Слайд 2Learning Objectives
Upon completion of this material, you should be able to:
Define information

security
Recount the history of computer security and how it evolved into information security
Define key terms and critical concepts of information security
List the phases of the security systems development life cycle
Describe the information security roles of professionals within an organization
Слайд 3Introduction
Information security: a “well-informed sense of assurance that the information risks and

controls are in balance.”—Jim Anderson, Emagined Security, Inc.
Security professionals must review the origins of this field to understand its impact on our understanding of information security today.
Слайд 4The History of Information Security
Computer security began immediately after the first mainframes

were developed.
Groups developed the code-breaking computations during World War II created the first modern computers.
Multiple levels of security were implemented.
Physical controls limiting access to sensitive military locations to authorized personnel
Rudimentary in defending against physical theft, espionage, and sabotage
Слайд 7The 1960s
Advanced Research Project Agency (ARPA) began to examine the feasibility of

redundant networked communications.
Larry Roberts developed the ARPANET from its inception.
Слайд 9The 1970s and 80s
ARPANET grew in popularity, as did its potential for
misuse.
Fundamental problems with ARPANET security were identified.
No safety procedures for dial-up connections to ARPANET
Nonexistent user identification and authorization to system
Слайд 10The 1970s and 80s (cont’d)
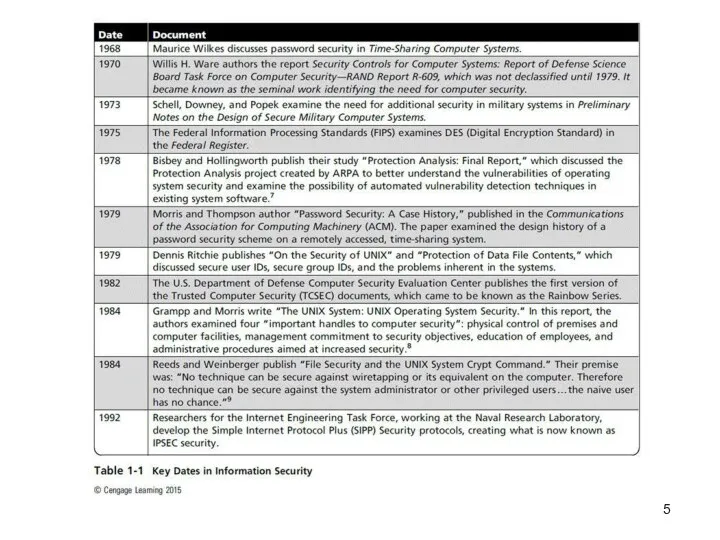
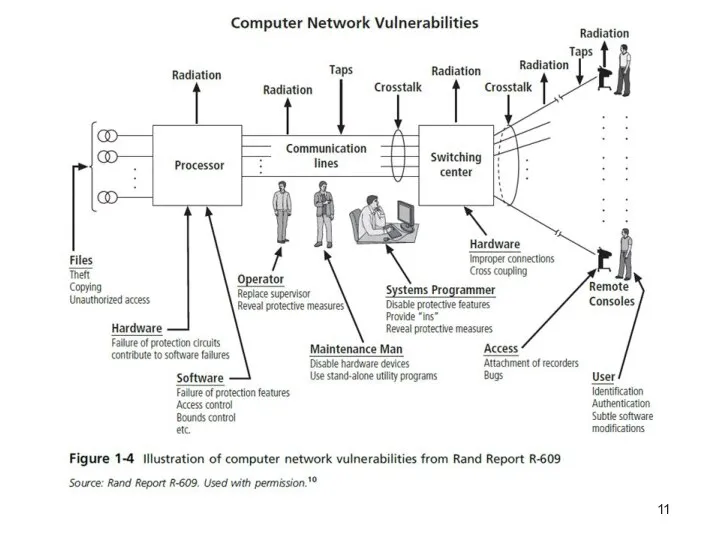
Information security began with Rand Report R-609 (paper

that started the study of computer security and identified the role of management and policy issues in it).
The scope of computer security grew from physical security to include:
Securing the data
Limiting random and unauthorized access to data
Involving personnel from multiple levels of the organization in information security
Слайд 12MULTICS
Early focus of computer security research centered on a system called Multiplexed
Information and Computing Service (MULTICS).
First operating system was created with security integrated into core functions.
Mainframe, time-sharing OS was developed in the mid-1960s by General Electric (GE), Bell Labs, and Massachusetts Institute of Technology (MIT).
Several MULTICS key players created UNIX.
Primary purpose of UNIX was text processing.
Late 1970s: The microprocessor expanded computing capabilities and security threats.
Слайд 13The 1990s
Networks of computers became more common, as did the need to
connect them to each other.
Internet became the first global network of networks.
Initially, network connections were based on de facto standards.
In early Internet deployments, security was treated as a low priority.
In 1993, DEFCON conference was established for those interested in information security.
Слайд 142000 to Present
The Internet brings millions of unsecured computer networks into continuous

