010 года № 210-ФЗ «Об организации предоставления государственных и м
Об основных вопросах реализации Федерального закона от 27 июля 2010 года № 210-ФЗ «Об организации предоставления государственных и м Отчет о встрече сотрудников Университета Вустера (Великобритания) от 31 октября 2011 года
Отчет о встрече сотрудников Университета Вустера (Великобритания) от 31 октября 2011 года Очерк жизни и творчества Ивана Алексеевича Бунина
Очерк жизни и творчества Ивана Алексеевича Бунина «Вирус страха» СПИД – как актуальная проблема современности
«Вирус страха» СПИД – как актуальная проблема современности Неделя математики и информатики 25.01.10 – 30.01.10
Неделя математики и информатики 25.01.10 – 30.01.10 Еврокоды (Eurocodes). Общие положения
Еврокоды (Eurocodes). Общие положения Система развития бизнеса и обучения Сирбио
Система развития бизнеса и обучения Сирбио Лекция_Тема 3
Лекция_Тема 3 Моё будущее. Филология
Моё будущее. Филология Бренд-менеджмент
Бренд-менеджмент End your speech with a bang
End your speech with a bang Тригонометрические функции угла
Тригонометрические функции угла Финансово-экономические модели и механизмы достижения эффектов МРСО
Финансово-экономические модели и механизмы достижения эффектов МРСО Музыкальный портрет. В каждой интонации спрятан человек
Музыкальный портрет. В каждой интонации спрятан человек НОВАЯ СИСТЕМА ОПЛАТЫ ТРУДА
НОВАЯ СИСТЕМА ОПЛАТЫ ТРУДА Диагностика в начальных классах
Диагностика в начальных классах