Содержание
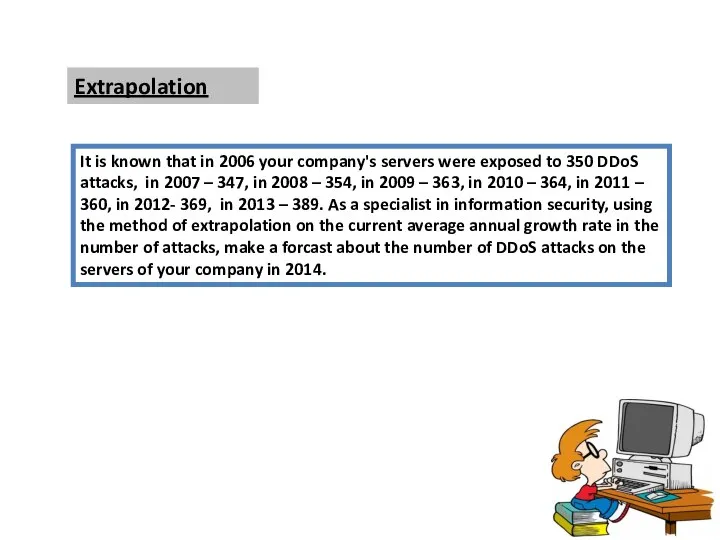
- 2. Extrapolation It is known that in 2006 your company's servers were exposed to 350 DDoS attacks,
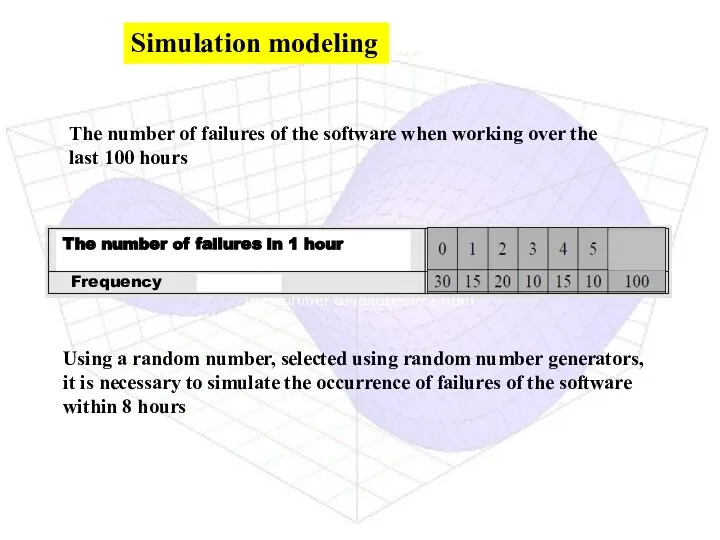
- 3. the number of failures in 1 hour The number of failures of the software when working
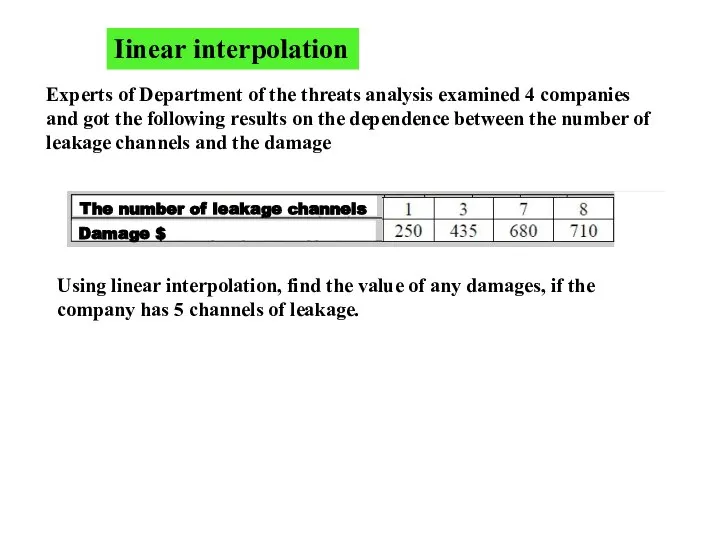
- 4. Iinear interpolation Experts of Department of the threats analysis examined 4 companies and got the following
- 5. EXPONENTIAL SMOOTHING The number of confidential information leakage from the public authorities of the region for
- 6. EVALUATION OF THE FORECAST RELIABILITY You must provide the CEO report on the reliability of forecasts
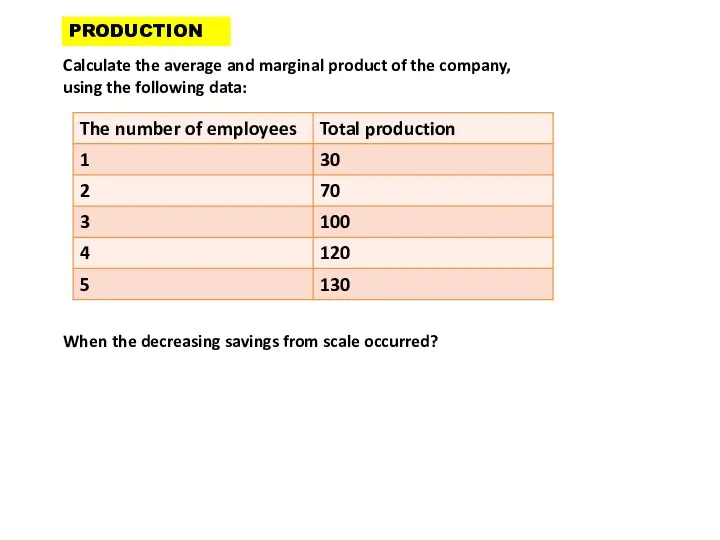
- 7. Calculate the average and marginal product of the company, using the following data: When the decreasing
- 9. Скачать презентацию


 Производный спрос. Предложение труда для отдельной фирмы. Заработная плата в экономической теории и практике
Производный спрос. Предложение труда для отдельной фирмы. Заработная плата в экономической теории и практике Теория экономического роста
Теория экономического роста Краснодар
Краснодар Организационный менеджмент
Организационный менеджмент Интервью для Global Answer
Интервью для Global Answer Типы экономических систем. Рынок
Типы экономических систем. Рынок Бизнес в России
Бизнес в России Анализ наилучших практик прогнозирования банкротства с целью выявления инвестиционной привлекательности предприятий НГК
Анализ наилучших практик прогнозирования банкротства с целью выявления инвестиционной привлекательности предприятий НГК Рынок земли и природных ресурсов