communication with each other.
The ability to secure a computer’s data was influenced by the security of every computer to which it is connected.
Growing threat of cyber attacks has increased the awareness of need for improved security.
Nation-states engaging in information warfare
Слайд 15What Is Security?
“A state of being secure and free from danger or

harm; the actions taken to make someone or something secure.”
A successful organization should have multiple layers of security in place to protect:
Operations
Physical infrastructure
People
Functions
Communications
Information
Слайд 16What is Security? (cont’d)
The protection of information and its critical elements, including

systems and hardware that use, store, and transmit that information
Includes information security management, data security, and network security
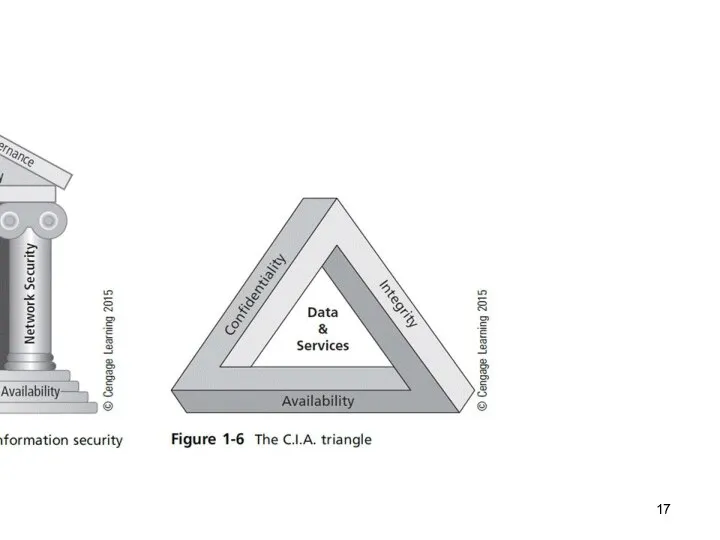
C.I.A. triangle
Is a standard based on confidentiality, integrity, and availability, now viewed as inadequate.
Expanded model consists of a list of critical characteristics of information.
Слайд 18Key Information Security Concepts
A computer can be the subject of an attack

and/or the object of an attack.
When the subject of an attack, the computer is used as an active tool to conduct attack.
When the object of an attack, the computer is the entity being attacked.
Слайд 19Critical Characteristics of Information
The value of information comes from the characteristics it
possesses:
Availability
Accuracy
Authenticity
Confidentiality
Integrity
Utility
Possession
Слайд 20Components of an Information System
Information system (IS) is the entire set of

people, procedures, and technology that enable business to use information.
Software
Hardware
Data
People
Procedures
Networks
Слайд 21Balancing Information Security and Access
Impossible to obtain perfect information security—it is a

process, not a goal.
Security should be considered a balance between protection and availability.
To achieve balance, the level of security must allow reasonable access, yet protect against threats.
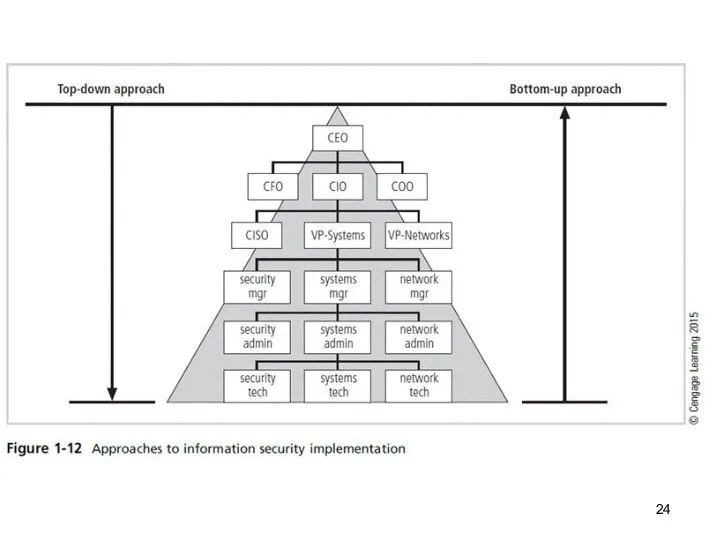
Слайд 22Approaches to Information Security Implementation: Bottom-Up Approach
Grassroots effort: Systems administrators attempt to

improve security of their systems.
Key advantage: technical expertise of individual administrators
Seldom works, as it lacks a number of critical features:
Participant support
Organizational staying power
Слайд 23Approaches to Information Security Implementation: Top-Down Approach
Initiated by upper management
Issue policy, procedures,

and processes
Dictate goals and expected outcomes of project
Determine accountability for each required action
The most successful type of top-down approach also involves a formal development strategy referred to as systems development life cycle.
Слайд 25Security Professionals and the Organization
Wide range of professionals are required to support

a diverse information security program.
Senior management is the key component.
Additional administrative support and technical expertise are required to implement details of IS program.
Слайд 26Senior Management
Chief information officer (CIO)
Senior technology officer
Primarily responsible for advising the

senior executives on strategic planning
Chief information security officer (CISO)
Has primary responsibility for assessment, management, and implementation of IS in the organization
Usually reports directly to the CIO
Слайд 27Information Security Project Team
A small functional team of people who are

experienced in one or multiple facets of required technical and nontechnical areas:
Champion
Team leader
Security policy developers
Risk assessment specialists
Security professionals
Systems administrators
End users
Слайд 28Data Responsibilities
Data owners: senior management responsible for the security and use of

a particular set of information
Data custodian: responsible for information and systems that process, transmit, and store it
Data users: individuals with an information security role
Слайд 29Communities of Interest
Group of individuals united by similar interests/values within an organization
Information

security management and professionals
Information technology management and professionals
Organizational management and professionals
Слайд 30Information Security: Is It an Art or a Science?
Implementation of information security

is often described as a combination of art and science.
“Security artisan” idea: based on the way individuals perceive system technologists and their abilities
Слайд 31Security as Art
No hard and fast rules nor many universally accepted complete

solutions
No manual for implementing security through entire system
Слайд 32Security as Science
Dealing with technology designed for rigorous performance levels
Specific conditions cause

virtually all actions in computer systems.
Almost every fault, security hole, and systems malfunction is a result of interaction of specific hardware and software.
If developers had sufficient time, they could resolve and eliminate faults.
Слайд 33Security as a Social Science
Social science examines the behavior of individuals interacting

with systems.
Security begins and ends with the people that interact with the system, intentionally or otherwise.
Security administrators can greatly reduce the levels of risk caused by end users and create more acceptable and supportable security profiles.
Слайд 34Summary
Information security is a “well-informed sense of assurance that the information risks

and controls are in balance.”
Computer security began immediately after the first mainframes were developed.
Successful organizations have multiple layers of security in place: physical, personal, operations, communications, network, and information.
Слайд 35Summary (cont’d)
Security should be considered a balance between protection and availability.
Information security

must be managed similar to any major system implemented in an organization. Implementation of information security is often described as a combination of art and science.






























 ОГУ «Региональный центр развития образования» Отдел сопровождения проектов
ОГУ «Региональный центр развития образования» Отдел сопровождения проектов Работа выполнена в рамках проекта «Повышение квалификаций различных категорий работников образования и формирование у них базов
Работа выполнена в рамках проекта «Повышение квалификаций различных категорий работников образования и формирование у них базов Как и где производится материал Tyvek® ?
Как и где производится материал Tyvek® ? Солнечная система 11 класс
Солнечная система 11 класс Арьергард - агенство бизнеса
Арьергард - агенство бизнеса Презентация на тему Современный урок в начальной школе в условиях ФГОС
Презентация на тему Современный урок в начальной школе в условиях ФГОС  Java Virtual Machine(Obfuscation and Java)
Java Virtual Machine(Obfuscation and Java) Конституционно правовые нормы Великобритании
Конституционно правовые нормы Великобритании Методы изучения генетики человека
Методы изучения генетики человека Комплект украшений в древнеславянском стиле
Комплект украшений в древнеславянском стиле Презентация на тему Феодализм
Презентация на тему Феодализм Одномаршевая деревянная лестница с балюстрадой
Одномаршевая деревянная лестница с балюстрадой London
London Презентация на тему Что изучает физика
Презентация на тему Что изучает физика Пересечение линии и поверхности
Пересечение линии и поверхности Виктор Робертович Цой
Виктор Робертович Цой Трансформатор (от лат.transformo - преобразую)
Трансформатор (от лат.transformo - преобразую) Брак, условия его заключения
Брак, условия его заключения Платформа Microsoft. NET
Платформа Microsoft. NET  Типология моделей управления международной деятельностью
Типология моделей управления международной деятельностью Русский язык3 класс
Русский язык3 класс Неделя зимних игр и забав
Неделя зимних игр и забав Анализ активности студентов в социальных сетях
Анализ активности студентов в социальных сетях Презентация по английскому Great Britain: a Country of Traditions
Презентация по английскому Great Britain: a Country of Traditions Курс подготовки вторичной продажи
Курс подготовки вторичной продажи Павлово-Посадские платки
Павлово-Посадские платки Оставить след или наследить
Оставить след или наследить Причины трагедии Ларисы Огудаловой. Ученики 10 «Б» класса:Завалова К., Илясова И., Попова Е.,Попов И.
Причины трагедии Ларисы Огудаловой. Ученики 10 «Б» класса:Завалова К., Илясова И., Попова Е.,Попов И.