Рынок земли и природных ресурсов Концепция устойчивого развития
Концепция устойчивого развития Теория отраслевых рынков(ТОР) (Лекция 3 )
Теория отраслевых рынков(ТОР) (Лекция 3 ) Задания на сравнение (с выбором ответа). Повторение понятий раздела Экономика
Задания на сравнение (с выбором ответа). Повторение понятий раздела Экономика Развитие рынка труда в инновационной экономике
Развитие рынка труда в инновационной экономике Новая жизнь старых вещей
Новая жизнь старых вещей Личные финансы
Личные финансы Товарная номенклатура внешнеэкономической деятельности ЕАЭС. Тема 6
Товарная номенклатура внешнеэкономической деятельности ЕАЭС. Тема 6 Производственная практика №2
Производственная практика №2 Неокейнсианская кривая Филлипса
Неокейнсианская кривая Филлипса Микроэкономика
Микроэкономика Издержи и прибыль коммерческого банка.
Издержи и прибыль коммерческого банка. Денежные доходы
Денежные доходы Модели экономических систем
Модели экономических систем Бережливое производство
Бережливое производство Хозяйственный механизм торговли и его основные элементы
Хозяйственный механизм торговли и его основные элементы Компьютеризированные пакеты для синтеза и анализа
Компьютеризированные пакеты для синтеза и анализа Метод морфологического анализа
Метод морфологического анализа Концепция всероссийского форума развития сельских территорий Деревня – душа России
Концепция всероссийского форума развития сельских территорий Деревня – душа России Аналіз каналів розподілу. Ірландія
Аналіз каналів розподілу. Ірландія